Добрый день, коллеги.
Столкнулся с непонятными синими экранами (BSOD)
на Windows Server 2003 R2 Enterprise Edition Service Pack 2.
Сервер Supermicro на Xeon E5620 , память 24 Гб .
Около 20 пользователей заходят на сервер только через терминал RDP,
работают с программой 1С 7.7 , пользуются интернетом,
программой Microsoft Office 2003 SP3, распчатывают на принтере.
Примерно один раз месяц(или чаще) сервер падает
в логах ошибка:
Причина непредвиденного завершения работы данного компьютера, предоставленная пользователем MYSEVER1Администратор: Отказ системы: Ошибка STOP
Код причины: 0x805000f
Код ошибки:
Строка проверки: 0x0000008e (0xc0000005, 0xbf8b421b, 0x99e0e9b4, 0x00000000)
Комментарий: 0x0000008e (0xc0000005, 0xbf8b421b, 0x99e0e9b4, 0x00000000)
Я проанализировал четыре минидампа(из C:WINDOWSMinidump) четырёх последних падений с помощью скрипта kdfe.cmd ,
причину и код ошибки показал для всех минидампов одну и ту же:
Crash date: Fri Feb 27 14:41:24.781 2015 (GMT+3)
Stop error code: 0x8E
Probably caused by: win32k.sys ( win32kLockObjectAssignment+a )
А также пранализировал два дампа памяти ядра (C:WINDOWSMEMORY.DMP) с помощью того же скрипта kdfe.cmd
результат одинаковый для этих двух дампов:
Crash date: Mon Nov 18 15:19:36.453 2013 (GMT+3)
Stop error code: 0x8E
Process name: AcroRd32.exe
Probably caused by: win32k.sys ( win32kLockObjectAssignment+a )
Здесь упоминается файл AcroRd32.exe от установленного Adobe Reader XI он может быть причиной такого падения ?
Также анализировал с помощью программы BlueScreenView,
она пометила как проблемные два файла :
win32k.sys
ntkrnlpa.exe
Просьба к коллегам помочь найти причну падения или подсказать направление дальнейшего анализа сбоя.
Минидампы выложил по адресу:
https://onedrive.live.com/redir?resid=8B1382BCC3B51862!107&authkey=!ACqcli9GyllP9nc&ithint=folder%2cdmp
Если нужны полные дампы тоже могу выложить.
BUG #: 41219 (Content Maintenance)
Symptoms
You may experience one or more of the following symptoms on a Microsoft Windows Server 2003-based, Microsoft Windows XP-based, or Microsoft Windows 2000-based computer:
-
The computer automatically restarts.
-
After you log on, you receive the following error message:
Microsoft Windows
The system has recovered from a serious error.
A log of this error has been created.
Please tell Microsoft about this problem.
We have created an error report that you can send to help us improve Microsoft Windows. We will treat this report as confidential and anonymous.
To see what data this error report contains, click here.To see what the error report contains, click click here. When you click the click here link at the bottom of the message box, you will see error signature information that is similar to one of the following data samples.
Data sample 1BCCode : 00000050 BCP1 : f8655000 BCP2 : 00000001 BCP3 : fc7cc465
BCP4 : 00000000 OSVer : 5_1_2600 SP : 0_0 Product : 256_1 Data sample 2BCCode : 0000008e BCP1 : c0000005 BCP2 : 00000120 BCP3 : fd28eaa4
BCP4 : 00000000 OSVer : 5_1_2600 SP : 0_0 Product : 256_1 -
You receive one of the following «Stop» error messages.
Message 1
A problem has been detected and Windows has been shut down to prevent damage to your computer…
Technical information:STOP: 0x00000050 (0xf8655000, 0x00000001, 0xfc7cc465, 0x00000000)
PAGE_FAULT_IN_NONPAGED_AREA (50)
Message 2
A problem has been detected and Windows has been shut down to prevent damage to your computer…
Technical information:STOP: 0x0000008e (0xc0000005, 0x00000120, 0xfd28eaa4, 0x00000000)
KERNEL_MODE_EXCEPTION_NOT_HANDLED_M (1000008e)
-
Error messages that are similar to the following are logged in the System event log:
Date:
date
Source: System
Error Time:
time
Category: (102)
Type: Error
Event ID: 1003
User: N/A
Computer:
COMPUTER
Description: Error code 00000050, parameter1 f8655000, parameter2 00000001, parameter3 fc7cc465, parameter4 00000000. For more information, see Help and Support Center at http://support.microsoft.com. Data: 0000: 53 79 73 74 65 6d 20 45 System E 0008: 72 72 6f 72 20 20 45 72 rror Er 0010: 72 6f 72 20 63 6f 64 65 ror code 0018: 20 30 30 30 30 30 30 35 0000050 0020: 30 20 20 50 61 72 61 6d 0 Param 0028: 65 74 65 72 73 20 66 66 eters ff 0030: 66 66 66 66 64 31 2cDate:
date
Source: System
Error Time:
time
Category: (102)
Type: Error
Event ID: 1003
User: N/A
Computer:
COMPUTER
Description: Error code 0000008e, parameter1 c0000005, parameter2 00000120, parameter3 fd28eaa4, parameter4 00000000. For more information, see Help and Support Center at http://support.microsoft.com. Data: 0000: 53 79 73 74 65 6d 20 45 System E 0008: 72 72 6f 72 20 20 45 72 rror Er 0010: 72 6f 72 20 63 6f 64 65 ror code 0018: 20 30 30 30 30 30 30 35 000008e 0020: 30 20 20 50 61 72 61 6d 0 Param 0028: 65 74 65 72 73 20 66 66 eters ff 0030: 66 66 66 66 64 31 2c
Notes
-
The symptoms of a Stop error vary according to your computer’s system failure options.
For more information about how to configure system failure options, click the following article number to view the article in the Microsoft Knowledge Base:
307973 How to configure system failure and recovery options in Windows
-
The four parameters that are inside the parentheses of the Stop error message vary according to the computer’s configuration.
Cause
This problem may occur if the computer is infected with a variant of the HaxDoor virus.
The HaxDoor virus creates a hidden process. Additionally, the virus hides files and registry keys. The executable file name of the HaxDoor virus may vary, but the file name is frequently Mszx23.exe. Many variants of this virus put a driver that is named Vdmt16.sys or Vdnt32.sys on the computer. This driver is used to hide the virus process. The HaxDoor virus variants can restore these files if you delete them.
Resolution
Important This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly. Therefore, make sure that you follow these steps carefully. For added protection, back up the registry before you modify it. Then, you can restore the registry if a problem occurs. For more information about how to back up and restore the registry, click the following article number to view the article in the Microsoft Knowledge Base:
322756 How to back up and restore the registry in Windows
To solve this problem, follow these steps:
-
Print the following Microsoft Knowledge Base article. Use the article as a guide to this procedure.
307654 How to install and use the Recovery Console in Windows XP
-
Click Start, click Run, type regedit, and then click OK.
-
Locate the following registry subkey:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonNotify
-
Locate and delete any entries in the registry subkey that reference «drct16» or «draw32».
For example, you may see entries that are similar to the following:
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonNotifydrct16
HKEY_LOCAL_MACHINESOFTWAREMicrosoftWindows NTCurrentVersionWinlogonNotifydraw32
-
Insert the Windows XP installation CD, and then restart the computer from the CD.
-
At the Welcome to Setup screen, press R (repair) to start the Windows Recovery Console.
-
Select the number that corresponds to the Windows installation that you want to repair. This number is typically 1.
-
If prompted, type the administrator password. If an administrator password does not exist, press ENTER.
-
At the command prompt, move to the C:WindowsSystem32 folder. For example, type cd C:WindowsSystem32.
-
Use the ren (rename) command to rename the following files as shown. Remember to press ENTER after each command. If you see a «File not found» message, move to the next file in the list.ren 1.a3d 1.a3d.bad ren cm.dll cm.dll.bad ren cz.dll cz.dll.bad ren draw32.dll draw32.dll.bad ren drct16.dll drct16.dll.bad ren dt163.dt dt163.dt.bad ren fltr.a3d fltr.a3d.bad ren hm.sys hm.sys.bad ren hz.dll hz.dll.bad ren hz.sys hz.sys.bad ren i.a3d i.a3d.bad ren in.a3d in.a3d.bad ren klo5.sys klo5.sys.bad ren klogini.dll klogini.dll.bad ren memlow.sys memlow.sys.bad ren mszx23.exe mszx23.exe.bad ren p2.ini p2.ini.bad ren ps.a3d ps.a3d.bad ren redir.a3d redir.a3d.bad ren tnfl.a3d tnfl.a3d.bad ren vdmt16.sys vdmt16.sys.bad ren vdnt32.sys vdnt32.sys.bad ren w32tm.exe w32tm.exe.bad ren WD.SYS WD.SYS.bad ren winlow.sys winlow.sys.bad ren wmx.a3d wmx.a3d.bad ren wz.dll wz.dll.bad ren wz.sys wz.sys.bad
If you want to delete these files when you are finished, type del *.bad. -
Remove the Windows XP installation CD, and then type
Exit to restart the computer. -
When the computer restarts, click
Start, click Run, type regedit, and then click
OK. -
Locate and delete the following registry subkeys and any entries that may be present under each subkey. If any registry subkeys from this list are not present, move to the next subkey in the list.
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvdmt16
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesvdnt32
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServiceswinlow
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesmemlowHKEY_LOCAL_MACHINESYSTEMControlSet001Servicesvdmt16
HKEY_LOCAL_MACHINESYSTEMControlSet001Servicesvdnt32
HKEY_LOCAL_MACHINESYSTEMControlSet001Serviceswinlow
HKEY_LOCAL_MACHINESYSTEMControlSet001ServicesmemlowHKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesENUMROOTLEGACY_VDMT16
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesENUMROOTLEGACY_VDNT32
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesENUMROOTLEGACY_WINLOW
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetServicesENUMROOTLEGACY_MEMLOW -
Locate and delete any entries that contain the Mszx23.exe file name under the following registry subkeys:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunServices
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRunServices -
Quit Registry Editor.
-
Make sure that your antivirus and anti-spyware programs are updated with the latest definitions, and then perform a complete system scan.
The following malware has been identified by antivirus vendors.
|
Symantec: |
Backdoor.Haxdoor.D |
|
Trend Micro: |
BKDR_HAXDOOR.BC, BKDR_HAXDOOR.BN, BKDR_HAXDOOR.BA, BKDR_HAXDOOR.AL |
|
PandaLabs: |
HAXDOOR.AW |
|
F-Secure: |
Backdoor.Win32.Haxdoor, Backdoor.Win32.Haxdoor.al |
|
Sophos: |
Troj/Haxdoor-AF, Troj/Haxdoor-CN, Troj/Haxdoor-AE |
|
Kaspersky Lab: |
Backdoor.Win32.Haxdoor.bg |
|
McAfee: |
BackDoor-BAC |
Need more help?
Want more options?
Explore subscription benefits, browse training courses, learn how to secure your device, and more.
Communities help you ask and answer questions, give feedback, and hear from experts with rich knowledge.
STOP error 0x8E on Windows Server 2003 and Endpoint Protection 12.1
calendar_today
Updated On:
Products
Endpoint Protection
Issue/Introduction
- You experience a STOP error 0x8E (KERNEL_MODE_EXCEPTION_NOT_HANDLED) on a physical or virtualized server running a 32-bit version of Windows Server 2003 Service Pack 2 and Symantec Endpoint Protection (SEP) 12.1.
- The address that the exception occurred at (which usually pinpoints the driver/function that caused the problem) points to win32k.sys (Microsoft’s Multi-User Win32 driver).
- Its call to the xxxDestroyThreadInfo function in the context of process csrss.exe (Microsoft’s Client/Server Runtime subsystem) led to the crash.
- When the crash occurs, there is also a locked thread involving a screensaver process (e.g. «vfinalv1.scr»).
- While SYMEVENT is present in the stack, it is in pass-thru mode and only capturing the process termination event as a result of win32k.sys’ function call (the next call in the stack is actually shown to be Nt!TerminateProcess).
- Win32k.sys is dated June 24, 2015. As this version was released on the day Windows Server 2003 reached End-of-Life (EOL) status, Microsoft will not be issuing any further hotfixes.
- The issue is very similar (but not identical) to the ones described below:
- A Windows Server 2003-based computer restarts unexpectedly and you receive a Stop error message during the terminal session logoff process: 0x0000008E KERNEL_MODE_EXCEPTION_NOT_HANDLED
- Blue screen crash with STOP Error 0x8E after installing Symantec Endpoint Protection
Bug Check 0x8E (KERNEL_MODE_EXCEPTION_NOT_HANDLED)
Cause
In this specific scenario, the issue is likely caused by the screensaver.
Resolution
Remove the screensaver and continue to monitor the server for further occurrences.
Feedback
thumb_up
Yes
thumb_down
No
I have a VMware server that was running Windows Standard Edition 2003 on VMware server version 1.0.5. Each time Windows OS starts up it comes to the login screen and as soon as anyone tries to login Windows gives the blue screen of death with the error of 0x0000008e. Inside of the vmware.log file I see this error right as the BSOD happens:
SCSI0: RESET BUS
The server locks up and reboots and the same thing happens. I have upgraded VMware server to version 1.0.10 and the same thing happens. I also upgraded the server to version 2.0.2 and the same thing happens (I can’t use the VMware server console in that version- but that is a separate issue).
If I boot the Server 2003 into safe mode I am able to login just fine.
There is a snapshot a month old that I would rather not use unless I have to.
VMwareVirtualizationWindows Server 2003
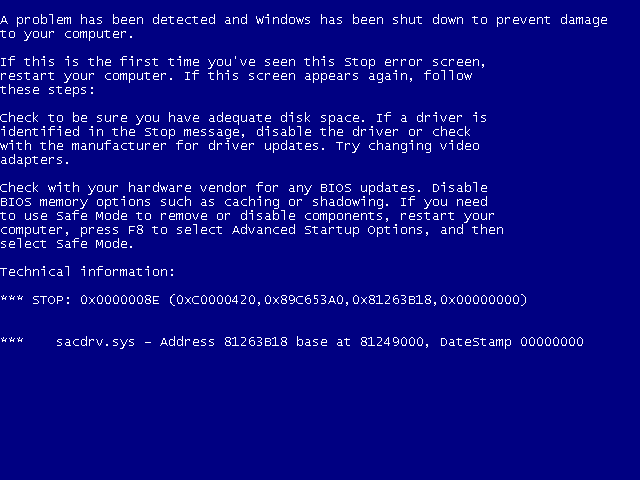
STOP 0×0000008E: KERNEL_MODE_EXCEPTION_NOT_HANDLED
Bsod актуален для следующих систем: Microsoft Windows Server 2003, Microsoft Windows XP или Microsoft Windows 2000.
- Компьютер автоматически перезагружается.
- После входа в систему появляются сообщения об ошибках.
- Появляется сообщение о фатальной ошибке.
Обнаружена ошибка, для предотвращения повреждения компьютера Windows завершит работу.
Техническая информация:
STOP: 0x0000008e (0xc0000005, 0×00000120, 0xfd28eaa4, 0×00000000)
KERNEL_MODE_EXCEPTION_NOT_HANDLED_M (1000008e)
Ошибка может быть вызвана следующим:
- Один или несколько RAM модулей установленных на вашем компьютере не исправны.
Протестируйте оперативную память на ошибки.
- Конфигурация RAM не совместима с Windows.
- Довольно часто такая ошибка наблюдается, когда компьютер заражен одной из разновидностей вируса HaxDoor.
Вирус HaxDoor порождает скрытый процесс. Кроме того, вирус скрывает файлы и разделы реестра. Имя исполняемого файла вируса HaxDoor может быть различным, однако чаще всего он появляется под именем Mszx23.exe. Большинство разновидностей этого вируса устанавливает на компьютер драйвер Vdmt16.sys или Vdnt32.sys. Этот драйвер используется для сокрытия процесса, порождаемого вирусом. Некоторые разновидности вируса HaxDoor могут восстанавливать этот файл после его удаления.
В обязательном порядке обновите свой антивирус и просканируйте компьютер.
