Recently, Chrome has stopped working with my self signed SSL certs, and thinks they’re insecure. When I look at the cert in the DevTools | Security tab, I can see that it says
Subject Alternative Name Missing The certificate for this site does
not contain a Subject Alternative Name extension containing a domain
name or IP address.Certificate Error There are issues with the site’s certificate chain
(net::ERR_CERT_COMMON_NAME_INVALID).
How can I fix this?
jww
96.8k90 gold badges408 silver badges878 bronze badges
asked Apr 27, 2017 at 18:17
Brad ParksBrad Parks
65.9k64 gold badges256 silver badges332 bronze badges
4
To fix this, you need to supply an extra parameter to openssl when you’re creating the cert, basically
-sha256 -extfile v3.ext
where v3.ext is a file like so, with %%DOMAIN%% replaced with the same name you use as your Common Name. More info here and over here. Note that typically you’d set the Common Name and %%DOMAIN%% to the domain you’re trying to generate a cert for. So if it was www.mysupersite.com, then you’d use that for both.
v3.ext
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = %%DOMAIN%%
Note: Scripts that address this issue, and create fully trusted ssl certs for use in Chrome, Safari and from Java clients can be found here
Another note: If all you’re trying to do is stop chrome from throwing errors when viewing a self signed certificate, you can can tell Chrome to ignore all SSL errors for ALL sites by starting it with a special command line option, as detailed here on SuperUser
answered Apr 27, 2017 at 18:17
Brad ParksBrad Parks
65.9k64 gold badges256 silver badges332 bronze badges
13
Following solution worked for me on chrome 65 (ref) —
Create an OpenSSL config file (example: req.cnf)
[req]
distinguished_name = req_distinguished_name
x509_extensions = v3_req
prompt = no
[req_distinguished_name]
C = US
ST = VA
L = SomeCity
O = MyCompany
OU = MyDivision
CN = www.company.com
[v3_req]
keyUsage = critical, digitalSignature, keyAgreement
extendedKeyUsage = serverAuth
subjectAltName = @alt_names
[alt_names]
DNS.1 = www.company.com
DNS.2 = company.com
DNS.3 = company.net
Create the certificate referencing this config file
openssl req -x509 -nodes -days 730 -newkey rsa:2048
-keyout cert.key -out cert.pem -config req.cnf -sha256
answered Apr 6, 2018 at 12:00
7
The Issue
As others have mentioned, the NET::ERR_CERT_COMMON_NAME_INVALID error is occurring because the generated certificate does not include the SAN (subjectAltName) field.
RFC2818 has deprecated falling back to the commonName field since May of 2000. The use of the subjectAltName field has been enforced in Chrome since version 58 (see Chrome 58 deprecations).
OpenSSL accepts x509v3 configuration files to add extended configurations to certificates (see the subjectAltName field for configuration options).
Bash Script
I created a self-signed-tls bash script with straightforward options to make it easy to generate certificate authorities and sign x509 certificates with OpenSSL (valid in Chrome using the subjectAltName field).
The script will guide you through a series of questions to include the necessary information (including the subjectAltName field). You can reference the README.md for more details and options for automation.
Be sure to restart chrome after installing new certificates.
chrome://restart
Other Resources
- The Docker documentation has a great straightforward example for creating a self-signed certificate authority and signing certificates with OpenSSL.
- cfssl is also a very robust tool that is widely used and worth checking out.
- mkcert is a tool written in GoLang. It seems simple to use and great for local development.
answered Sep 15, 2017 at 16:13
LoganLogan
6078 silver badges7 bronze badges
2
Here is a very simple way to create an IP certificate that Chrome will trust.
The ssl.conf file…
[ req ]
default_bits = 4096
distinguished_name = req_distinguished_name
req_extensions = req_ext
prompt = no
[ req_distinguished_name ]
commonName = 192.168.1.10
[ req_ext ]
subjectAltName = IP:192.168.1.10
Where, of course 192.168.1.10 is the local network IP we want Chrome to trust.
Create the certificate:
openssl genrsa -out key1.pem
openssl req -new -key key1.pem -out csr1.pem -config ssl.conf
openssl x509 -req -days 9999 -in csr1.pem -signkey key1.pem -out cert1.pem -extensions req_ext -extfile ssl.conf
rm csr1.pem
On Windows import the certificate into the Trusted Root Certificate Store on all client machines. On Android Phone or Tablet download the certificate to install it. Now Chrome will trust the certificate on windows and Android.
On windows dev box the best place to get openssl.exe is from «c:Program FilesGitusrbinopenssl.exe»
answered Oct 2, 2019 at 22:41
AQuirkyAQuirky
4,5712 gold badges32 silver badges50 bronze badges
1
I simply use the -subj parameter adding the machines ip address. So solved with one command only.
sudo openssl req -x509 -nodes -days 3650 -newkey rsa:2048 -sha256 -subj '/CN=my-domain.com/subjectAltName=DNS.1=192.168.0.222/' -keyout my-domain.key -out my-domain.crt
You can add others attributes like C, ST, L, O, OU, emailAddress to generate certs without being prompted.
answered Jul 26, 2017 at 17:53
LudwigLudwig
3,4822 gold badges20 silver badges24 bronze badges
3
I had so many issues getting self-signed certificates working on macos/Chrome. Finally I found Mkcert, «A simple zero-config tool to make locally trusted development certificates with any names you’d like.» https://github.com/FiloSottile/mkcert
answered Dec 6, 2019 at 0:48
AnthonyAnthony
4255 silver badges8 bronze badges
1
-
Make a copy of your OpenSSL config in your home directory:
cp /System/Library/OpenSSL/openssl.cnf ~/openssl-temp.cnfor on Linux:
cp /etc/ssl/openssl.cnf ~/openssl-temp.cnf -
Add Subject Alternative Name to
openssl-temp.cnf, under[v3_ca]:[ v3_ca ] subjectAltName = DNS:localhostReplace
localhostby the domain for which you want to generate that certificate. -
Generate certificate:
sudo openssl req -x509 -nodes -days 365 -newkey rsa:2048 -config ~/openssl-temp.cnf -keyout /path/to/your.key -out /path/to/your.crt
You can then delete openssl-temp.cnf
answered Jun 10, 2019 at 17:20
Vic SeedoubleyewVic Seedoubleyew
10.7k6 gold badges54 silver badges75 bronze badges
2
I was able to get rid of (net::ERR_CERT_AUTHORITY_INVALID) by changing the DNS.1 value of v3.ext file
[alt_names]
DNS.1 = domainname.com
Change domainname.com with your own domain.
answered May 16, 2017 at 11:51
on MAC
starting from chrome Version 67.0.3396.99 my self-signed certificate stopped to work.
regeneration with all what written here didn’t work.
UPDATE
had a chance to confirm that my approach works today :). If it doesn’t work for you make sure your are using this approach
v3.ext
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = <specify-the-same-common-name-that-you-used-while-generating-csr-in-the-last-step>
$
copied from here
https://ksearch.wordpress.com/2017/08/22/generate-and-import-a-self-signed-ssl-certificate-on-mac-osx-sierra/
END UPDATE
finally was able to see green Secure only when removed my cert from system, and added it to local keychain. (if there is one — drop it first). Not sure if it maters but in my case I downloaded certificate via chrome, and verified that create date is today — so it is the one I’ve just created.
hope it will be helpful for someone spend like a day on it.
never update chrome!
answered Jul 2, 2018 at 20:55
user2932688user2932688
1,53811 silver badges24 bronze badges
Updated June 2021 — Windows 10 — Chrome v91 answer is here
answered Jun 6, 2021 at 3:13
orszaczkyorszaczky
12.9k8 gold badges47 silver badges54 bronze badges
If you want to run your server localhost, you need to setup CN = localhost and DNS.1 = localhost.
[req]
default_bits = 2048
default_md = sha256
distinguished_name = req_distinguished_name
prompt = no
prompt = no
x509_extensions = v3_req
[req_distinguished_name]
C = BR
CN = localhost
emailAddress=contact@example.com
L = Sao Paulo
O = example.com
OU = example.com
ST = Sao Paulo
[v3_req]
authorityKeyIdentifier = keyid, issuer
basicConstraints = CA:FALSE
extendedKeyUsage = serverAuth
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = localhost
answered Aug 9, 2020 at 4:06
For an Atlassian application to be able to successfully establish SSL connection with LDAP, the certificate for the directory must be trusted. Typically, this certificate is imported into the Java stores for trusted certificates, in a file called a keystore. The default keystore file is called cacerts and it lives in the jrelibsecurity sub-directory of your Java installation.
Errors
-
The connection to the LDAP fails with the an error «handling exception: javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No subject alternative DNS name matching DOMAIN.COM found.»
nested exception is javax.naming.CommunicationException: DOMAIN.COM:636 [Root exception is javax.net.ssl.SSLHandshakeException: java.security.cert.CertificateException: No subject alternative DNS name matching DOMAIN.COM found.]=Cause 1
The LDAP server uses a different certificate compared to what is imported into the Java environment.
-
Although this is rare, the LDAP server uses a different server certificate to communicate.
-
it is possible that the LDAP server, either has multiple server certificates
-
OR the certificate imported in Java, is no longer present on the LDAP server.
-
Cause 2
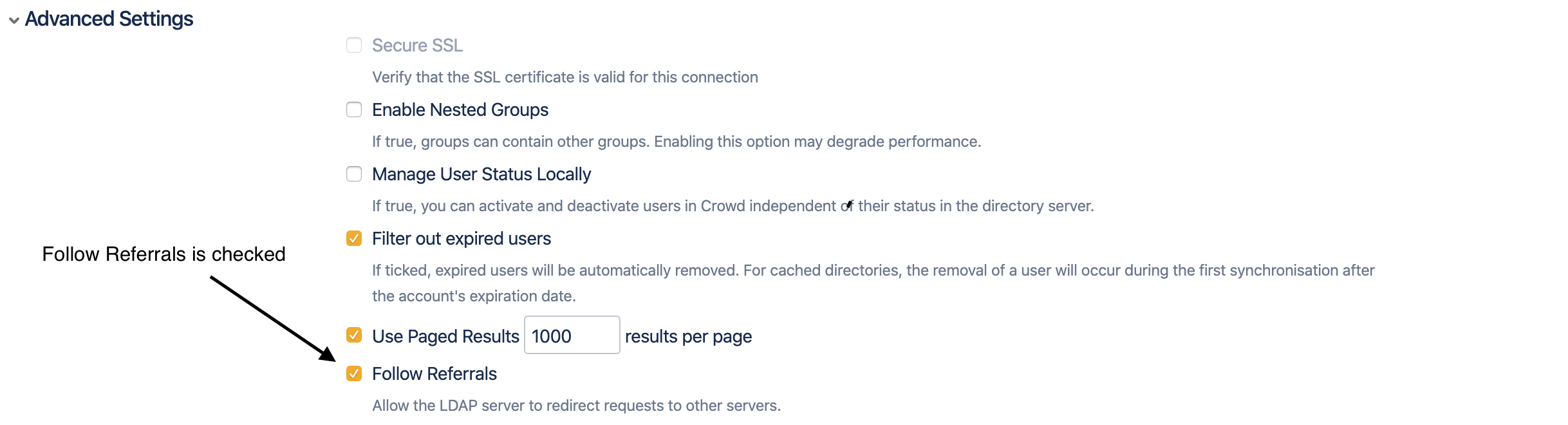
Follow referral is enabled.
By default, «Follow Referrals» is turned on.
Certificate requirement
-
Subject name of the certificate should match the host name of the Directory server mentioned in the User Directory configuration page.
-
The certificate should contain the LDAP server name.
-
The certificate should be imported into JAVA runtime environment. Below command can be used.
-
Please replace «server-certificate.crt» with actual certificate name.
1keytool -importcert -keystore .jrelibsecuritycacerts -file server-certificate.crt
-
-
Jira will need to be restarted to identify the newly imported certificate.
The article Configuring an SSL connection to Active Directory discusses the steps in detail.
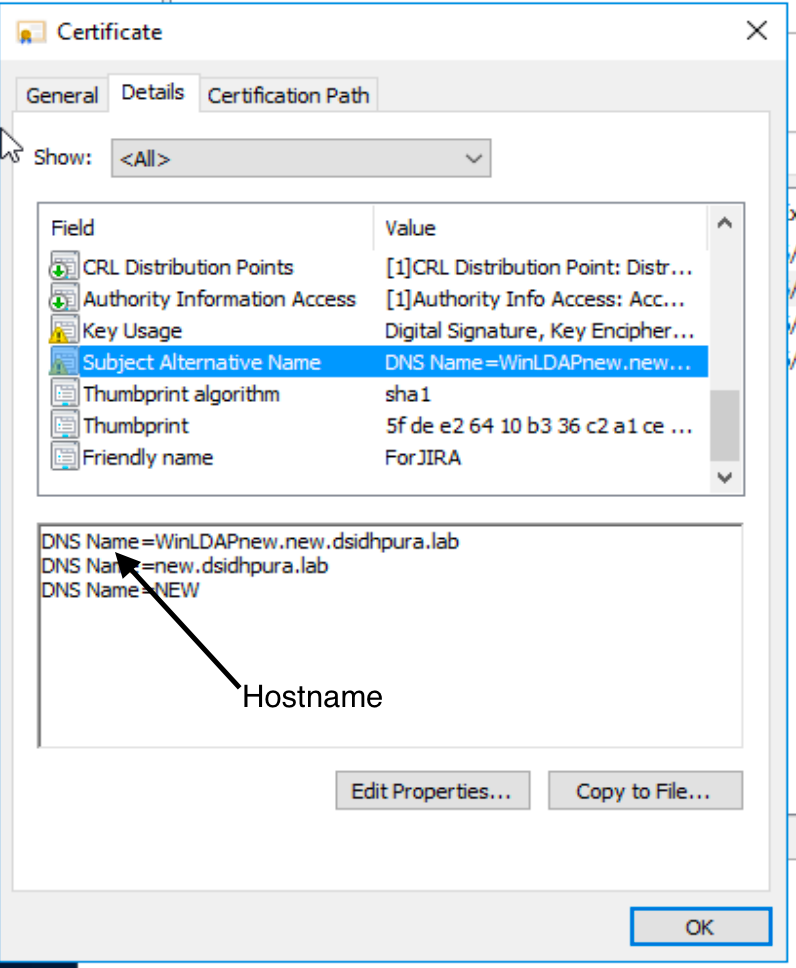
Subject Name from the certificate
Hostname from the User Directory configuration
Solution 1
-
To get certificate used by the LDAP server, enable to the following debug logging.
-
Once the certificate used LDAP server is identified, import the certificate into the Java environment.
Enable Logging
-
Add the following to setenv.sh in JVM_SUPPORT_RECOMMENDED_ARGS
-
«-Djavax.net.debug=all»
-
Restart Jira.
-
Check the catalina log file for SSL handshake information
-
Snippet from the logs
-
With the above logging enabled, the catalina.out, would log the certificate being received for the connection.
1 2 3 4 5 6 7 8 9 10 11 12 chain [0] = [ [ Version: V3 Subject: CN=WinLDAPnew.new.dsidhpura.lab Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11 Key: Sun RSA public key, 2048 bits public exponent: 65537 Validity: [From: Tue May 12 19:07:25 IST 2020, To: Wed May 12 19:07:25 IST 2021] Issuer: CN=new-WINLDAPNEW-CA, DC=new, DC=dsidhpura, DC=lab SerialNumber: [ 12000000 05123d75 38577613 fb000000 000005]- Below is the certificate in the Java environment
1 2 3 4 5 6 7 Alias name: ldaps Creation date: 12 May, 2020 Entry type: trustedCertEntry Owner: Issuer: CN=new-WINLDAPNEW-CA, DC=new, DC=dsidhpura, DC=lab Serial number: 120000000454d67e7f8f53f1c1000000000004-
Notice the serial numbers are different between the certificate received for communication and certificate imported into Java.
-
LDAP server certificate SerialNumber: 1200000005123d7538577613fb000000000005
-
Java environment certificate Serial number: 120000000454d67e7f8f53f1c1000000000004
-
Solution 2
With follow referral enabled.
- The DNS name resolution for the domain name should resolve to LDAP server, for which certificate is imported in the Java environment.
- Using the screenshots from this article, the Domain name would be new.dsidhpura.lab.
- This DNS name should resolve the LDAP server for which the certificate is imported in the Java environment.
Пытаюсь собрать и установить PHP7 на Ubuntu 14.04
Собрать получилось, а вот после make install выпадает ошибка:
Installing PEAR environment: /root/php7/usr/lib/php/
--2015-12-04 11:34:28-- https://pear.php.net/install-pear-nozlib.phar
Resolving pear.php.net (pear.php.net)... 5.35.241.22
Connecting to pear.php.net (pear.php.net)|5.35.241.22|:443... connected.
ERROR: no certificate subject alternative name matches
requested host name 'pear.php.net'.
To connect to pear.php.net insecurely, use `--no-check-certificate'.
make: *** [install-pear] Error 5-
Вопрос заданболее трёх лет назад
-
1971 просмотр
Makefile 443 строка, можно изменить
PEAR_INSTALLER_URL = https://pear.php.net/install-pear-nozlib.pharна
PEAR_INSTALLER_URL = http://pear.php.net/install-pear-nozlib.pharПригласить эксперта
Ощущение что корневые сертификаты у вас протухли, обновить систему всю
Чего все побежали ставить 7?
--without-pear
Я пробовал фиксить Makefile, но тогда прилетает 404.
-
Показать ещё
Загружается…
22 мая 2023, в 18:02
120000 руб./за проект
13 июн. 2023, в 18:39
5000 руб./за проект
13 июн. 2023, в 18:22
180000 руб./за проект
Минуточку внимания
С недавних пор Chrome стал ругаться на самоподписанные сертификаты, выдавая ошибку: «Subject Alternative Names is missing». Когда мы генерируем стандартный запрос с использованием команды openssl
# openssl req -new -sha256 -nodes -out domain.csr -newkey rsa:2048 -keyout domain.key
нет возможности задать эти альтернативные имена, а именно по ним браузер и проверят достоверность ресурса. Поэтому что бы такой ошибки не возникало сгенерируем расширенный запрос, выглядит он примерно так:
# openssl req -new -sha256 -nodes -out domain.csr -newkey rsa:2048 -keyout domain.key -config <( > cat <<-EOF > [req] > default_bits = 2048 > prompt = no > default_md = sha256 > req_extensions = req_ext > distinguished_name = dn > > [ dn ] > C=RU > ST=Moscow > L=Moscow > O=Company > OU=IT > [email protected] > CN = website.company.ru > > [ req_ext ] > subjectAltName = @alt_names > > [ alt_names ] > DNS.1 = website.company.ru > DNS.2 = www.website.company.ru > EOF > )
Сгенерированный таким образом запрос так же нормально переваривает MS CA, который в итоге выпускает правильный сертификат с альтернативными именами.
The newest version of Google Chrome 58 requires that certificates specify the hostname(s) to which they apply in the SubjectAltName field. The error, Security certificate does not specify subject alternative names trigger if the certificate does not have the correct SubjectAlternativeName extension.
As part of our Server Management Services, we assist our customers with several such errors.
Today, let us see an effective way to fix this error.
Subject Alternative Name
The Subject Alternative Name field helps to specify additional hostnames to be protected by a single SSL Certificate.
This extension was a part of the X509 certificate standard before 1999. However, it wasn’t in use until the launch of Microsoft Exchange Server 2007.
Now Subject Alternative Names are widely in use for environments or platforms that need to secure multiple sites across different domains/subdomains.
We can find Subject Alternative Names in the address bar. Click the padlock in the browser to examine the SSL Certificate. In the certificate details, we will find a Subject Alternative Name extension.
What to do with Subject Alternative Names?
- Secure Host Names on Different Base Domains in One SSL Certificate:
A Wildcard Certificate can protect all first-level subdomains on an entire domain. Whereas Subject Alternative Names can protect both www.example.com and www.example.net.
- Virtual Host Multiple SSL Sites on a Single IP Address:
Hosting multiple SSL-enabled sites on a single server typically requires a unique IP address per site. However, a Multi-Domain (SAN) Certificate with Subject Alternative Names solves this problem.
- Greatly Simplify Your Server’s SSL Configuration:
A Multi-Domain (SAN) Certificate saves us the hassle and time involved in configuring multiple IP addresses on the server, binding each IP address to a different certificate, and trying to piece it all together.
Solution for Security certificate does not specify subject alternative names
-
In order to solve the SubjectAltNames issue, we edit the file:
C:wamp64binapacheapache2.4.27confopenssl.cnf
Under [ Req ] section
uncommented: req_extensions = v3_req
Under [ v3_req ] section
Added: extendedKeyUsage = serverAuth
Added: subjectAltName = @alt_names
Under [ v3_ca ] section
Added: subjectAltName = @alt_names
Added new section [ alt_names ] at the bottom of the file
[ alt_names ]
DNS.1 = %domain%Then we reload the new certificate into the Trusted Root Certification Authorities Store.
-
Supply an extra parameter to openssl when we create the cert,
-sha256 -extfile v3.extHere, v3.ext is a file with %%DOMAIN%% replaced with the same name we use as the Common Name.
Typically we will set the Common Name and %%DOMAIN%% to the domain we are trying to generate a cert for. So if it was www.example.com, then we have to use that for both.
v3.ext
authorityKeyIdentifier=keyid,issuer
basicConstraints=CA:FALSE
keyUsage = digitalSignature, nonRepudiation, keyEncipherment, dataEncipherment
subjectAltName = @alt_names
[alt_names]
DNS.1 = %%DOMAIN%%-
Regenerate the certificate to include a Subject Alternative Name.
To fix the error for Chrome users, we have to regenerate the certificate. To do that we can use the Certificates MMC when we have an internal Certification Authority (CA).
- From the webserver, open MMC and add the Certificates snap-in, managing the Computer account.
- Then expand Certificates (Local Computer) > Personal > (right-click) Certificates > All Tasks > Request New Certificate.
- Then choose Active Directory Enrollment Policy to use the existing internal CA.
- Select the Web Server certificate template and click the link below it to enter more information.
- Add the Common Name for the Subject Name, and the DNS name for the Alternative Name.
- Enter a Friendly Name on the General tab.
- Optionally, make the private key exportable on the Private Key tab and click OK.
- Then click Enroll to generate the new cert from the CA and install it on the webserver.
- The certificate will be installed. Click Details to view the new certificate.
- On the Details tab, we see the Subject Alternative Name is on the new cert.
Now we configure IIS to use the new certificate or reconfigure Exchange web services using the Enable-ExchangeCertificate cmdlet.
-
Disable the checking of SubjectAlternativeName in Chrome.
This is a work-around that will not function beyond version 65 of Google Chrome. Our Support Techs recommend using this method as a temporary fix.
By adding the following setting, Chrome can force to allow certificates that are missing the SubjectAlternativeName extension:
Windows registry (REG_DWORD):
SoftwarePoliciesGoogleChromeEnableCommonNameFallbackForLocalAnchorsWe can add a registry key to Windows by entering the following at the Command Prompt:
reg add HKLMSoftwarePoliciesGoogleChrome /v EnableCommonNameFallbackForLocalAnchors /t REG_DWORD /d 1When we enable this setting, Google Chrome will use the Common Name of a server certificate to match a hostname if the certificate is missing a SubjectAlternativeName extension, as long as it successfully validates and chains to a locally-installed CA certificate.
[The error continues to prevail? We can help you]
Conclusion
To conclude, the error, Security certificate does not specify subject alternative names trigger if the certificate does not have the correct SubjectAlternativeName extension. Today we saw how our Support Techs fix this.
PREVENT YOUR SERVER FROM CRASHING!
Never again lose customers to poor server speed! Let us help you.
Our server experts will monitor & maintain your server 24/7 so that it remains lightning fast and secure.
GET STARTED
var google_conversion_label = «owonCMyG5nEQ0aD71QM»;