I am doing a tutorial on Mutual SSL authentication using tomcat. I tried google and stackoverflow for the answer but I haven’t been lucky so far. I have done the following steps
1. Generated a self signed Certificate using the command as…
keytool -genkey -v -alias tomcat -keyalg RSA -validity 3650 -keystore D:server.keystore -dname "CN=KeshavServer,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN" -storepass server123 -keypass server123
Result(DOS Output):
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) with a validity of 3,650 days for: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
New certificate (self-signed):
[
[
Version: V3
Subject: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
modulus: 169745031109692228700332160907879660712549791227819060217679327134557
60724387920644418620368961814809125561438164385172820012631533276651192871536066
44484789458740611952365817466495640787815691991239210085729312562284526930712191
68874744017392521167643053301439564836240073082909781032758910760996909343586608
99178037089977353808963798076122662239868847716719923568980681140353282369676681
53737103284233931190726847482006084262000642602659963850552605206369455374224663
42718874198088754429094645464054866254482989193982685337964154043630072713972109
68332098433075932439269617793403644275259520886009675985568022246951
public exponent: 65537
Validity: [From: Mon Aug 12 12:16:13 IST 2013,
To: Thu Aug 10 12:16:13 IST 2023]
Issuer: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
SerialNumber: [ 713ab315]
Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: D6 0E 1F 23 B2 11 92 D2 19 7B C9 AA 19 EF 82 EB ...#............
0010: A6 0C 35 57 ..5W
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 4C 36 84 CD FE 2C 11 4B 88 C1 AE 3A 7A 6A A1 C4 L6...,.K...:zj..
0010: 2C 6E F5 73 33 64 57 06 04 7F AC 1B D6 CA BF E0 ,n.s3dW.........
0020: D2 88 09 A9 B8 4D 70 EE 73 6E 02 45 33 83 42 1E .....Mp.sn.E3.B.
0030: C4 8E 67 F3 51 D7 9C 53 08 CD C7 EA 4B BC 27 0D ..g.Q..S....K.'.
0040: 17 36 9B 12 4A F7 F7 23 0E C2 51 0A 18 06 B5 80 .6..J..#..Q.....
0050: 1C 44 17 0D 99 14 6E 27 40 30 56 DF 31 D9 CC 15 .D....n'@0V.1...
0060: 46 7C 72 C2 54 CE 2E 2B 41 94 19 54 9B 3A F7 85 F.r.T..+A..T.:..
0070: 96 CE 5F 80 C5 A5 02 AE 09 17 A5 C3 E4 A6 BB 63 .._............c
0080: A3 EF 99 4F BC A4 FF 4F 2B BD 46 E5 BE 57 C7 BD ...O...O+.F..W..
0090: 85 54 F9 B1 5F 01 18 07 9F DD 02 99 91 B3 35 FB .T.._.........5.
00A0: 62 74 2A 0A 37 8A 9B 0D E8 BF B4 24 CE 24 12 8A bt*.7......$.$..
00B0: 22 68 39 90 BD 02 24 A4 E9 9B 52 E1 AA 76 1D 16 "h9...$...R..v..
00C0: 91 2A 60 49 D3 F6 91 0A 01 E4 98 1B BB EB B7 E5 .*`I............
00D0: E3 DF 39 B8 73 02 C3 1D EA 95 D1 95 A7 27 53 FC ..9.s........'S.
00E0: 28 2B 21 50 90 BF 48 9A 25 92 28 D8 EC FE 82 60 (+!P..H.%.(....`
00F0: B9 21 28 B3 1A 37 B6 79 17 8B FF 4C 0B C1 6D 0C .!(..7.y...L..m.
]
[Storing D:server.keystore]
2. Generated the developer key by using the command as…
keytool -genkey -v -alias developerKey -keyalg RSA -storetype PKCS12 -keystore dev.p12 -dname "CN=KeshavClient,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN" -storepass dev123 -keypass dev123
Result(DOS Output):
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) wi
th a validity of 90 days
for: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
New certificate (self-signed):
[
[
Version: V3
Subject: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
modulus: 257861330490904259854513552509935970316490717846991127699603148980652
01114722960469328519589253139525292368465436006354129813882061510118729695295380
60706390500779076802188937858019079525575493711793923541823056735274180328061957
20693618061100873813154701306998418961615717804323475393466678818363454317730604
32071710089666113885067366725913386597296681138020057906688646996872449490785655
01898351843152376966821908896570275550705585694195185294854938453556896208850780
54361881798687601045808741784626686357148783050499722574071065943861302398542177
91929018282855348848062666985932392623629290470810910913665654471519
public exponent: 65537
Validity: [From: Mon Aug 12 12:16:26 IST 2013,
To: Sun Nov 10 12:16:26 IST 2013]
Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
SerialNumber: [ 503c03cf]
Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(..
0010: 34 63 F2 4C 4c.L
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 91 79 CF CC 0F FD CA BB 2A 60 5E 87 8F 2F 6D B6 .y......*`^../m.
0010: DD 71 05 6A B1 21 DB B0 B0 0F D7 3E 7A DB 12 84 .q.j.!.....>z...
0020: 3A C0 63 1B C1 FE FD C5 60 27 E3 2E 14 A0 38 2C :.c.....`'....8,
0030: EE 82 8C 6E 13 05 8A BC 24 2F A1 4F 5C 25 24 10 ...n....$/.O%$.
0040: EC 5A D1 E3 23 AC 51 BA D4 33 6C AF AF A2 68 2F .Z..#.Q..3l...h/
0050: 29 4F 33 F9 0A 56 C1 83 0C 07 30 14 40 A2 CF 17 )O3..V....0.@...
0060: B1 A1 18 AD 51 76 EA 8E D6 6E 50 4E 7A 7C F5 89 ....Qv...nPNz...
0070: B1 73 F4 05 D2 E9 1B 94 48 2F 65 30 33 F4 1B 28 .s......H/e03..(
0080: AA 36 4C 11 52 C5 2A 9D 4A 11 6D FA 9B C6 09 37 .6L.R.*.J.m....7
0090: A1 CC AC A3 67 B1 60 E6 65 F1 0C 98 0E 5E C0 89 ....g.`.e....^..
00A0: BD 54 98 81 51 DB 6C 53 A5 8C AD 05 57 60 46 20 .T..Q.lS....W`F
00B0: 5E 60 74 58 F8 88 2A 46 F6 F5 5A D3 20 FC 9E FA ^`tX..*F..Z. ...
00C0: 8D 14 A8 72 99 F5 FF 9E 0B 5B F9 68 77 30 75 93 ...r.....[.hw0u.
00D0: 3E 7A 16 38 55 11 30 D6 A1 39 97 97 DB 86 B8 9E >z.8U.0..9......
00E0: 3F 08 84 93 A3 A7 E0 4F 6D 07 A2 E6 F9 09 E8 3B ?......Om......;
00F0: 6C 86 F2 26 F6 20 04 D9 92 66 DC 3B 69 FA 75 30 l..&. ...f.;i.u0
]
[Storing dev.p12]
3 Exported and saved the certificate in dev.cer
keytool -export -alias developerKey -keystore dev.p12 -storetype PKCS12 -storepass dev123 -rfc -file dev.cer
Result(DOS Output):
Certificate stored in file <dev.cer>
4.Imported dev.cer in the keystore as using the command as… and selected y
keytool -import -v -file dev.cer -keystore tomcat.keystore -storepass server123
Result(DOS Output):
Owner: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Serial number: 503c03cf
Valid from: Mon Aug 12 12:16:26 IST 2013 until: Sun Nov 10 12:16:26 IST 2013
Certificate fingerprints:
MD5: 7A:CE:AD:78:31:12:89:3A:20:94:01:63:5C:E6:6D:48
SHA1: 4C:E3:4A:CF:93:EF:69:46:AD:01:B1:AC:22:F4:E6:91:B5:62:D1:C3
SHA256: D1:E6:20:9C:A7:3C:82:46:7A:2A:E6:61:1E:30:E3:F0:B9:E6:F0:03:DA:
19:87:B4:6F:F2:B1:BE:D3:89:A8:2B
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(..
0010: 34 63 F2 4C 4c.L
]
]
Trust this certificate? [no]: y
Certificate was added to keystore
[Storing tomcat.keystore]
5.Added the connecter entry to server.xml as…
<Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
keystoreFile="D:/server.keystore" keystorePass="server123"
truststoreFile="D:/server.keystore" truststorePass="server123"
clientAuth="true" sslProtocol="TLS" />
6. Started Tomcat, firefox and on Tools->Options->Advanced->View Certificates->Your Certificate->import, imported the dev.p12 file
Result: asked me for the password which I entered as dev123 then i hit next, next till finish
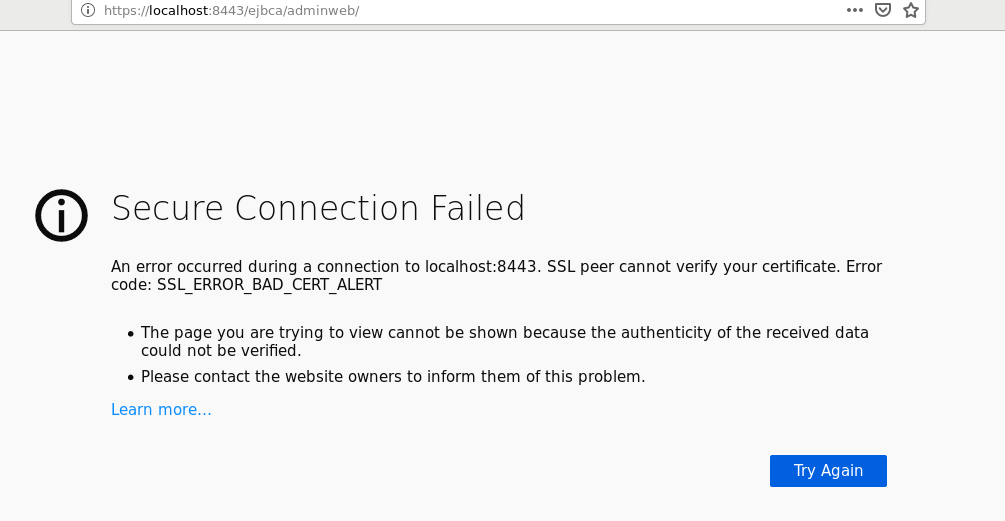
Final Result on opening https://localhost:8443/CertificatePOC/
Secure Connection Failed
An error occurred during a connection to localhost:8443.
SSL peer cannot verify your certificate.
(Error code: ssl_error_bad_cert_alert)
If in the server.xml I change the attribute clientAuth to false then the web page opens correctly.
Any help will be appreciated
I am using tomcat7 with eclipse indigo OS windows 7
If any more details/screenshot is required I will happily provide
Are you trying to browse the internet using Firefox, but are you getting the error message ‘ssl_error_bad_cert_alert’?
Tech Support 24/7
Ask a Tech Specialist Online
Connect with the Expert via email, text or phone. Include photos, documents, and more. Get step-by-step instructions from verified Tech Support Specialists.
On this page, you will find more information about the most common causes and most relevant solutions for the Firefox error ‘ssl_error_bad_cert_alert’. Do you need help straight away? Visit our support page.
Let’s get started
It has never been easier to solve error «ssl_error_bad_cert_alert».
View list of solutions
Contact an expert
Error information
How to solve Firefox error ssl_error_bad_cert_alert
We’ve created a list of solutions which you can follow if you want to solve this Firefox problem yourself. Do you need more help? Visit our support page if you need professional support with Firefox right away.
Tech Support 24/7
Ask a Tech Specialist Online
Connect with the Expert via email, text or phone. Include photos, documents, and more. Get step-by-step instructions from verified Tech Support Specialists.
On this page, you will find more information about the most common causes and most relevant solutions for the Firefox error ‘ssl_error_bad_cert_alert’. Do you need help straight away? Visit our support page.
Let’s get started
It has never been easier to solve error «ssl_error_bad_cert_alert».
View list of solutions
Contact an expert
Error information
How to solve Firefox error ssl_error_bad_cert_alert
We’ve created a list of solutions which you can follow if you want to solve this Firefox problem yourself. Do you need more help? Visit our support page if you need professional support with Firefox right away.
Tech Support 24/7
Ask a Tech Specialist Online
Connect with the Expert via email, text or phone. Include photos, documents, and more. Get step-by-step instructions from verified Tech Support Specialists.
Have you found a solution yourself, but it is not in the list? Share your solution in the comments below.
Need more help?
Do you need more help?
Tech experts are ready to answer your questions.
Ask a question
Исправление ошибки сертификата SSL [Учебное пособие]
Я делаю учебник по взаимной аутентификации SSL с использованием tomcat. Я попробовал найти ответ в Google и stackoverflow, но пока мне не повезло. Я сделал следующие шаги
1. Сгенерировал самоподписанный сертификат, используя команду как …
keytool -genkey -v -alias tomcat -keyalg RSA -validity 3650 -keystore D:server.keystore -dname 'CN=KeshavServer,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN' -storepass server123 -keypass server123 Результат (вывод DOS):
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) with a validity of 3,650 days for: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN New certificate (self-signed): [ [ Version: V3 Subject: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11 Key: Sun RSA public key, 2048 bits modulus: 169745031109692228700332160907879660712549791227819060217679327134557 60724387920644418620368961814809125561438164385172820012631533276651192871536066 44484789458740611952365817466495640787815691991239210085729312562284526930712191 68874744017392521167643053301439564836240073082909781032758910760996909343586608 99178037089977353808963798076122662239868847716719923568980681140353282369676681 53737103284233931190726847482006084262000642602659963850552605206369455374224663 42718874198088754429094645464054866254482989193982685337964154043630072713972109 68332098433075932439269617793403644275259520886009675985568022246951 public exponent: 65537 Validity: [From: Mon Aug 12 12:16:13 IST 2013, To: Thu Aug 10 12:16:13 IST 2023] Issuer: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN SerialNumber: [ 713ab315] Certificate Extensions: 1 [1]: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: D6 0E 1F 23 B2 11 92 D2 19 7B C9 AA 19 EF 82 EB ...#............ 0010: A6 0C 35 57 ..5W ] ] ] Algorithm: [SHA256withRSA] Signature: 0000: 4C 36 84 CD FE 2C 11 4B 88 C1 AE 3A 7A 6A A1 C4 L6...,.K...:zj.. 0010: 2C 6E F5 73 33 64 57 06 04 7F AC 1B D6 CA BF E0 ,n.s3dW......... 0020: D2 88 09 A9 B8 4D 70 EE 73 6E 02 45 33 83 42 1E .....Mp.sn.E3.B. 0030: C4 8E 67 F3 51 D7 9C 53 08 CD C7 EA 4B BC 27 0D ..g.Q..S....K.'. 0040: 17 36 9B 12 4A F7 F7 23 0E C2 51 0A 18 06 B5 80 .6..J..#..Q..... 0050: 1C 44 17 0D 99 14 6E 27 40 30 56 DF 31 D9 CC 15 .D....n'@0V.1... 0060: 46 7C 72 C2 54 CE 2E 2B 41 94 19 54 9B 3A F7 85 F.r.T..+A..T.:.. 0070: 96 CE 5F 80 C5 A5 02 AE 09 17 A5 C3 E4 A6 BB 63 .._............c 0080: A3 EF 99 4F BC A4 FF 4F 2B BD 46 E5 BE 57 C7 BD ...O...O+.F..W.. 0090: 85 54 F9 B1 5F 01 18 07 9F DD 02 99 91 B3 35 FB .T.._.........5. 00A0: 62 74 2A 0A 37 8A 9B 0D E8 BF B4 24 CE 24 12 8A bt*.7......$.$.. 00B0: 22 68 39 90 BD 02 24 A4 E9 9B 52 E1 AA 76 1D 16 'h9...$...R..v.. 00C0: 91 2A 60 49 D3 F6 91 0A 01 E4 98 1B BB EB B7 E5 .*`I............ 00D0: E3 DF 39 B8 73 02 C3 1D EA 95 D1 95 A7 27 53 FC ..9.s........'S. 00E0: 28 2B 21 50 90 BF 48 9A 25 92 28 D8 EC FE 82 60 (+!P..H.%.(....` 00F0: B9 21 28 B3 1A 37 B6 79 17 8B FF 4C 0B C1 6D 0C .!(..7.y...L..m. ] [Storing D:server.keystore] 2. Сгенерировал ключ разработчика, используя команду как …
keytool -genkey -v -alias developerKey -keyalg RSA -storetype PKCS12 -keystore dev.p12 -dname 'CN=KeshavClient,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN' -storepass dev123 -keypass dev123 Result(DOS Output): Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) wi th a validity of 90 days for: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN New certificate (self-signed): [ [ Version: V3 Subject: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11 Key: Sun RSA public key, 2048 bits modulus: 257861330490904259854513552509935970316490717846991127699603148980652 01114722960469328519589253139525292368465436006354129813882061510118729695295380 60706390500779076802188937858019079525575493711793923541823056735274180328061957 20693618061100873813154701306998418961615717804323475393466678818363454317730604 32071710089666113885067366725913386597296681138020057906688646996872449490785655 01898351843152376966821908896570275550705585694195185294854938453556896208850780 54361881798687601045808741784626686357148783050499722574071065943861302398542177 91929018282855348848062666985932392623629290470810910913665654471519 public exponent: 65537 Validity: [From: Mon Aug 12 12:16:26 IST 2013, To: Sun Nov 10 12:16:26 IST 2013] Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN SerialNumber: [ 503c03cf] Certificate Extensions: 1 [1]: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(.. 0010: 34 63 F2 4C 4c.L ] ] ] Algorithm: [SHA256withRSA] Signature: 0000: 91 79 CF CC 0F FD CA BB 2A 60 5E 87 8F 2F 6D B6 .y......*`^../m. 0010: DD 71 05 6A B1 21 DB B0 B0 0F D7 3E 7A DB 12 84 .q.j.!.....>z... 0020: 3A C0 63 1B C1 FE FD C5 60 27 E3 2E 14 A0 38 2C :.c.....`'....8, 0030: EE 82 8C 6E 13 05 8A BC 24 2F A1 4F 5C 25 24 10 ...n....$/.O%$. 0040: EC 5A D1 E3 23 AC 51 BA D4 33 6C AF AF A2 68 2F .Z..#.Q..3l...h/ 0050: 29 4F 33 F9 0A 56 C1 83 0C 07 30 14 40 A2 CF 17 )O3..V....0.@... 0060: B1 A1 18 AD 51 76 EA 8E D6 6E 50 4E 7A 7C F5 89 ....Qv...nPNz... 0070: B1 73 F4 05 D2 E9 1B 94 48 2F 65 30 33 F4 1B 28 .s......H/e03..( 0080: AA 36 4C 11 52 C5 2A 9D 4A 11 6D FA 9B C6 09 37 .6L.R.*.J.m....7 0090: A1 CC AC A3 67 B1 60 E6 65 F1 0C 98 0E 5E C0 89 ....g.`.e....^.. 00A0: BD 54 98 81 51 DB 6C 53 A5 8C AD 05 57 60 46 20 .T..Q.lS....W`F 00B0: 5E 60 74 58 F8 88 2A 46 F6 F5 5A D3 20 FC 9E FA ^`tX..*F..Z. ... 00C0: 8D 14 A8 72 99 F5 FF 9E 0B 5B F9 68 77 30 75 93 ...r.....[.hw0u. 00D0: 3E 7A 16 38 55 11 30 D6 A1 39 97 97 DB 86 B8 9E >z.8U.0..9...... 00E0: 3F 08 84 93 A3 A7 E0 4F 6D 07 A2 E6 F9 09 E8 3B ?......Om......; 00F0: 6C 86 F2 26 F6 20 04 D9 92 66 DC 3B 69 FA 75 30 l..&. ...f.;i.u0 ] [Storing dev.p12] 3 Экспортировал и сохранил сертификат в dev.cer keytool -export -alias developerKey -keystore dev.p12 -storetype PKCS12 -storepass dev123 -rfc -file dev.cer
Result(DOS Output): Certificate stored in file 4.Импортирован dev.cer в хранилище ключей с использованием команды как … и выбран y keytool -import -v -file dev.cer -keystore tomcat.keystore -storepass server123
Result(DOS Output): Owner: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN Serial number: 503c03cf Valid from: Mon Aug 12 12:16:26 IST 2013 until: Sun Nov 10 12:16:26 IST 2013 Certificate fingerprints: MD5: 7A:CE:AD:78:31:12:89:3A:20:94:01:63:5C:E6:6D:48 SHA1: 4C:E3:4A:CF:93:EF:69:46:AD:01:B1:AC:22:F4:E6:91:B5:62:D1:C3 SHA256: D1:E6:20:9C:A7:3C:82:46:7A:2A:E6:61:1E:30:E3:F0:B9:E6:F0:03:DA: 19:87:B4:6F:F2:B1:BE:D3:89:A8:2B Signature algorithm name: SHA256withRSA Version: 3 Extensions: #1: ObjectId: 2.5.29.14 Criticality=false SubjectKeyIdentifier [ KeyIdentifier [ 0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(.. 0010: 34 63 F2 4C 4c.L ] ] Trust this certificate? [no]: y Certificate was added to keystore [Storing tomcat.keystore] 5. Добавлена запись коннектора в server.xml как …
6. Запустил Tomcat, firefox и в Инструменты-> Параметры-> Дополнительно-> Просмотр сертификатов-> Ваш сертификат-> импорт, импортировал файл dev.p12 Результат: попросил меня ввести пароль, который я ввел как dev123, затем я нажал следующий, следующий до конца
Final Result on opening https://localhost:8443/CertificatePOC/ Secure Connection Failed An error occurred during a connection to localhost:8443. SSL peer cannot verify your certificate. (Error code: ssl_error_bad_cert_alert) Если в server.xml я изменяю атрибут clientAuth на false, тогда веб-страница открывается правильно.
Любая помощь будет оценена по достоинству. Я использую tomcat7 с ОС Windows 7 eclipse indigo. Если требуется дополнительная информация / снимок экрана, я с радостью предоставлю
Ошибка ssl_error_bad_cert_alert в этом случае означает, что сервер не доверяет вашему самозаверяющему сертификату. Один из способов решить эту проблему — создать сертификаты и CSR, а затем подписать их в локальном центре сертификации. Затем вы просто добавляете свой ЦС разработчика в хранилище доверенных сертификатов JVM. Это немного больше настроек, но более гибкое (например, вы можете создавать подписанные сертификаты для всей команды разработчиков, тестировать отзыв через OCSP / CRL и т. Д.).
Эти шаги скопированы из моей истории и, вероятно, потребуют изменений:
Создайте локальный центр сертификации разработчиков
openssl genrsa -out ca.key -aes256 -passout pass:changeit 4096 openssl req -new -x509 -key ca.key -config openssl.conf -days 3560 -sha256 -out ca.pem -passin pass:changeit openssl rsa -in ca.key -out ca.key -passin pass:changeit Создание клиентских и серверных хранилищ ключей с парой ключей в каждом
keytool -genkey -keyalg RSA -alias client -keystore client.jks -storepass changeit -validity 1000 keytool -genkey -keyalg RSA -alias tomcat -keystore ~/.keystore -storepass changeit -validity 1000 Создание запросов на подписание сертификатов клиента и сервера (csr) на основе указанных выше пар ключей хранилища ключей.
keytool -certreq -v -alias client -keystore client.jks -storepass changeit -file client.csr keytool -certreq -v -alias tomcat -keystore ~/.keystore -storepass changeit -file tomcat.csr Подпишите запросы (создайте сертификаты) для клиент-серверных csr
openssl x509 -req -CA ca.pem -CAkey ca.key -in client.csr -out client.cer -days 1000 -CAcreateserial openssl x509 -req -CA ca.pem -CAkey ca.key -in tomcat.csr -out tomcat.cer -days 1000 -CAcreateserial Импортируйте сертификат CA в хранилища ключей клиент / сервер (возможно, не обязательно, так как он все равно должен быть добавлен в хранилище доверенных сертификатов)
keytool -import -keystore client.jks -file ca.pem -alias rootca keytool -import -keystore ~/.keystore -file ca.pem -alias rootca Импортируйте сертификаты клиента и сервера в соответствующие хранилища ключей.
keytool -import -keystore client.jks -file client.cer -alias client keytool -import -keystore ~/.keystore -file tomcat.cer -alias tomcat Преобразуйте сертификат клиента в p12 (PKCS12), чтобы его можно было импортировать в firefox или где-нибудь еще
keytool -importkeystore -srckeystore client.jks -destkeystore client.p12 -srcstoretype JKS -deststoretype PKCS12 -srcstorepass changeit -deststorepass changeit -srcalias client -destalias client -srckeypass changeit -destkeypass changeit -noprompt Импортируйте сертификат ЦС в хранилище доверенных сертификатов JVM
sudo keytool -import -trustcacerts -alias suter-dev-ca -file ca.pem -keystore /Library/Java/JavaVirtualMachines/jdk1.7.0_60.jdk/Contents/Home/jre/lib/security/cacerts При желании импортируйте сертификат CA в свой браузер.
Ваш пост было трудно прочитать из-за форматирования. Надеюсь это поможет.
Источники: http://shib.kuleuven.be/docs/ssl_commands.shtml, https://docs.oracle.com/cd/E19509-01/820-3503/ggezy/index.html
Tweet
Share
Link
Plus
Send
Send
Pin
I am doing a tutorial on Mutual SSL authentication using tomcat. I tried google and stackoverflow for the answer but I haven’t been lucky so far. I have done the following steps
1. Generated a self signed Certificate using the command as…
keytool -genkey -v -alias tomcat -keyalg RSA -validity 3650 -keystore D:server.keystore -dname "CN=KeshavServer,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN" -storepass server123 -keypass server123
Result(DOS Output):
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) with a validity of 3,650 days for: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
New certificate (self-signed):
[
[
Version: V3
Subject: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
modulus: 169745031109692228700332160907879660712549791227819060217679327134557
60724387920644418620368961814809125561438164385172820012631533276651192871536066
44484789458740611952365817466495640787815691991239210085729312562284526930712191
68874744017392521167643053301439564836240073082909781032758910760996909343586608
99178037089977353808963798076122662239868847716719923568980681140353282369676681
53737103284233931190726847482006084262000642602659963850552605206369455374224663
42718874198088754429094645464054866254482989193982685337964154043630072713972109
68332098433075932439269617793403644275259520886009675985568022246951
public exponent: 65537
Validity: [From: Mon Aug 12 12:16:13 IST 2013,
To: Thu Aug 10 12:16:13 IST 2023]
Issuer: CN=KeshavServer, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
SerialNumber: [ 713ab315]
Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: D6 0E 1F 23 B2 11 92 D2 19 7B C9 AA 19 EF 82 EB ...#............
0010: A6 0C 35 57 ..5W
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 4C 36 84 CD FE 2C 11 4B 88 C1 AE 3A 7A 6A A1 C4 L6...,.K...:zj..
0010: 2C 6E F5 73 33 64 57 06 04 7F AC 1B D6 CA BF E0 ,n.s3dW.........
0020: D2 88 09 A9 B8 4D 70 EE 73 6E 02 45 33 83 42 1E .....Mp.sn.E3.B.
0030: C4 8E 67 F3 51 D7 9C 53 08 CD C7 EA 4B BC 27 0D ..g.Q..S....K.'.
0040: 17 36 9B 12 4A F7 F7 23 0E C2 51 0A 18 06 B5 80 .6..J..#..Q.....
0050: 1C 44 17 0D 99 14 6E 27 40 30 56 DF 31 D9 CC 15 .D....n'@0V.1...
0060: 46 7C 72 C2 54 CE 2E 2B 41 94 19 54 9B 3A F7 85 F.r.T..+A..T.:..
0070: 96 CE 5F 80 C5 A5 02 AE 09 17 A5 C3 E4 A6 BB 63 .._............c
0080: A3 EF 99 4F BC A4 FF 4F 2B BD 46 E5 BE 57 C7 BD ...O...O+.F..W..
0090: 85 54 F9 B1 5F 01 18 07 9F DD 02 99 91 B3 35 FB .T.._.........5.
00A0: 62 74 2A 0A 37 8A 9B 0D E8 BF B4 24 CE 24 12 8A bt*.7......$.$..
00B0: 22 68 39 90 BD 02 24 A4 E9 9B 52 E1 AA 76 1D 16 "h9...$...R..v..
00C0: 91 2A 60 49 D3 F6 91 0A 01 E4 98 1B BB EB B7 E5 .*`I............
00D0: E3 DF 39 B8 73 02 C3 1D EA 95 D1 95 A7 27 53 FC ..9.s........'S.
00E0: 28 2B 21 50 90 BF 48 9A 25 92 28 D8 EC FE 82 60 (+!P..H.%.(....`
00F0: B9 21 28 B3 1A 37 B6 79 17 8B FF 4C 0B C1 6D 0C .!(..7.y...L..m.
]
[Storing D:server.keystore]
2. Generated the developer key by using the command as…
keytool -genkey -v -alias developerKey -keyalg RSA -storetype PKCS12 -keystore dev.p12 -dname "CN=KeshavClient,OU=AppDev,O=Netambit,L=Noida,S=UP,C=IN" -storepass dev123 -keypass dev123
Result(DOS Output):
Generating 2,048 bit RSA key pair and self-signed certificate (SHA256withRSA) wi
th a validity of 90 days
for: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
New certificate (self-signed):
[
[
Version: V3
Subject: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Signature Algorithm: SHA256withRSA, OID = 1.2.840.113549.1.1.11
Key: Sun RSA public key, 2048 bits
modulus: 257861330490904259854513552509935970316490717846991127699603148980652
01114722960469328519589253139525292368465436006354129813882061510118729695295380
60706390500779076802188937858019079525575493711793923541823056735274180328061957
20693618061100873813154701306998418961615717804323475393466678818363454317730604
32071710089666113885067366725913386597296681138020057906688646996872449490785655
01898351843152376966821908896570275550705585694195185294854938453556896208850780
54361881798687601045808741784626686357148783050499722574071065943861302398542177
91929018282855348848062666985932392623629290470810910913665654471519
public exponent: 65537
Validity: [From: Mon Aug 12 12:16:26 IST 2013,
To: Sun Nov 10 12:16:26 IST 2013]
Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
SerialNumber: [ 503c03cf]
Certificate Extensions: 1
[1]: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(..
0010: 34 63 F2 4C 4c.L
]
]
]
Algorithm: [SHA256withRSA]
Signature:
0000: 91 79 CF CC 0F FD CA BB 2A 60 5E 87 8F 2F 6D B6 .y......*`^../m.
0010: DD 71 05 6A B1 21 DB B0 B0 0F D7 3E 7A DB 12 84 .q.j.!.....>z...
0020: 3A C0 63 1B C1 FE FD C5 60 27 E3 2E 14 A0 38 2C :.c.....`'....8,
0030: EE 82 8C 6E 13 05 8A BC 24 2F A1 4F 5C 25 24 10 ...n....$/.O%$.
0040: EC 5A D1 E3 23 AC 51 BA D4 33 6C AF AF A2 68 2F .Z..#.Q..3l...h/
0050: 29 4F 33 F9 0A 56 C1 83 0C 07 30 14 40 A2 CF 17 )O3..V....0.@...
0060: B1 A1 18 AD 51 76 EA 8E D6 6E 50 4E 7A 7C F5 89 ....Qv...nPNz...
0070: B1 73 F4 05 D2 E9 1B 94 48 2F 65 30 33 F4 1B 28 .s......H/e03..(
0080: AA 36 4C 11 52 C5 2A 9D 4A 11 6D FA 9B C6 09 37 .6L.R.*.J.m....7
0090: A1 CC AC A3 67 B1 60 E6 65 F1 0C 98 0E 5E C0 89 ....g.`.e....^..
00A0: BD 54 98 81 51 DB 6C 53 A5 8C AD 05 57 60 46 20 .T..Q.lS....W`F
00B0: 5E 60 74 58 F8 88 2A 46 F6 F5 5A D3 20 FC 9E FA ^`tX..*F..Z. ...
00C0: 8D 14 A8 72 99 F5 FF 9E 0B 5B F9 68 77 30 75 93 ...r.....[.hw0u.
00D0: 3E 7A 16 38 55 11 30 D6 A1 39 97 97 DB 86 B8 9E >z.8U.0..9......
00E0: 3F 08 84 93 A3 A7 E0 4F 6D 07 A2 E6 F9 09 E8 3B ?......Om......;
00F0: 6C 86 F2 26 F6 20 04 D9 92 66 DC 3B 69 FA 75 30 l..&. ...f.;i.u0
]
[Storing dev.p12]
3 Exported and saved the certificate in dev.cer
keytool -export -alias developerKey -keystore dev.p12 -storetype PKCS12 -storepass dev123 -rfc -file dev.cer
Result(DOS Output):
Certificate stored in file <dev.cer>
4.Imported dev.cer in the keystore as using the command as… and selected y
keytool -import -v -file dev.cer -keystore tomcat.keystore -storepass server123
Result(DOS Output):
Owner: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Issuer: CN=KeshavClient, OU=AppDev, O=Netambit, L=Noida, ST=UP, C=IN
Serial number: 503c03cf
Valid from: Mon Aug 12 12:16:26 IST 2013 until: Sun Nov 10 12:16:26 IST 2013
Certificate fingerprints:
MD5: 7A:CE:AD:78:31:12:89:3A:20:94:01:63:5C:E6:6D:48
SHA1: 4C:E3:4A:CF:93:EF:69:46:AD:01:B1:AC:22:F4:E6:91:B5:62:D1:C3
SHA256: D1:E6:20:9C:A7:3C:82:46:7A:2A:E6:61:1E:30:E3:F0:B9:E6:F0:03:DA:
19:87:B4:6F:F2:B1:BE:D3:89:A8:2B
Signature algorithm name: SHA256withRSA
Version: 3
Extensions:
#1: ObjectId: 2.5.29.14 Criticality=false
SubjectKeyIdentifier [
KeyIdentifier [
0000: AD 4A E3 0E 3D E9 DB B0 8E DF 8F 66 34 28 AE AF .J..=......f4(..
0010: 34 63 F2 4C 4c.L
]
]
Trust this certificate? [no]: y
Certificate was added to keystore
[Storing tomcat.keystore]
5.Added the connecter entry to server.xml as…
<Connector port="8443" protocol="HTTP/1.1" SSLEnabled="true"
maxThreads="150" scheme="https" secure="true"
keystoreFile="D:/server.keystore" keystorePass="server123"
truststoreFile="D:/server.keystore" truststorePass="server123"
clientAuth="true" sslProtocol="TLS" />
6. Started Tomcat, firefox and on Tools->Options->Advanced->View Certificates->Your Certificate->import, imported the dev.p12 file
Result: asked me for the password which I entered as dev123 then i hit next, next till finish
Final Result on opening https://localhost:8443/CertificatePOC/
Secure Connection Failed
An error occurred during a connection to localhost:8443.
SSL peer cannot verify your certificate.
(Error code: ssl_error_bad_cert_alert)
If in the server.xml I change the attribute clientAuth to false then the web page opens correctly.
Any help will be appreciated
I am using tomcat7 with eclipse indigo OS windows 7
If any more details/screenshot is required I will happily provide
Добрый день!
При запуске Ejbca, в FireFox появляется ошибка SSL_ERROR_BAD_CERT_ALERT.
Подскажите, как ее побороть…
-
Вопрос заданболее трёх лет назад
-
137 просмотров