Содержание
- How I solved “Unable to access HASP SRM Run-time Environment? (H0033)”
- Background
- Solution
- Share Post
- Gary Davis
- Sentinel В® LDK Environment Installer GUI for Windows: Readme
- Version 7.81
- July 2018
- Operating Systems Supported
- Virtual Environments Supported
- Upgrading the Run-time Environment
- Installing the Run-time Environment
- Allowing Incoming Connections From Public Networks Using Port 1947
- Issues Related to Device Guard and Code Integrity Policies
- Issue 1: Windows blocks the installation of the Run-time Environment
- Issue 2: Protected application does not operate at the customer site
- Issue 3: Vendor Tools fail to load
- Issue 4: Digital signature removed from the RTE Installer
- Enhancements and Issues Resolved in This Release
- Enhancements
- Issues Resolved
- Security Updates in This Release
- Reporting a Security Vulnerability
- Revision History
- Issues Resolved in Version 7.80
- Issues Resolved in Version 7.65
- Enhancements in Version 7.63
- Issues Resolved in Version 7.63
- Enhancements in Version 7.60
- Issues Resolved in Version 7.60
- Enhancements in Version 7.55
- Issues Resolved in Version 7.55
- Enhancements in Version 7.54
- Issues Resolved in Version 7.54
- Issues Resolved in Version 7.53
- Enhancements in Version 7.52
- Issues Resolved in Version 7.52
- Issues Resolved in Version 7.51
- Issues Resolved in Version 7.50
- Issues Resolved in Version 7.41
- Enhancements in Revision 7.40
- Issues Resolved in Version 7.40
- Known Issues — Run-time Environment
How I solved “Unable to access HASP SRM Run-time Environment? (H0033)”
First of all, don’t stress! These instructions will most likely get you up and running with your 4D, 5D, 6D or other dongle-controlled program in short order.
Background
My wife asked me to install her Viking embroidery “5D” software on her Surface Pro PC so she could use the touch tablet and pen to do graphics drawing and editing in the Design Creator.
The software is protected by requiring the user to have a USB dongle plugged in when running the program.
Installation went through normal software install and then it also had 3 updates to install. Two of the updates seemed to end with an error, perhaps because I did not reboot the PC after each (it was not clear whether or not to do this). At any point, running the program with the dongle installed resulted in the H0033 error.
I tried doing a repair install and also install of drivers (from the main install menu) – neither helped.
Searching on this error showed several hits saying to go to the windows Services and enabling the HASP License Manager (or Sentinel HASP License Manager) but in my case, I did not have the HASP entry in Services.
I looked in the Device Manager and saw an error for the HASP device and its properties said the device driver was not installed. Doing an Uninstall followed by a Scan for New Hardware did not help.
Some posts said to try to go to this url in your browser: http://localhost:1947 but that just displayed an error. Normally, this would display the HASP SRM Admin Control Center.
Solution
I eventually found a post to download the HASP SRM Runtime drivers at https://sentinelcustomer.gemalto.com/sentineldownloads/ (or use the link below). Installing this did solve the H0033 error. Also, once installed, the dongle light was lit and the http://localhost:1947 worked.
From the download page, I chose to install the Sentinel HASP/LDK Windows GUI Run-time Installer. The zip file contains a Readme file and a HASPUserSetup.exe file. Run the exe file to start the installation. It’s pretty quick.
Copy of HASP SRM Runtime download zip file:
When I installed the driver, I did not have the dongle plugged in. After the install, I tried going to the the localhost url above and it worked (displayed a page, not an error). I then plugged in the dongle and it lit up and the localhost url displayed more mildly interesting information.
Read the feedback (over 100 posts) and you will see virtually everybody is successful with this procedure. Please post feedback on your results.
Gary Davis
DotNET/PayPal Development and other Techie Stuff
Источник
Sentinel В® LDK Environment Installer GUI for Windows: Readme
Version 7.81
July 2018
This document provides information regarding the Run-time Environment Installer GUI for Sentinel LDK and Sentinel HASP, including supported operating systems, enhancements, known compatibility issue, and issues resolved. («Sentinel LDK» is the next generation of Sentinel HASP.)
The following topics are discussed:
Operating Systems Supported
- Windows 7 SP1
- Windows 7 SP1 Embedded standard (x86)
- Windows 8.1 SP1
- Windows Server 2008 R2 SP1
- Windows Server 2012 R2
- Windows Server 2016
- Windows 10 Version 1803
Note: Windows 10 Insider Preview builds are not supported.
The operating system versions listed in this section were tested by Gemalto and verified to be fully compatible with Sentinel LDK. For reasons of compatibility and security, Gemalto recommends that you always keep your operating system up to date with the latest fixes and service packs.
The installer detects the version of the operating system at run-time, before installing the relevant drivers.
Virtual Environments Supported
For a list of the virtual environments supported, see «Supported Platforms for End Users» in the Sentinel LDK Release Notes.
Upgrading the Run-time Environment
When using the Installer GUI to upgrade the Run-time Environment, ensure that:
- No other Run-time Environment Installer is active.
- No other Run-time Environment components are active. Although the installation program terminates applications that are accessing the Run-time, it does not terminate running services. For example, if the Sentinel License Manager is running as a service, you must stop the service before upgrading the Run-time Environment.
Installing the Run-time Environment
- The Installer GUI detects the version of the operating system during Run-time Environment installation, before installing the relevant drivers.
- By default, Windows displays a User Account Control message during driver installation. The user must click Continue to continue the installation. Alternatively, the user can change the default setting from the Control Panel of their operating system.
- A log file of the installation process is written to aksdrvsetup.log in the Windows directory.
For additional information, see “2.17 — Upgrading Sentinel LDK Run-Time Environment (RTE) Installer” in the Sentinel EMS Configuration Guide.
Allowing Incoming Connections From Public Networks Using Port 1947
The Run-time Environment Installer adds a firewall rule named “Sentinel License Manager” that allowed incoming connections from private networks using port 1947.
You can manually allow access from public networks using this port, but Gemalto highly recommends against this.
If you do plan to allow incoming connections from public networks using port 1947, create a rule with a different name in order to prevent future RTE upgrades from removing this access.
The traditional method until now to protect against malicious application under Windows has been to trust the applications unless they were blocked by an antivirus or other security solution. Device Guard, available in Windows 10 Enterprise, implements a mode of operation in which the operating system trusts only applications that are authorized by your enterprise. You designate these trusted applications by creating code integrity policies.
You can maintain a whitelist of software that is allowed to run (a configurable code integrity policy), rather than trying to stay ahead of attackers by maintaining a constantly-updated list of «signatures» of software that should be blocked. This approach uses the trust-nothing model well known in mobile device operating systems.
Only code that is verified by Code Integrity, usually through the digital signature that you have identified as being from a trusted signer, is allowed to run. This allows full control over allowed code in both kernel and user mode.
Code integrity contains two primary components:
- kernel mode code integrity (KMCI)
- user mode code integrity (UMCI)
This section describes issues that arise and the workarounds when machines at the end user site are enabled with Device Guard, and the code integrity policy set to “enforce” mode.
Note: The procedures described in this document should be performed by an IT professional who is familiar with Device Guard and code integrity policies.
Issue 1: Windows blocks the installation of the Run-time Environment
During installation of the Run-time Environment on your computer, Windows displays a message similar to this: «Your organization used Device Guard to block this app. Contact your support person for more info.»
Solution:
To install the Run-time Environment on a machine where Device Guard is enabled in enforce mode (which make use of PcaCertificate level code signing check), ensure that DigiCert is listed/added in the Signers list of the policy file.
Import the DigiCert Intermediate certificate to the trusted list of Intermediate Certification Authorities(ICA) store on the golden computer before creating code integrity policy.
A Digicert Intermediate certificate is available from https://aboutssl.org/digicert-trusted-root-authority-certificates/#intermediates. Under Intermediate Certificates, locate and download the DigiCert EV Code Signing CA (SHA2) certificate. You can also fetch this intermediate certificate from your trusted source.
To add the DigiCert Root Certificate:
- Download the certificate on the golden computer and double-click the certificate file. The Certificate dialog box is displayed.
- Click Install Certificate. Follow the Certificate Install Wizard to complete the import of this certificate to the ICA store.
- Run the steps to create a new or updated policy. This will allow Sentinel software to be installed without any issues on a machine where Device Guard is enabled.
Repeat the installation of the Run-time Environment.
Issue 2: Protected application does not operate at the customer site
(LDK-17267) ) When you distribute applications that are protected with SL keys, the customized vendor library (haspvlib_vendorID.*) that are required for these applications are not signed. As a result, Device Guard does not allow the software to operate at the customer site.
Workaround A:
This workaround must be performed at the customer site.
Do the following to add an exception for the customized vendor library file in the code integrity policy:
- Use Windows PowerShell in elevated mode to create a policy for the exception.
- Use the Group Policy editor to deploy the policy file.
To create the policy for the exception:
- Open PowerShell in elevated mode.
- Run the command to create a policy (referred to below as P1) in audit mode.
- Deploy this policy.
- Operate the protected application as you would normally.
- Create another policy (referred to as P2) that captures audit information from the events log.
Note: Before proceeding with the next step, review policy P2 carefully. This policy contains information about all the binaries that were used in your system while you operated the protected application. Any unwanted application that was executed during this time is logged in the policy. If not removed, any such application will be treated as a trusted binary. - Merge policies P1 and P2.
- Disable audit mode.
- Deploy the merged policy.
To deploy the policy file:
- Open the Group Policy editor by running GPEdit.msc.
- Navigate to: Computer ConfigurationAdministrative TemplatesSystemDevice Guard
- Select Deploy Code Integrity Policy. Enable this setting by using the path to the relevant policy file created above.
Workaround B (not recommended):
This workaround must be performed at the customer site.
Before deploying the code integrity policy, disable UMCI (user mode code integrity) mode.
To accomplish this, run the following command in Windows PowerShell in elevated mode:
Set-RuleOption -FilePath
-Option 0 -Delete
Issue 3: Vendor Tools fail to load
(SM-907) Sentinel LDK Vendor Tools fail to load. An error message is displayed, stating that a DLL, LIB, COM, or EXE file is not designed to run on Windows or that the DLL contains an error.
Workaround A:
Do the following to add a policy for the Sentinel LDK Vendor Tools in the code integrity policy file:
- Use Windows PowerShell in elevated mode to create a policy for the Vendor Tools.
- Use the Group Policy editor to deploy the policy file.
To create the policy for the Vendor Tools:
- Open PowerShell in elevated mode.
- Run the command to create a policy (referred to below as P1) in audit mode.
- Deploy this policy.
- Execute all of the Vendor Tools that you will require at your site and perform all of the functions in these tools that you will require. If you miss any required Vendor Tools or Vendor Tool functions, the required entries will not be added in the new code integrity policy, and these tools or functions will generate an error message when they are eventually used.
- Create another policy (referred to as P2) that captures audit information from the events log.
Note: Before proceeding with the next step, review policy P2 carefully. This policy contains information about all the binaries that were used in your system while you operated the Vendor Tools. Any unwanted application that was executed during this time is logged in the policy. If not removed, any such application will be treated as a trusted binary. - Merge policies P1 and P2.
- Disable audit mode.
- Deploy the merged policy.
To deploy the policy file:
- Open the Group Policy editor by running GPEdit.msc.
- Navigate to: Computer ConfigurationAdministrative TemplatesSystemDevice Guard
- Select Deploy Code Integrity Policy. Enable this setting by using the path to the relevant policy file created above.
Workaround B (not recommended):
Perform this workaround at your development site.
Before deploying the code integrity policy, disable UMCI (user mode code integrity) mode.
To accomplish this, run the following command in Windows PowerShell in elevated mode:
Set-RuleOption -FilePath
-Option 0 -Delete
No further actions are required.
Issue 4: Digital signature removed from the RTE Installer
(SM-18780) When a user creates a Run-time Environment Installer using Sentinel EMS, the digital signature is removed from the Installer. As a result, Device Guard blocks the RTE Installer from executing.
If the vendor downloads the installer as an EXE file and signs it, Device Guard allows the installer to run, but the installation fails due to an unsigned DLL file called by haspdinst.exe.
Workaround:
Perform the procedure that follows.
- Download the Run-time Environment Installer from the following URL in the Gemalto web site:
To work with Sentinel EMS, continue with the following additional steps:
- In a Web browser, enter the following to start Admin Control Center: http://localhost:1947
- On the Configuring Network Settings page, in the EMS URL field, enter the URL to access the Sentinel EMS Service.
- Click Submit.
- Proceed to work with Sentinel EMS as required.
As an alternative, you can use one of the workarounds provided above for issues 2 and 3.
Enhancements and Issues Resolved in This Release
Enhancements
The RTE Installer now provides more details in order to help ensure that installation of the RTE completes successfully. The Installer now differentiates between the following situations:
- Installation of the RTE has succeeded. No restart is required.
- Installation of the RTE cannot complete due to a lock on a required file. The RTE Installer attempts to rename the locked file in the background. If it succeeds, the installation will continue. If the rename attempt fails, the installer returns error 52. At this point, your code can call the new RTE Installer API function haspds_GetLockingProcessList to get the locking process name. You can then release the locked file and restart the RTE Installer.
Several security improvements have been implemented.
Issues Resolved
| Reference | Description |
|---|---|
| SM-18163 | |
| SM-27901 | The revision history of all enhancements implemented and issues resolved for earlier versions of the RTE is now available online at: http://sentinelldk.safenet-inc.com/Default.htm |
| SM-30222 SM-30886 |
The hasp_login function would fail to log in to a HASP4 parallel port key (the function would not fail with HASP4 SUB keys). The login would fail with the error code HASP_HASP_NOT_FOUND = 7. This issue would occur with RTE version 7.52 and later.
| Reference | Description |
|---|---|
| SM-28148 | |
| SM-31010 | If the client connected using different IPv6 interfaces, the License Manager would sometimes count the sessions on a machine multiple times. |
Security Updates in This Release
There are no known and unresolved security issue relating to Sentinel products in this release.
For the latest information regarding any older or newly-discovered issues, see this Web page:
Reporting a Security Vulnerability
If you think you have found a security vulnerability, please send it to Gemalto using the links provided on the Web page provided above.
Revision History
This section describes enhancements implemented and issues resolved in the last three major releases of Sentinel Run-time Environment.
The revision history for earlier versions of Sentinel Run-time Environment is available at: http://sentinelldk.safenet-inc.com/Default.htm
Issues Resolved in Version 7.80
If a customer applies a V2C update from a remote machine that has the Vendor library but no license from the same vendor, the error returned was HASP_UPDATE_TOO_NEW, which was confusing. Now the error returned is HASP_KEYID_NOT_FOUND.
The RTE installer adds a firewall rule (named “Sentinel License Manager”) that, in the past, allowed incoming connections from any network, including public networks, using port 1947. Starting with RTE version 7.80, the firewall rule added by the RTE Installer does not allow incoming connections from public networks. If you are upgrading from an earlier version of RTE, the installer replaces the existing rule (that allows connections from public networks) with a rule that blocks such connections.
You can manually allow access using this port from public networks, but Gemalto highly recommends against this.
If you do plan to allow access from public networks using port 1947, create a rule with a different name in order to prevent future RTE upgrades from removing this access.
| Reference | Description |
|---|---|
| SM-12155 | |
| SM-18502 | Defining an excessive number of User Restrictions in Admin Control Center would cause the License Manager Service to fail. |
| SM-19981 | hasp_update would return an internal error for an HL Key when the license definition contains empty content in the default memory section. |
| SM-23609 | |
| SM-25600 | The Run-Time Environment would require an excessive amount of time to install. |
| SM-26543 | Under certain circumstances, Sentinel License Manager would crash on the REST interface with long packets. |
| SM-9841 | HASP4 keys would stop working after the Run-time Environment was upgraded to v.7.54. |
Issues Resolved in Version 7.65
A possible security issue related to buffer overflow (reported by Kaspersky) has been resolved.
| Reference | Description |
|---|---|
| SM-21408 | The Admin Control Center help system was missing information regarding the new “Idle Timeout of Session” configuration parameter. |
| SM-23320 | A possible security issue related to License Manager failure due to stack overflow on deep XML data (reported by Kaspersky) has been resolved. |
| SM-23402 | |
| SM-23813 | A possible security issue that was reported by Kaspersky has been resolved. |
Enhancements in Version 7.63
In the past, the timeout for an idle License Manager session was fixed at 12 hours. You can now set the timeout to any value between 10 minutes and 720 minutes (12 hours). The timeout value can be set as follows:
- In Admin Control Center, on the Basic Configuration page. Use the Idle Timeout of Session parameter.
- In the hasplm.ini file. Assign the timeout value to idle_session_timeout_mins.
Admin Control Center now adds the update counter in C2V files in clear text — for example: 5
It is no longer necessary to decode the C2V file in order to view this information.
| Reference | Description |
|---|---|
| SM-13443 | When a Sentinel HL (HASP configuration) key or HASP HL key is attached to a Windows machine, the Run-time Environment is no longer installed automatically by Windows Update. It is now the software vendor’s responsibility to ensure that the Run-time Environment is installed when required. |
| SM-13505 | |
| SM-14894 | |
| SM-19483 | Admin Control Center now recognizes the new V2CP format to update protection keys. This supports planned enhancements in Sentinel LDK v.7.8. |
Issues Resolved in Version 7.63
The Run-time Environment now supports the use of the VMType3 clone protection scheme.
Enhancements in Version 7.60
| Reference | Description |
|---|---|
| SM-15922 | Admin Control Center no longer requires the |
| Reference | Description |
| SM-5318 |
You can now enter the URL to access Sentinel EMS in your Web browser without changing the EMS URL to lowercase.
Admin Control Center (under Windows) can now display and apply updates to local SL UserMode keys. (Session information and certificate information for SL UserMode keys is not displayed.)
To display SL UserMode keys in Admin Control Station, License Manager runs an additional process (hasplmv) on the machine. If you are willing to accept that SL UserMode keys will not be displayed, you have the option to prevent hasplmv from executing by clearing the relevant check box on the Configuration page in Admin Control Center.
In the past, Admin Control Center and Admin API provided a configuration parameter that determined whether a remote user could access and perform actions in Admin Control Center. However, this parameter did not control remote access to Admin API.
Now, the parameter Allow Remote Access to ACC and Admin API (in Admin Control Center) and the tag (in Admin API) control remote access to both Admin Control Center and Admin API.
Issues Resolved in Version 7.60
| Reference | Description |
|---|---|
| SM-1286 |
When a data file is protected with Version 2 data protection mode for Android platforms: If, for any reason (for example, no license was found), the protected application was not able to decrypt the protected data file, no error message was generated to explain why the file cannot be opened.
Under Windows 10, a physical machine would be detected as a virtual machine when only Hyper-V Hypervisor is enabled.
The Diagnostics report in Admin Control Center (Diagnostics > Generate Report) displays information on «Recent Clients» and «Recent Users». Each entry contained a time stamp but not a date stamp. The report has been corrected to display both a time stamp and a date stamp for each entry.
When building a Run-Time Environment installer using Wix, an error message similar to the following was generated:
Invalid product version ‘7.53.1.66350’ in package HASP_Setup.msi’. When included in a bundle, all product version fields in an MSI package must be less than 65536.
This error no longer occurs.
Under certain circumstances, Sentinel LDK License Manager Service would crash. The exception code would map to STATUS_STACK_OVERFLOW in __chkstk API.
Enhancements in Version 7.55
| Reference | Description |
|---|---|
| LDK-12145 | |
| SM-515 | It was possible to rehost a cloned license to another machine. |
| SM-518 |
Sentinel Admin Control Center can now be used to configure the License Manager for the following additional considerations:
- Allow specific named users to access specific Batch Codes, protection keys (haspID), or Product IDs.
- Use the «*» wildcard character for IP and hostname.
- Use subnet mask notation (for example: 172.18.8.0/21) for IP addresses
For more information, see «Configuring User Settings» in the Admin Control Center online help.
Issues Resolved in Version 7.55
| Reference | Description |
|---|---|
| SM-4748 |
Various crash conditions in the License Manager that could be used for denial-of-service attacks or privilege-escalation attacks have been resolved.
When a user issues a «detach license» request from a remote Admin Control Center, the user name cannot be included in request. As a result, User Restrictions (defined in ACC on the license server machine) that are based on the user name are handled as follows:
- “allow” user restrictions that are based on a specific user name are not applied because the user name is not available to the License Manager on the license server. If a different restriction such as deny=all@all is also specified, the detach request will be denied.
- If any “deny” user restriction that is applicable for the request in all respects other than username exists, that restriction is applied even if the user name specified in the restriction does not match. For example: If the detach request was sent from a machine with the hostname host123, and a user restriction has been specified deny=skr@host123 on the license server machine, the detach request is denied even the user requesting the detach has a different username.
Sentinel Admin Control Center online help has been updated to describe these limitations.
Enhancements in Version 7.54
| Reference | Description |
|---|---|
| SM-4942 |
| Reference | Description |
|---|---|
| SM-889 | Run-time Environment is supported under Windows Server 2016. |
Issues Resolved in Version 7.54
Installation of a rebranded RTE would fail when the account name contains multi-byte characters (such as Japanese). The install log would contain an error similar to the following:
could not open C:UsersuserNameAppDataLocalTempEMSUrl.properties ../hhlinst.c,4659
OPEN file C:UsersuserNameAppDataLocalTempEMSUrl.properties processing error. ../hhlinst.c,4660,
The decrypt function in the HASP4 API would give incorrect results after RTE 7.52 or 7.53 was installed.
| Reference | Description |
|---|---|
| SM-2090 | |
| SM-3767 | After installation of RTE 7.53, hasplms was unreachable to remote clients. The RTE installer did not add the firewall rule to allow Sentinel License Manager Service. |
Issues Resolved in Version 7.53
Given the following scenario:
- Obtain a C2V file for an SL Legacy key.
- Prepare an update to upgrade the SL Legacy key to an SL AdminMode key in Sentinel License Generation API, but do not apply the update.
- Prepare a second update using the first update as the current state for the key.
- Apply the second update to the key.
The update would return a status of OK even though the update fails.
Given the following scenario:
- Connect a Sentinel HL (HASP configuration) key to a machine and generate a C2V file for the key.
- Create an update in Sentinel License Generation API to upgrade the key to a Sentinel HL (Driverless configuration) key, but do not apply the update.
- Prepare a second update to the key using the first update as the current state for the key.
- Apply the second update to the key.
The update would return a status of OK even though the update fails.
Enhancements in Version 7.52
| Reference | Description |
|---|---|
| SM-1201 |
The Features page in Admin Control Center now displays the peak number of consumed seats per Feature. The peak number is based on the current License Manager session. For each Feature, the peak number value is displayed as a tool tip for the seats value under the Logins column. This information enables end users and organizations to determine if the number of seats purchased is suitable for their needs.
The Run-time Environment can now be installed under Windows 10 when Device Guard is enabled.
Issues Resolved in Version 7.52
| Reference | Description |
|---|---|
| LDK-15786 |
A Sentinel HL (HASP configuration) key would not be accessible by the protected application under the following circumstances:
The following conditions exist:
- Windows 10 version 1607 is present on the machine.
- The network is disabled.
- The Run-time Environment is not present on the machine.
The following actions are performed:
- The HL key is connected to the machine and then disconnected.
- The Run-time Environment is installed on the machine.
- The HL key is connected again to the machine.
The HL key would not be accessible.
When using RTE 7.51, a Stop error (BSoD) would occur when the protected application attempted to retrieve the serial number of the disk drive that uses Intel RAID drivers.
Under certain circumstances, the uninstall of the Run-time Environment on a Windows 8 machine would fail.
The uninstall of the Run-time Environment would not provide proper notification if it failed to remove all necessary files. The uninstall process now provides a detailed list of any files that it fails to remove and advises the user to remove the files manually.
During the installation of a rebranded Run-time Environment using the -v flag ( haspdinst.exe -i -v ), an internal error would be displayed (message: «An error occurred when the RTE installer attempted to unpack the file sm.cab»). Note that the -v flag is not a documented option, and that the installation would succeed despite the error message.
Given the following circumstances.
- A machine is not connected to the network
- Run-time Environment v.7.50 is installed on the machine.
- The Run-time Environment is removed with a purge command.
- You connect a Sentinel HL (HASP configuration) key to the machine.
The Run-time Environment would be automatically reinstalled.
Now, the Run-time Environment is not installed under these circumstances.
Issues Resolved in Version 7.51
| Reference | Description |
|---|---|
| SM-498 |
Given the following circumstances:
- A V2C file was applied to a new SL AdminMode license on a given machine.
- The same V2C was applied a second time to the license.
Instead of generating an error message and rejecting the update, the License Manager would generate the error message and then remove the original SL AdminMode license from the machine. (The license would be restored when the License Manager was restarted.)
Issues Resolved in Version 7.50
| Reference | Description |
|---|---|
| LDK-13933 | When installing Sentinel LDK Run-time Environment v7.41 or later under Windows 10 (x86), the file hlvdd.dll was not installed. As a result, the protected application would fail. |
| LDK-16215 | Each time the end user would connect a Sentinel HL (Driverless configuration) key to a different USB port on a Windows machine, the Driver Software Installation message box would indicate that a restart was required. |
| LDK-16443 |
Given the following circumstances:
- A file type is registered as “protected” using Version 1 data file protection.
- A file of the protected type is saved from the protected application using “Save as”.
Under certain circumstances, the saved file was not encrypted.
Given the following circumstances:
- A license server machine and the recipient machine are in different time zones
- A detachable license is transferred online from the server to the recipient machine.
The detached license would expire earlier than expected.
Given the following circumstances:
- An SL AdminMode or SL Legacy license is located on a physical machine.
- From a remote VM, hasp_get_info() is called to fetch values of the «disabled» and «usable» tags for the SL license.
The incorrect values disabled=true and usable= false were returned.
Given the following circumstances:
- SL Legacy licenses from two different vendors were present on a machine.
- The license from one of the vendors is removed.
- The License Manager service is restarted.
The remaining SL Legacy license was no longer visible in Admin Control Center.
Given the following circumstances:
- RTE version 6.60 or earlier is installed on a machine with no licenses.
- Retrieve the fingerprint of the machine.
- Upgrade the RTE to version 7.41
- Use the retrieved fingerprint to generate an SL AdminMode license.
- Apply the license with the upgraded RTE.
The license would be marked as “cloned”.
| Reference | Description |
|---|---|
| LDK-12479 | |
| LDK-12860 | When a fully-qualified domain name (FQDN) was provided in the login scope using a character set outside the Windows code page, the login would fail with error code 50 (Scope Result Empty). |
| LDK-13136 | Sentinel Licensing API would identify a Max Micro key as a Max key under certain circumstances. |
| LDK-13455 | |
| LDK-13926 | The branded RTE Installer that is generated by Sentinel EMS did not copy the haspvlib correctly to /var/hasplm/. As a result, when hasp_update attempted to apply a V2C file, error 48 was generated. |
| LDK-14274 | |
| LDK-14280 | HASP HL keys are not recognized correctly by the License Manager when keys from two or more vendors are connected to a given machine. |
| LDK-14805 | The Run-time Environment did not support RAID controllers that create symbolic links as DeviceRaidPort. |
| LDK-15306 | On the Diagnostics page of Admin Control Center, the Requests counter would count a request to local licenses as a remote request. |
| LDK-15307 | |
| LDK-15857 | |
| LDK-16113 | When a V2C file to clear the “cloned” status of an SL Legacy license was applied, The “clear clone” operation was not applied correctly until the user restarted the machine. |
| LDK-16215 | Driver software was reinstalled and the end user was prompted to restart the machine each time an HL (Driverless configuration) key was connected to a differed USB port on the machine. |
Issues Resolved in Version 7.41
| Reference | Description |
|---|---|
| LDK-12845 | Installation of Sentinel Run-time Environment version 7.40 on a machine with an obsolete version (11.5.x) of Intel RAID drivers would cause a Stop error (BSoD). |
Enhancements in Revision 7.40
| Reference | Description |
|---|---|
| LDK-6938 | The Run-time Environment now supports Sentinel HL Drive microSD keys. |
| LDK-8350 | The diagnostic report in Admin Control Center now provides additional information for Driverless keys and updated driver versions |
| LDK-10079 | The diagnostic panel in Admin Control Center now displays the version number for the Run-time Environment. |
| LDK-10107 | The Admin Control Center log file now indicates the version number for the Licensing API. |
| LDK-10279 | The button in Admin Control Center for generating C2V files is now blocked for HASP HL keys and Sentinel HL (HASP configuration) keys. |
| LDK-11034 | The Sentinel Keys page in Admin Control Center now displays the capacity of attached Sentinel Drive microSD keys. |
| LDK-11335 | Admin Control Center now displays the module name (in addition to the Feature ID) for Sentinel Master keys and Sentinel Developer keys. |
Issues Resolved in Version 7.40
| Reference | Description |
|---|---|
| LDK-7237 | Under certain circumstances, Admin Control Center would continue to show active sessions for an HL key after all sessions had logged out of the key. |
| LDK-8866 | Under certain circumstances, if SL license information became corrupted, Sentinel LDK License Manager Service would crash instead of issuing an error message. As a result, it was not possible for the vendor to correct the situation by sending a license update. |
| LDK-9797 | The Run-time Environment did not provide a meaningful error message when a given License Manager ID was found on multiple machines in the same network. This situation is typically caused by cloning a VM. As a result, it was difficult to identify the source of the problem when the licenses on these machine were inaccessible. Now an appropriate error message is generated. |
| LDK-9948 | Rehosting of an SL Legacy key to a different machine would fail with the return code HASP_CLONE_DETECTED. |
| LDK-10273 | Admin Control Center would allow a license to be detached even though the termination date for the detach was invalid. |
| LDK-10564 | The Vendor ID for a Master key was not the same in Admin Control Center pages and in the Diagnostics Reports. |
| LDK-10857 | When an iSCSI disk was connected to a Windows physical machine, the License Manager would regard the machine as a virtual machine. |
| LDK-11478 | After Run-time Environment v.7.32 was installed, running an application that was protected with Sentinel HASP Envelope (prior to Sentinel LDK 6.3) would cause a Stop error (BSoD). |
| LDK-11787 | Under certain circumstances, the Licensing API function hasp_get_info would always return a value of 0 as the value for for an SL license. Now the function returns the correct value for . |
| LDK-11825 | Admin Control Center was not able to display an invalid HL key. Now such a key is visible in Admin Control Center with an indication that the key is not valid. |
| LDK-12196 | When an SL key is installed on a machine with Run-time Environment 7.32 or 7.3, the Run-time Environment would continually open additional handles. |
Known Issues — Run-time Environment
Sentinel LDK communicates via TCP and UDP on port 1947. This port is IANA-registered exclusively for this purpose. At the end user site, the firewall must be configured so that communication via this port is not blocked.
When a computer names contains UTF-16 characters, Admin Control Center displays the short name for the computer (similar to Windows Explorer). Similarly, the sntl_admin_get function in Admin API returns the short name.
After Windows 7 is upgraded to Windows 8, the user is not able to use existing SL licenses or to install new SL licenses.
Workaround: After you upgrade from Windows 7 to Windows 8, reinstall the Run-time Environment.
Sentinel Licensing API: On a computer with the Nvidia chip set GeForce 7025/nForce 630a, and where the CPU is AMD Athlon 64 X2, the hasp_read and hasp_encrypt functions may fail with error 39, HASP_BROKEN_SESSION. This problem only exists with HASP HL keys with Firmware version 3.25.
Workaround 1: On the computer described above, when error 39 is returned, call the hasp_read or hasp_encrypt function again. It is not necessary to call hasp_login again.
Workaround 2: Use Sentinel HL keys with Firmware version 4.2x.
With some new USB chipsets, it is possible that the API hasp_update() call, used to update the firmware of Sentinel HL keys to version 3.25, will generate the HASP_BROKEN_SESSION return code, even if the firmware is correctly updated. (This issue does not occur with Sentinel HL Driverless keys with firmware version 4.x.)
Workaround: Install the latest Run-time Environment. The automatic firmware update feature of the License Manager will automatically update the firmware of the key the first time that the key is connected, without the need to call hasp_update().
For a Java 7 or Java 8 application that is protected with Envelope, the end user must use the following flag when launching the protected application:
- For Java 7: Specify -usesplitverifier
- For Java 8: Specify -noverify
If the appropriate flag is not specified, the application may throw java.verifyerror when launched.
The License Manager fails to load vlibs under Windows 10 when Device Guide is enabled and the Code Integrity policy is set to “enforce”. For more information, see Issues Related to Device Guard and Code Integrity Policies.
Sentinel LDK Vendor Tools fail to load under Windows 10 when Device Guide is enabled and the Code Integrity policy is set to «enforce». An error message is displayed regarding a certain DLL, stating that the DLL is not designed to run on Windows or that the DLL contains an error. For more information, see Issues Related to Device Guard and Code Integrity Policies.
Given the following circumstances at a customer site:
- One machine has Run-time Environment version 7.51.
- A second machine has a version of Run-time Environment that is earlier than 7.51.
- The customer performs rehost of a license repeatedly between the two machines.
- An update is applied to the license on either of these machines.
A rehost operation sometimes fails with the message HASP_REHOST_ALREADY_APPLIED.
Workaround: Obtain a new SL license from the software vendor for the protected application on the target machine. Before attempting any additional rehost procedure, install the latest Run-time Environment on both machines.
В© Gemalto 2018. All rights reserved. Gemalto, the Gemalto logo, are trademarks and service marks of Gemalto and are registered in certain countries.
Источник
Adblock
detector
| Reference | Description |
|---|---|
| 12506 |
How I solved “Unable to access HASP SRM Run-time Environment? (H0033)”
First of all, don’t stress! These instructions will most likely get you up and running with your 4D, 5D, 6D or other dongle-controlled program in short order.
Background
My wife asked me to install her Viking embroidery “5D” software on her Surface Pro PC so she could use the touch tablet and pen to do graphics drawing and editing in the Design Creator.
The software is protected by requiring the user to have a USB dongle plugged in when running the program.
Installation went through normal software install and then it also had 3 updates to install. Two of the updates seemed to end with an error, perhaps because I did not reboot the PC after each (it was not clear whether or not to do this). At any point, running the program with the dongle installed resulted in the H0033 error.
I tried doing a repair install and also install of drivers (from the main install menu) – neither helped.
Searching on this error showed several hits saying to go to the windows Services and enabling the HASP License Manager (or Sentinel HASP License Manager) but in my case, I did not have the HASP entry in Services.
I looked in the Device Manager and saw an error for the HASP device and its properties said the device driver was not installed. Doing an Uninstall followed by a Scan for New Hardware did not help.
Some posts said to try to go to this url in your browser: http://localhost:1947 but that just displayed an error. Normally, this would display the HASP SRM Admin Control Center.
Solution
I eventually found a post to download the HASP SRM Runtime drivers at https://sentinelcustomer.gemalto.com/sentineldownloads/ (or use the link below). Installing this did solve the H0033 error. Also, once installed, the dongle light was lit and the http://localhost:1947 worked.
From the download page, I chose to install the Sentinel HASP/LDK Windows GUI Run-time Installer. The zip file contains a Readme file and a HASPUserSetup.exe file. Run the exe file to start the installation. It’s pretty quick.
Copy of HASP SRM Runtime download zip file:
When I installed the driver, I did not have the dongle plugged in. After the install, I tried going to the the localhost url above and it worked (displayed a page, not an error). I then plugged in the dongle and it lit up and the localhost url displayed more mildly interesting information.
Read the feedback (over 100 posts) and you will see virtually everybody is successful with this procedure. Please post feedback on your results.
Share Post
Gary Davis
DotNET/PayPal Development and other Techie Stuff
Источник
Troubleshooting
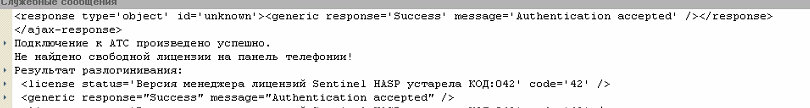
License key is not connected.
Connected license key’s batch code is different from required one (a license key of another software vendor is used).
Connect the license key provided by VIT.
When network license key is required, the license key being connected does not enable the protected software.
Check if the license key that is being connected is a network key (usually red) and, if not, connect the network protection key.
Sentinel LDK Run-time environment (hasplms.exe process) is not installed on the computer where protected software is to run.
See the instructions:
Network traffic is blocked at Port 475 on the computer where the license key is installed and/or protected software is running (due to Windows Firewall or, for example, antivirus software).
Disable all the software that may block access to your license key or add a blocked object into a list of exceptions (whether it is Port 475, Sentinel LDK Run-time service or other software blocked).
“Feature not found (H0031)” error
The license key does not have any information about Program Number/Feature ID requested by protected application.
Update the license key:
On your computer, two license keys with the same batch codes are installed. The key that was detected and currently enables the protected application does not have the feature(s) needed by that application.
For hardware license keys: connect available keys one-by-one to see which of them enables protected functionality of your application.
Also, read more on this conflict (the Important 2 block).
“Unable to access HASP SRM RunTime Environment (H0033)” error
C:WINDOWSsystem32hasplms.exe is blocked by the Firewall or antivirus software.
Add the Sentinel LDK Run-time environment to the blocking exceptions list.
Port 1947 is blocked by the Firewall. Add the port to the blocking exceptions list.
Sentinel LDK Run-time environment (hasplms.exe)
stopped working.
Relaunch the environment’s process.
“Terminal services detected, cannot run without a dongle (H0027)” error
Occurs when terminal services are detected. For example, Microsoft Terminal Server (including Remote Desktop services), Citrix Winframe/Metaframe etc.
Your license key should not be connected to a computer that has active terminal software installed.
VIT controls this option by allowing or prohibiting its products operation on terminal servers. If such option is needed, request for the license key update:
“Your license has expired (H0041)” error
Update the license key:
| Cause | Solution |
|---|---|
| The license has expired. | |
| System time on the computer was changed manually. |
«UpdateTooOld»
Trying to install a V2C file with an update counter that is out of sequence with update counter in the Sentinel protection key. Values of update counter in file are lower than those in Sentinel protection key.
«UpdateTooNew»
Trying to install a V2C file with an update counter that is out of sequence with the update counter in the Sentinel protection key. First value in file is more-than-1 greater than value in Sentinel protection key.
When licensing information contained in a v2c-file is to update (rewrite) the information contained in the corresponding license key, that new information must be applied strictly in a sequence of corresponding c2v-files generation.
Check if you are applying several license updates in a right order and whether all of them are present and none skipped. If everything seems to be applied correctly, but the error still occurs, contact your manager: there might be something overlooked while v2c-files generation on VIT’s side. Possible solution may be to format your license key and write a new license information into it from scratch.
Источник
Sentinel В® LDK Environment Installer GUI for Windows: Readme
Version 7.81
July 2018
This document provides information regarding the Run-time Environment Installer GUI for Sentinel LDK and Sentinel HASP, including supported operating systems, enhancements, known compatibility issue, and issues resolved. («Sentinel LDK» is the next generation of Sentinel HASP.)
The following topics are discussed:
Operating Systems Supported
- Windows 7 SP1
- Windows 7 SP1 Embedded standard (x86)
- Windows 8.1 SP1
- Windows Server 2008 R2 SP1
- Windows Server 2012 R2
- Windows Server 2016
- Windows 10 Version 1803
Note: Windows 10 Insider Preview builds are not supported.
The operating system versions listed in this section were tested by Gemalto and verified to be fully compatible with Sentinel LDK. For reasons of compatibility and security, Gemalto recommends that you always keep your operating system up to date with the latest fixes and service packs.
The installer detects the version of the operating system at run-time, before installing the relevant drivers.
Virtual Environments Supported
For a list of the virtual environments supported, see «Supported Platforms for End Users» in the Sentinel LDK Release Notes.
Upgrading the Run-time Environment
When using the Installer GUI to upgrade the Run-time Environment, ensure that:
- No other Run-time Environment Installer is active.
- No other Run-time Environment components are active. Although the installation program terminates applications that are accessing the Run-time, it does not terminate running services. For example, if the Sentinel License Manager is running as a service, you must stop the service before upgrading the Run-time Environment.
Installing the Run-time Environment
- The Installer GUI detects the version of the operating system during Run-time Environment installation, before installing the relevant drivers.
- By default, Windows displays a User Account Control message during driver installation. The user must click Continue to continue the installation. Alternatively, the user can change the default setting from the Control Panel of their operating system.
- A log file of the installation process is written to aksdrvsetup.log in the Windows directory.
For additional information, see “2.17 — Upgrading Sentinel LDK Run-Time Environment (RTE) Installer” in the Sentinel EMS Configuration Guide.
Allowing Incoming Connections From Public Networks Using Port 1947
The Run-time Environment Installer adds a firewall rule named “Sentinel License Manager” that allowed incoming connections from private networks using port 1947.
You can manually allow access from public networks using this port, but Gemalto highly recommends against this.
If you do plan to allow incoming connections from public networks using port 1947, create a rule with a different name in order to prevent future RTE upgrades from removing this access.
Issues Related to Device Guard and Code Integrity Policies
The traditional method until now to protect against malicious application under Windows has been to trust the applications unless they were blocked by an antivirus or other security solution. Device Guard, available in Windows 10 Enterprise, implements a mode of operation in which the operating system trusts only applications that are authorized by your enterprise. You designate these trusted applications by creating code integrity policies.
You can maintain a whitelist of software that is allowed to run (a configurable code integrity policy), rather than trying to stay ahead of attackers by maintaining a constantly-updated list of «signatures» of software that should be blocked. This approach uses the trust-nothing model well known in mobile device operating systems.
Only code that is verified by Code Integrity, usually through the digital signature that you have identified as being from a trusted signer, is allowed to run. This allows full control over allowed code in both kernel and user mode.
Code integrity contains two primary components:
- kernel mode code integrity (KMCI)
- user mode code integrity (UMCI)
This section describes issues that arise and the workarounds when machines at the end user site are enabled with Device Guard, and the code integrity policy set to “enforce” mode.
Note: The procedures described in this document should be performed by an IT professional who is familiar with Device Guard and code integrity policies.
Issue 1: Windows blocks the installation of the Run-time Environment
During installation of the Run-time Environment on your computer, Windows displays a message similar to this: «Your organization used Device Guard to block this app. Contact your support person for more info.»
Solution:
To install the Run-time Environment on a machine where Device Guard is enabled in enforce mode (which make use of PcaCertificate level code signing check), ensure that DigiCert is listed/added in the Signers list of the policy file.
Import the DigiCert Intermediate certificate to the trusted list of Intermediate Certification Authorities(ICA) store on the golden computer before creating code integrity policy.
A Digicert Intermediate certificate is available from https://aboutssl.org/digicert-trusted-root-authority-certificates/#intermediates. Under Intermediate Certificates, locate and download the DigiCert EV Code Signing CA (SHA2) certificate. You can also fetch this intermediate certificate from your trusted source.
To add the DigiCert Root Certificate:
- Download the certificate on the golden computer and double-click the certificate file. The Certificate dialog box is displayed.
- Click Install Certificate. Follow the Certificate Install Wizard to complete the import of this certificate to the ICA store.
- Run the steps to create a new or updated policy. This will allow Sentinel software to be installed without any issues on a machine where Device Guard is enabled.
Repeat the installation of the Run-time Environment.
Issue 2: Protected application does not operate at the customer site
(LDK-17267) ) When you distribute applications that are protected with SL keys, the customized vendor library (haspvlib_vendorID.*) that are required for these applications are not signed. As a result, Device Guard does not allow the software to operate at the customer site.
Workaround A:
This workaround must be performed at the customer site.
Do the following to add an exception for the customized vendor library file in the code integrity policy:
- Use Windows PowerShell in elevated mode to create a policy for the exception.
- Use the Group Policy editor to deploy the policy file.
To create the policy for the exception:
- Open PowerShell in elevated mode.
- Run the command to create a policy (referred to below as P1) in audit mode.
- Deploy this policy.
- Operate the protected application as you would normally.
- Create another policy (referred to as P2) that captures audit information from the events log.
Note: Before proceeding with the next step, review policy P2 carefully. This policy contains information about all the binaries that were used in your system while you operated the protected application. Any unwanted application that was executed during this time is logged in the policy. If not removed, any such application will be treated as a trusted binary. - Merge policies P1 and P2.
- Disable audit mode.
- Deploy the merged policy.
To deploy the policy file:
- Open the Group Policy editor by running GPEdit.msc.
- Navigate to: Computer ConfigurationAdministrative TemplatesSystemDevice Guard
- Select Deploy Code Integrity Policy. Enable this setting by using the path to the relevant policy file created above.
Workaround B (not recommended):
This workaround must be performed at the customer site.
Before deploying the code integrity policy, disable UMCI (user mode code integrity) mode.
To accomplish this, run the following command in Windows PowerShell in elevated mode:
Set-RuleOption -FilePath
-Option 0 -Delete
Issue 3: Vendor Tools fail to load
(SM-907) Sentinel LDK Vendor Tools fail to load. An error message is displayed, stating that a DLL, LIB, COM, or EXE file is not designed to run on Windows or that the DLL contains an error.
Workaround A:
Do the following to add a policy for the Sentinel LDK Vendor Tools in the code integrity policy file:
- Use Windows PowerShell in elevated mode to create a policy for the Vendor Tools.
- Use the Group Policy editor to deploy the policy file.
To create the policy for the Vendor Tools:
- Open PowerShell in elevated mode.
- Run the command to create a policy (referred to below as P1) in audit mode.
- Deploy this policy.
- Execute all of the Vendor Tools that you will require at your site and perform all of the functions in these tools that you will require. If you miss any required Vendor Tools or Vendor Tool functions, the required entries will not be added in the new code integrity policy, and these tools or functions will generate an error message when they are eventually used.
- Create another policy (referred to as P2) that captures audit information from the events log.
Note: Before proceeding with the next step, review policy P2 carefully. This policy contains information about all the binaries that were used in your system while you operated the Vendor Tools. Any unwanted application that was executed during this time is logged in the policy. If not removed, any such application will be treated as a trusted binary. - Merge policies P1 and P2.
- Disable audit mode.
- Deploy the merged policy.
To deploy the policy file:
- Open the Group Policy editor by running GPEdit.msc.
- Navigate to: Computer ConfigurationAdministrative TemplatesSystemDevice Guard
- Select Deploy Code Integrity Policy. Enable this setting by using the path to the relevant policy file created above.
Workaround B (not recommended):
Perform this workaround at your development site.
Before deploying the code integrity policy, disable UMCI (user mode code integrity) mode.
To accomplish this, run the following command in Windows PowerShell in elevated mode:
Set-RuleOption -FilePath
-Option 0 -Delete
No further actions are required.
Issue 4: Digital signature removed from the RTE Installer
(SM-18780) When a user creates a Run-time Environment Installer using Sentinel EMS, the digital signature is removed from the Installer. As a result, Device Guard blocks the RTE Installer from executing.
If the vendor downloads the installer as an EXE file and signs it, Device Guard allows the installer to run, but the installation fails due to an unsigned DLL file called by haspdinst.exe.
Workaround:
Perform the procedure that follows.
- Download the Run-time Environment Installer from the following URL in the Gemalto web site:
To work with Sentinel EMS, continue with the following additional steps:
- In a Web browser, enter the following to start Admin Control Center: http://localhost:1947
- On the Configuring Network Settings page, in the EMS URL field, enter the URL to access the Sentinel EMS Service.
- Click Submit.
- Proceed to work with Sentinel EMS as required.
As an alternative, you can use one of the workarounds provided above for issues 2 and 3.
Enhancements and Issues Resolved in This Release
Enhancements
The RTE Installer now provides more details in order to help ensure that installation of the RTE completes successfully. The Installer now differentiates between the following situations:
- Installation of the RTE has succeeded. No restart is required.
- Installation of the RTE cannot complete due to a lock on a required file. The RTE Installer attempts to rename the locked file in the background. If it succeeds, the installation will continue. If the rename attempt fails, the installer returns error 52. At this point, your code can call the new RTE Installer API function haspds_GetLockingProcessList to get the locking process name. You can then release the locked file and restart the RTE Installer.
Several security improvements have been implemented.
Issues Resolved
| Reference | Description |
|---|---|
| SM-18163 | |
| SM-27901 | The revision history of all enhancements implemented and issues resolved for earlier versions of the RTE is now available online at: http://sentinelldk.safenet-inc.com/Default.htm |
| SM-30222 SM-30886 |
The hasp_login function would fail to log in to a HASP4 parallel port key (the function would not fail with HASP4 SUB keys). The login would fail with the error code HASP_HASP_NOT_FOUND = 7. This issue would occur with RTE version 7.52 and later.
| Reference | Description |
|---|---|
| SM-28148 | |
| SM-31010 | If the client connected using different IPv6 interfaces, the License Manager would sometimes count the sessions on a machine multiple times. |
Security Updates in This Release
There are no known and unresolved security issue relating to Sentinel products in this release.
For the latest information regarding any older or newly-discovered issues, see this Web page:
Reporting a Security Vulnerability
If you think you have found a security vulnerability, please send it to Gemalto using the links provided on the Web page provided above.
Revision History
This section describes enhancements implemented and issues resolved in the last three major releases of Sentinel Run-time Environment.
The revision history for earlier versions of Sentinel Run-time Environment is available at: http://sentinelldk.safenet-inc.com/Default.htm
Issues Resolved in Version 7.80
If a customer applies a V2C update from a remote machine that has the Vendor library but no license from the same vendor, the error returned was HASP_UPDATE_TOO_NEW, which was confusing. Now the error returned is HASP_KEYID_NOT_FOUND.
The RTE installer adds a firewall rule (named “Sentinel License Manager”) that, in the past, allowed incoming connections from any network, including public networks, using port 1947. Starting with RTE version 7.80, the firewall rule added by the RTE Installer does not allow incoming connections from public networks. If you are upgrading from an earlier version of RTE, the installer replaces the existing rule (that allows connections from public networks) with a rule that blocks such connections.
You can manually allow access using this port from public networks, but Gemalto highly recommends against this.
If you do plan to allow access from public networks using port 1947, create a rule with a different name in order to prevent future RTE upgrades from removing this access.
| Reference | Description |
|---|---|
| SM-12155 | |
| SM-18502 | Defining an excessive number of User Restrictions in Admin Control Center would cause the License Manager Service to fail. |
| SM-19981 | hasp_update would return an internal error for an HL Key when the license definition contains empty content in the default memory section. |
| SM-23609 | |
| SM-25600 | The Run-Time Environment would require an excessive amount of time to install. |
| SM-26543 | Under certain circumstances, Sentinel License Manager would crash on the REST interface with long packets. |
| SM-9841 | HASP4 keys would stop working after the Run-time Environment was upgraded to v.7.54. |
Issues Resolved in Version 7.65
A possible security issue related to buffer overflow (reported by Kaspersky) has been resolved.
| Reference | Description |
|---|---|
| SM-21408 | The Admin Control Center help system was missing information regarding the new “Idle Timeout of Session” configuration parameter. |
| SM-23320 | A possible security issue related to License Manager failure due to stack overflow on deep XML data (reported by Kaspersky) has been resolved. |
| SM-23402 | |
| SM-23813 | A possible security issue that was reported by Kaspersky has been resolved. |
Enhancements in Version 7.63
In the past, the timeout for an idle License Manager session was fixed at 12 hours. You can now set the timeout to any value between 10 minutes and 720 minutes (12 hours). The timeout value can be set as follows:
- In Admin Control Center, on the Basic Configuration page. Use the Idle Timeout of Session parameter.
- In the hasplm.ini file. Assign the timeout value to idle_session_timeout_mins.
Admin Control Center now adds the update counter in C2V files in clear text — for example: 5
It is no longer necessary to decode the C2V file in order to view this information.
| Reference | Description |
|---|---|
| SM-13443 | When a Sentinel HL (HASP configuration) key or HASP HL key is attached to a Windows machine, the Run-time Environment is no longer installed automatically by Windows Update. It is now the software vendor’s responsibility to ensure that the Run-time Environment is installed when required. |
| SM-13505 | |
| SM-14894 | |
| SM-19483 | Admin Control Center now recognizes the new V2CP format to update protection keys. This supports planned enhancements in Sentinel LDK v.7.8. |
Issues Resolved in Version 7.63
The Run-time Environment now supports the use of the VMType3 clone protection scheme.
Enhancements in Version 7.60
| Reference | Description |
|---|---|
| SM-15922 | Admin Control Center no longer requires the |
| Reference | Description |
| SM-5318 |
You can now enter the URL to access Sentinel EMS in your Web browser without changing the EMS URL to lowercase.
Admin Control Center (under Windows) can now display and apply updates to local SL UserMode keys. (Session information and certificate information for SL UserMode keys is not displayed.)
To display SL UserMode keys in Admin Control Station, License Manager runs an additional process (hasplmv) on the machine. If you are willing to accept that SL UserMode keys will not be displayed, you have the option to prevent hasplmv from executing by clearing the relevant check box on the Configuration page in Admin Control Center.
In the past, Admin Control Center and Admin API provided a configuration parameter that determined whether a remote user could access and perform actions in Admin Control Center. However, this parameter did not control remote access to Admin API.
Now, the parameter Allow Remote Access to ACC and Admin API (in Admin Control Center) and the tag (in Admin API) control remote access to both Admin Control Center and Admin API.
Issues Resolved in Version 7.60
| Reference | Description |
|---|---|
| SM-1286 |
When a data file is protected with Version 2 data protection mode for Android platforms: If, for any reason (for example, no license was found), the protected application was not able to decrypt the protected data file, no error message was generated to explain why the file cannot be opened.
Under Windows 10, a physical machine would be detected as a virtual machine when only Hyper-V Hypervisor is enabled.
The Diagnostics report in Admin Control Center (Diagnostics > Generate Report) displays information on «Recent Clients» and «Recent Users». Each entry contained a time stamp but not a date stamp. The report has been corrected to display both a time stamp and a date stamp for each entry.
When building a Run-Time Environment installer using Wix, an error message similar to the following was generated:
Invalid product version ‘7.53.1.66350’ in package HASP_Setup.msi’. When included in a bundle, all product version fields in an MSI package must be less than 65536.
This error no longer occurs.
Under certain circumstances, Sentinel LDK License Manager Service would crash. The exception code would map to STATUS_STACK_OVERFLOW in __chkstk API.
Enhancements in Version 7.55
| Reference | Description |
|---|---|
| LDK-12145 | |
| SM-515 | It was possible to rehost a cloned license to another machine. |
| SM-518 |
Sentinel Admin Control Center can now be used to configure the License Manager for the following additional considerations:
- Allow specific named users to access specific Batch Codes, protection keys (haspID), or Product IDs.
- Use the «*» wildcard character for IP and hostname.
- Use subnet mask notation (for example: 172.18.8.0/21) for IP addresses
For more information, see «Configuring User Settings» in the Admin Control Center online help.
Issues Resolved in Version 7.55
| Reference | Description |
|---|---|
| SM-4748 |
Various crash conditions in the License Manager that could be used for denial-of-service attacks or privilege-escalation attacks have been resolved.
When a user issues a «detach license» request from a remote Admin Control Center, the user name cannot be included in request. As a result, User Restrictions (defined in ACC on the license server machine) that are based on the user name are handled as follows:
- “allow” user restrictions that are based on a specific user name are not applied because the user name is not available to the License Manager on the license server. If a different restriction such as deny=all@all is also specified, the detach request will be denied.
- If any “deny” user restriction that is applicable for the request in all respects other than username exists, that restriction is applied even if the user name specified in the restriction does not match. For example: If the detach request was sent from a machine with the hostname host123, and a user restriction has been specified deny=skr@host123 on the license server machine, the detach request is denied even the user requesting the detach has a different username.
Sentinel Admin Control Center online help has been updated to describe these limitations.
Enhancements in Version 7.54
| Reference | Description |
|---|---|
| SM-4942 |
| Reference | Description |
|---|---|
| SM-889 | Run-time Environment is supported under Windows Server 2016. |
Issues Resolved in Version 7.54
Installation of a rebranded RTE would fail when the account name contains multi-byte characters (such as Japanese). The install log would contain an error similar to the following:
could not open C:UsersuserNameAppDataLocalTempEMSUrl.properties ../hhlinst.c,4659
OPEN file C:UsersuserNameAppDataLocalTempEMSUrl.properties processing error. ../hhlinst.c,4660,
The decrypt function in the HASP4 API would give incorrect results after RTE 7.52 or 7.53 was installed.
| Reference | Description |
|---|---|
| SM-2090 | |
| SM-3767 | After installation of RTE 7.53, hasplms was unreachable to remote clients. The RTE installer did not add the firewall rule to allow Sentinel License Manager Service. |
Issues Resolved in Version 7.53
Given the following scenario:
- Obtain a C2V file for an SL Legacy key.
- Prepare an update to upgrade the SL Legacy key to an SL AdminMode key in Sentinel License Generation API, but do not apply the update.
- Prepare a second update using the first update as the current state for the key.
- Apply the second update to the key.
The update would return a status of OK even though the update fails.
Given the following scenario:
- Connect a Sentinel HL (HASP configuration) key to a machine and generate a C2V file for the key.
- Create an update in Sentinel License Generation API to upgrade the key to a Sentinel HL (Driverless configuration) key, but do not apply the update.
- Prepare a second update to the key using the first update as the current state for the key.
- Apply the second update to the key.
The update would return a status of OK even though the update fails.
Enhancements in Version 7.52
| Reference | Description |
|---|---|
| SM-1201 |
The Features page in Admin Control Center now displays the peak number of consumed seats per Feature. The peak number is based on the current License Manager session. For each Feature, the peak number value is displayed as a tool tip for the seats value under the Logins column. This information enables end users and organizations to determine if the number of seats purchased is suitable for their needs.
The Run-time Environment can now be installed under Windows 10 when Device Guard is enabled.
Issues Resolved in Version 7.52
| Reference | Description |
|---|---|
| LDK-15786 |
A Sentinel HL (HASP configuration) key would not be accessible by the protected application under the following circumstances:
The following conditions exist:
- Windows 10 version 1607 is present on the machine.
- The network is disabled.
- The Run-time Environment is not present on the machine.
The following actions are performed:
- The HL key is connected to the machine and then disconnected.
- The Run-time Environment is installed on the machine.
- The HL key is connected again to the machine.
The HL key would not be accessible.
When using RTE 7.51, a Stop error (BSoD) would occur when the protected application attempted to retrieve the serial number of the disk drive that uses Intel RAID drivers.
Under certain circumstances, the uninstall of the Run-time Environment on a Windows 8 machine would fail.
The uninstall of the Run-time Environment would not provide proper notification if it failed to remove all necessary files. The uninstall process now provides a detailed list of any files that it fails to remove and advises the user to remove the files manually.
During the installation of a rebranded Run-time Environment using the -v flag ( haspdinst.exe -i -v ), an internal error would be displayed (message: «An error occurred when the RTE installer attempted to unpack the file sm.cab»). Note that the -v flag is not a documented option, and that the installation would succeed despite the error message.
Given the following circumstances.
- A machine is not connected to the network
- Run-time Environment v.7.50 is installed on the machine.
- The Run-time Environment is removed with a purge command.
- You connect a Sentinel HL (HASP configuration) key to the machine.
The Run-time Environment would be automatically reinstalled.
Now, the Run-time Environment is not installed under these circumstances.
Issues Resolved in Version 7.51
| Reference | Description |
|---|---|
| SM-498 |
Given the following circumstances:
- A V2C file was applied to a new SL AdminMode license on a given machine.
- The same V2C was applied a second time to the license.
Instead of generating an error message and rejecting the update, the License Manager would generate the error message and then remove the original SL AdminMode license from the machine. (The license would be restored when the License Manager was restarted.)
Issues Resolved in Version 7.50
| Reference | Description |
|---|---|
| LDK-13933 | When installing Sentinel LDK Run-time Environment v7.41 or later under Windows 10 (x86), the file hlvdd.dll was not installed. As a result, the protected application would fail. |
| LDK-16215 | Each time the end user would connect a Sentinel HL (Driverless configuration) key to a different USB port on a Windows machine, the Driver Software Installation message box would indicate that a restart was required. |
| LDK-16443 |
Given the following circumstances:
- A file type is registered as “protected” using Version 1 data file protection.
- A file of the protected type is saved from the protected application using “Save as”.
Under certain circumstances, the saved file was not encrypted.
Given the following circumstances:
- A license server machine and the recipient machine are in different time zones
- A detachable license is transferred online from the server to the recipient machine.
The detached license would expire earlier than expected.
Given the following circumstances:
- An SL AdminMode or SL Legacy license is located on a physical machine.
- From a remote VM, hasp_get_info() is called to fetch values of the «disabled» and «usable» tags for the SL license.
The incorrect values disabled=true and usable= false were returned.
Given the following circumstances:
- SL Legacy licenses from two different vendors were present on a machine.
- The license from one of the vendors is removed.
- The License Manager service is restarted.
The remaining SL Legacy license was no longer visible in Admin Control Center.
Given the following circumstances:
- RTE version 6.60 or earlier is installed on a machine with no licenses.
- Retrieve the fingerprint of the machine.
- Upgrade the RTE to version 7.41
- Use the retrieved fingerprint to generate an SL AdminMode license.
- Apply the license with the upgraded RTE.
The license would be marked as “cloned”.
| Reference | Description |
|---|---|
| LDK-12479 | |
| LDK-12860 | When a fully-qualified domain name (FQDN) was provided in the login scope using a character set outside the Windows code page, the login would fail with error code 50 (Scope Result Empty). |
| LDK-13136 | Sentinel Licensing API would identify a Max Micro key as a Max key under certain circumstances. |
| LDK-13455 | |
| LDK-13926 | The branded RTE Installer that is generated by Sentinel EMS did not copy the haspvlib correctly to /var/hasplm/. As a result, when hasp_update attempted to apply a V2C file, error 48 was generated. |
| LDK-14274 | |
| LDK-14280 | HASP HL keys are not recognized correctly by the License Manager when keys from two or more vendors are connected to a given machine. |
| LDK-14805 | The Run-time Environment did not support RAID controllers that create symbolic links as DeviceRaidPort. |
| LDK-15306 | On the Diagnostics page of Admin Control Center, the Requests counter would count a request to local licenses as a remote request. |
| LDK-15307 | |
| LDK-15857 | |
| LDK-16113 | When a V2C file to clear the “cloned” status of an SL Legacy license was applied, The “clear clone” operation was not applied correctly until the user restarted the machine. |
| LDK-16215 | Driver software was reinstalled and the end user was prompted to restart the machine each time an HL (Driverless configuration) key was connected to a differed USB port on the machine. |
Issues Resolved in Version 7.41
| Reference | Description |
|---|---|
| LDK-12845 | Installation of Sentinel Run-time Environment version 7.40 on a machine with an obsolete version (11.5.x) of Intel RAID drivers would cause a Stop error (BSoD). |
Enhancements in Revision 7.40
| Reference | Description |
|---|---|
| LDK-6938 | The Run-time Environment now supports Sentinel HL Drive microSD keys. |
| LDK-8350 | The diagnostic report in Admin Control Center now provides additional information for Driverless keys and updated driver versions |
| LDK-10079 | The diagnostic panel in Admin Control Center now displays the version number for the Run-time Environment. |
| LDK-10107 | The Admin Control Center log file now indicates the version number for the Licensing API. |
| LDK-10279 | The button in Admin Control Center for generating C2V files is now blocked for HASP HL keys and Sentinel HL (HASP configuration) keys. |
| LDK-11034 | The Sentinel Keys page in Admin Control Center now displays the capacity of attached Sentinel Drive microSD keys. |
| LDK-11335 | Admin Control Center now displays the module name (in addition to the Feature ID) for Sentinel Master keys and Sentinel Developer keys. |
Issues Resolved in Version 7.40
| Reference | Description |
|---|---|
| LDK-7237 | Under certain circumstances, Admin Control Center would continue to show active sessions for an HL key after all sessions had logged out of the key. |
| LDK-8866 | Under certain circumstances, if SL license information became corrupted, Sentinel LDK License Manager Service would crash instead of issuing an error message. As a result, it was not possible for the vendor to correct the situation by sending a license update. |
| LDK-9797 | The Run-time Environment did not provide a meaningful error message when a given License Manager ID was found on multiple machines in the same network. This situation is typically caused by cloning a VM. As a result, it was difficult to identify the source of the problem when the licenses on these machine were inaccessible. Now an appropriate error message is generated. |
| LDK-9948 | Rehosting of an SL Legacy key to a different machine would fail with the return code HASP_CLONE_DETECTED. |
| LDK-10273 | Admin Control Center would allow a license to be detached even though the termination date for the detach was invalid. |
| LDK-10564 | The Vendor ID for a Master key was not the same in Admin Control Center pages and in the Diagnostics Reports. |
| LDK-10857 | When an iSCSI disk was connected to a Windows physical machine, the License Manager would regard the machine as a virtual machine. |
| LDK-11478 | After Run-time Environment v.7.32 was installed, running an application that was protected with Sentinel HASP Envelope (prior to Sentinel LDK 6.3) would cause a Stop error (BSoD). |
| LDK-11787 | Under certain circumstances, the Licensing API function hasp_get_info would always return a value of 0 as the value for for an SL license. Now the function returns the correct value for . |
| LDK-11825 | Admin Control Center was not able to display an invalid HL key. Now such a key is visible in Admin Control Center with an indication that the key is not valid. |
| LDK-12196 | When an SL key is installed on a machine with Run-time Environment 7.32 or 7.3, the Run-time Environment would continually open additional handles. |
Known Issues — Run-time Environment
Sentinel LDK communicates via TCP and UDP on port 1947. This port is IANA-registered exclusively for this purpose. At the end user site, the firewall must be configured so that communication via this port is not blocked.
When a computer names contains UTF-16 characters, Admin Control Center displays the short name for the computer (similar to Windows Explorer). Similarly, the sntl_admin_get function in Admin API returns the short name.
After Windows 7 is upgraded to Windows 8, the user is not able to use existing SL licenses or to install new SL licenses.
Workaround: After you upgrade from Windows 7 to Windows 8, reinstall the Run-time Environment.
Sentinel Licensing API: On a computer with the Nvidia chip set GeForce 7025/nForce 630a, and where the CPU is AMD Athlon 64 X2, the hasp_read and hasp_encrypt functions may fail with error 39, HASP_BROKEN_SESSION. This problem only exists with HASP HL keys with Firmware version 3.25.
Workaround 1: On the computer described above, when error 39 is returned, call the hasp_read or hasp_encrypt function again. It is not necessary to call hasp_login again.
Workaround 2: Use Sentinel HL keys with Firmware version 4.2x.
With some new USB chipsets, it is possible that the API hasp_update() call, used to update the firmware of Sentinel HL keys to version 3.25, will generate the HASP_BROKEN_SESSION return code, even if the firmware is correctly updated. (This issue does not occur with Sentinel HL Driverless keys with firmware version 4.x.)
Workaround: Install the latest Run-time Environment. The automatic firmware update feature of the License Manager will automatically update the firmware of the key the first time that the key is connected, without the need to call hasp_update().
For a Java 7 or Java 8 application that is protected with Envelope, the end user must use the following flag when launching the protected application:
- For Java 7: Specify -usesplitverifier
- For Java 8: Specify -noverify
If the appropriate flag is not specified, the application may throw java.verifyerror when launched.
The License Manager fails to load vlibs under Windows 10 when Device Guide is enabled and the Code Integrity policy is set to “enforce”. For more information, see Issues Related to Device Guard and Code Integrity Policies.
Sentinel LDK Vendor Tools fail to load under Windows 10 when Device Guide is enabled and the Code Integrity policy is set to «enforce». An error message is displayed regarding a certain DLL, stating that the DLL is not designed to run on Windows or that the DLL contains an error. For more information, see Issues Related to Device Guard and Code Integrity Policies.
Given the following circumstances at a customer site:
- One machine has Run-time Environment version 7.51.
- A second machine has a version of Run-time Environment that is earlier than 7.51.
- The customer performs rehost of a license repeatedly between the two machines.
- An update is applied to the license on either of these machines.
A rehost operation sometimes fails with the message HASP_REHOST_ALREADY_APPLIED.
Workaround: Obtain a new SL license from the software vendor for the protected application on the target machine. Before attempting any additional rehost procedure, install the latest Run-time Environment on both machines.
В© Gemalto 2018. All rights reserved. Gemalto, the Gemalto logo, are trademarks and service marks of Gemalto and are registered in certain countries.
Источник
Adblock
detector
| Reference | Description |
|---|---|
| 12506 |
Version 7.41
October 2015
This document provides
information regarding the Run-time Environment Installer GUI for
Sentinel LDK and Sentinel HASP, including supported operating systems,
enhancements, known compatibility issue, and issues resolved.
(«Sentinel LDK» is the next generation of Sentinel HASP.)
The following topics are discussed:
- Operating Systems Supported
- Upgrading the Run-time Environment
- Installing the Run-time Environment
- Issues Resolved in This Release
- Revision History
- Known Issues — Run-time
Environment
Operating Systems Supported
- Windows XP (X86) SP3
- Windows XP (X64) SP2
- Windows Vista SP2
- Windows 7 SP1
- Windows 8.1 SP1
- Windows 10
- Windows Server 2003 SP2
- Windows Server 2008 SP2
- Windows Server 2008 R2 SP1
- Windows Server 2012 R2
- Windows 7 SP1 Embedded
standard (x86)
The operating system versions listed in this section were tested by SafeNet and verified to be fully compatible with Sentinel LDK. Older operating system versions are likely to be fully compatible as well, but are not guaranteed. For reasons of compatibility and security, SafeNet recommends that you always keep your operating system up to date with the latest fixes and service packs.
Back to Topics
Upgrading the Run-time
Environment
When using the Installer GUI to
upgrade the Run-time Environment, ensure that:
- No other Run-time
Environment Installer is active. - No other Run-time
Environment components are active. Although the installation program
terminates applications that are accessing the Run-time, it does not
terminate running services. For example, if the Sentinel License
Manager is running as a service, you must stop the service before
upgrading the Run-time Environment.
Back to Topics
Installing the Run-time
Environment
- The Installer GUI detects
the version of the operating system during Run-time Environment
installation, before installing the relevant drivers. - By default, Windows Vista
(and later) operating systems display a User
Account Control message during
driver installation. The user must click Continue
to continue the installation. Alternatively, the user can change the
default setting from the Control Panel of their operating system. - A log file of the
installation process is written to aksdrvsetup.log
in the Windows directory.
Back to Topics
Issues Resolved in This Release
| Reference | Description |
|---|---|
| LDK-12845 | Installation of Sentinel Run-time Environment version 7.40 on a machine with an obsolete version (11.5.x) of Intel RAID drivers would cause a Stop error (BSoD). |
Back to Topics
Revision History
Enhancements in Revision 7.40
| Reference | Description |
|---|---|
| LDK-6938 | The Run-time Environment now supports Sentinel HL Drive microSD keys. |
| LDK-8350 | The diagnostic report in Admin Control Center now provides additional information for driverless keys and updated driver versions |
| LDK-10079 | The diagnostic panel in Admin Control Center now displays the version number for the Run-time Environment. |
| LDK-10107 | The Admin Control Center log file now indicates the version number for the Licensing API. |
| LDK-10279 | The button in Admin Control Center for generating C2V files is now blocked for HASP HL keys and Sentinel HL (HASP configuration) keys. |
| LDK-11034 | The Sentinel Keys page in Admin Control Center now displays the capacity of attached Sentinel Drive microSD keys. |
| LDK-11335 | Admin Control Center now displays the module name (in addition to the Feature ID) for Sentinel Master keys and Sentinel Developer keys. |
Issues Resolved in Version 7.40
| Reference | Description |
|---|---|
| LDK-7237 | Under certain circumstances, Admin Control Center would continue to show active sessions for an HL key after all sessions had logged out of the key. |
| LDK-8866 | Under certain circumstances, if SL license information became corrupted, Sentinel LDK License Manager Service would crash instead of issuing an error message. As a result, it was not possible for the vendor to correct the situation by sending a license update. |
| LDK-9797 | The Run-time Environment did not provide a meaningful error message when a given License Manager ID was found on multiple machines in the same network. This situation is typically caused by cloning a VM. As a result, it was difficult to identify the source of the problem when the licenses on these machine were inaccessible. Now an appropriate error message is generated. |
| LDK-9948 | Rehosting of an SL Legacy key to a different machine would fail with the return code HASP_CLONE_DETECTED. |
| LDK-10273 | Admin Control Center would allow a license to be detached even though the termination date for the detach was invalid. |
| LDK-10564 | The Vendor ID for a Master key was not the same in Admin Control Center pages and in the Diagnostics Reports. |
| LDK-10857 | When an iSCSI disk was connected to a Windows physical machine, the License Manager would regard the machine as a virtual machine. |
| LDK-11478 | After Run-time Environment v.7.32 was installed, running an application that was protected with Sentinel HASP Envelope (prior to Sentinel LDK 6.3) would cause a Stop error (BSoD). |
| LDK-11787 | Under certain circumstances, the Licensing API function hasp_get_info would always return a value of 0 as the value for <updateCounter> for an SL license. Now the function returns the correct value for <updateCounter>. |
| LDK-11825 | Admin Control Center was not able to display an invalid HL key. Now such a key is visible in Admin Control Center with an indication that the key is not valid. |
| LDK-12196 | When an SL key is installed on a machine with Run-time Environment 7.32 or 7.3, the Run-time Environment would continually open additional handles. |
Enhancements in Version 7.32
| Reference | Description |
|---|---|
| LDK-6934 | Sentinel LDK Run-time Environment now supports the Sentinel HL Drive microSD key (patent pending). This key has been tested with the following microSD cards:
|
| LDK-10090 | Run-time Environment is now supported under Windows 10 Technical Preview Build 10041. |
Issues Resolved in Version 7.32
| Reference | Description |
|---|---|
| LDK-9325 | Given the following circumstances:
When the SL key is displayed in Admin Control Center on a second physical machine, the Feature is shown as «disabled». However, a protected application that includes that Feature operates correctly. |
| LDK-8862 | When attempting to access a remote License Manager, Sentinel Admin API would return the incorrect error code SNTL_ADMIN_LM_NOT_FOUND (6002). |
| LDK-7237 | Given the following circumstances:
The Login count for the license would no longer match the number of actual applications active. As part of the resolution for this issue, when the count criteria for a network license is modified, all active sessions are automatically terminated. |
Enhancements in Version 6.65
| Reference | Description |
|---|---|
| LDK-4468 | The template for customizing entries for the Access log in Sentinel License Manager has been enhanced.
In addition, the template is now used for log entries generated by Embedded License Managers and External License Managers. For information on the log template, see the Edit Log Parameters screen and related help screen in Admin Control Center. (Click the Edit Log Parameters button from the Configuration — Basic Settings screen.) |
| LDK-735 | Admin Control Center now enables the user to generate a C2V file without the requirement of installing the RUS utility. This is supported for Windows, Mac and Linux platforms. The following limitations apply:
The C2V file can be generated for locally-connected Sentinel HL, HASP HL, and SL AdminMode keys. |
Issues Resolved in Version 6.65
| Reference | Description |
|---|---|
| LDK-7084 | The hasp_get_info() function in the Licensing API did not return consistent results for localhost when no IP address set in etchosts file for localhost. The function would return either localhost(127.0.0.1) or IPv4. To resolve this issue, the Licensing API must be upgraded to version 7.3 or later and the Run-time Environment must be upgraded to version 6.65 or later. |
| LDK-5710 | When the real-time clock battery in a Sentinel HL (Driverless configuration) keys is exhausted, the error code returned by the hasp_login or hasp_login_scope function was HASP_INT_ERR instead of HASP_NO_BATTERY_POWER. |
| LDK-5390 | If hasplms.exe is locked at the time the user attempts to upgrade the Run-time Environment, a misleading error message was displayed. The error message now provides an appropriate description of the issue. |
| LDK-8895 | When an activated SL-Legacy license is installed on a machine that contains Products that have clone protection disabled, and a user then attempts to detach a license, error 64 (clone detected) was generated. Now a license can be successfully detached. |
| LDK-8936 | Installation of certain third party tools would cause the removal of a symbolic link from Hardlock drivers. As a result, HL keys would become inaccessible. |
Back to Topics
Known Issues — Run-time
Environment
| Reference | Description |
|---|---|
| 12506 | Sentinel LDK communicates via TCP and UDP on port 1947. This port is IANA-registered exclusively for this purpose. At the end user site, the firewall must be configured so that communication via this port is not blocked. |
| 180256 | When a computer names contains UTF-16 characters, Admin Control Center displays the short name for the computer (similar to Windows Explorer). Similarly, the sntl_admin_get function in Admin API returns the short name. |
| 182646 | After Windows 7 is upgraded to Windows 8, the user is not able to use existing SL licenses or to install new SL licenses. Workaround: After you upgrade from Windows 7 to Windows 8, reinstall the Run-time Environment. |
| LDK-2471 | Sentinel Licensing API: On a computer with the Nvidia chip set GeForce 7025/nForce 630a, and where the CPU is AMD Athlon 64 X2, the hasp_read and hasp_encrypt functions may fail with error 39, HASP_BROKEN_SESSION. This problem only exists with HASP HL keys with Firmware version 3.25. Workaround 1: Workaround 2: |
| LDK-8480 | With some new USB chipsets, it is possible that the API hasp_update() call, used to update the firmware of Sentinel HL keys to version 3.25, will generate the HASP_BROKEN_SESSION return code, even if the firmware is correctly updated. (This issue does not occur with Sentinel HL Driverless keys with firmware version 4.x.)
Workaround: Install the latest Run-time Environment. The automatic firmware update feature of the License Manager will automatically update the firmware of the key the first time that the key is connected, without the need to call hasp_update(). |
| LDK-11418 | For a Java 7 or Java 8 application that is protected with Envelope, the end user must use the following flag when launching the protected application:
If the appropriate flag is not specified, the application may throw java.verifyerror when launched. |
| LDK-12145 | When a data file is protected with Version 2 data protection mode for Android platforms: If, for any reason (for example, no license was found), the protected application is not able to decrypt the protected data file, no error message is generated to explain why the file cannot be opened. |
Back to Topics
Copyright
© 2015 SafeNet, Inc. All rights reserved.
DocID 118r Revision 1509-1
Содержание
- Ошибка Unable to access HASP SRM RunTime Environment (H0033)
- Описание проблемы
- Решение
- Сбой при установке драйвера HASP
Ошибка Unable to access HASP SRM RunTime Environment (H0033)
Описание проблемы
При запуске системы выдается ошибка Unable to access HASP SRM RunTime Environment (H0033).
Решение
Способ решения данной проблемы зависит причины ошибки. Для того, что бы ее выявить, необходимо выполнить следующие действия:
- проверить, что C:WINDOWSsystem32hasplms.exe не блокируется Брандмауэром Windows (Windows firewall) или антивирусной программой. В том случае, если Брандмауэр Windows (Windows firewall) включен, то приложение hasplms.exe следует добавить в список исключений.
- проверить, что порт 1947 не блокируется программой Брандмауэр Windows (Windows firewall). В том случае, если Брандмауэр Windows (Windows firewall) включен, то порт 1947 следует добавить в список исключений;
- проверить, что cлужба hasplms (HASP License Manager Service) запущена. Для этого, нужно запустить Диспетчер задач, перейти в нем на вкладку Службы и для службы hasplms посмотреть значение колонки Состояние . В том случае оно обозначено как Остановлено, то следует запустить службу — правой кнопкой мыши кликнуть на ее названии и в контекстном меню выбрать пункт Запустить службу.
- если службу hasplms не удалось запустить с помощью диспетчера задач, тогда следует в командной строке ввести cmd и запустить консоль от имени администратора. В появившемся окне последовательно ввести следующие команды:
- bcdedit -set LOADOPTIONS DISABLE_INTEGRITY_CHECKS
- bcdedit -set TESTSIGNING ON
- выполнить перезагрузку и убедиться что служба hasplms запущена.
- Более подробная информация доступна на форуме Sentinel
Для того, что бы добавить разрешение запуска программы или использования порта в Брандмауэр Windows (Windows firewall) необходимовыполнить следующие действия:
Сбой при установке драйвера HASP
При инсталляции драйвера HASP у моего удаленного клиента происходит ошибка (см. ссылку)
Прошу сообщить почему это происходит ?
Подобная ошибка возможна если на ПК уже был установлен драйвер более старой версии и он ещё используется системой на момент установки нового драйвера (возможно воткнут ключ и драйвер с ним работает).
Воспользуйтесь данной инструкцией для переустановки драйвера:
Инструкция по установке/удалению драйверов (не забываем убедиться что UAC отключен и после его отключения ПК был перезагружен):
1. Отключите все локальные HASP ключи.
2. Убедитесь, что Вы вошли в систему как администратор, если возможно, временно отключите любое защитное ПО (антивирус, брандмауэр).
3. Чтобы убедиться, что не установлено старых версий драйверов, пожалуйста, загрузите драйвер 4.116 по ссылке: http://sentinelcustomer.safenet-inc.com/DownloadNotice.aspx?dID=8589943584
4. Распакуйте загруженный архив на диск и в командной строке перейдите в директорию с файлами из архива.
5. Запустите «hinstall –r –alldrv» для удаления версий, установленных ранее.
6. Если возникли проблемы с удалением – обратитесь к пункту инструкции «ПРОБЛЕМЫ ВО ВРЕМЯ УСТАНОВКИ ДРАЙВЕРА».
Удаляем и затем устанавливаем заново драйвер:
1. Скачиваем свежую версию драйвера (консольную версию драйвера): http://sentinelcustomer.safenet-inc.com/DownloadNotice.aspx?dID=8589947873
2. Не забудьте убедиться что UAC отключен и после его отключения ПК был перезагружен.
3. Отключите все локальные HASP ключи.
4. Убедитесь, что Вы вошли в систему как администратор, если возможно, временно отключите любое защитное ПО (антивирус, брандмауэр).
5. Разархивируйте скачанный драйвер.
6. Выполните из командной строки «haspdinst.exe –fr –kp –purge» для удаления версий установленных ранее.
7. Теперь выполните «haspdinst.exe –i» для установки драйвера.
8. Если возникли проблемы с удалением – обратитесь к пункту инструкции «ПРОБЛЕМЫ ВО ВРЕМЯ УСТАНОВКИ ДРАЙВЕРА».
9. Откройте браузер и перейдите по адресу http://localhost:1947 (утилита Admin Control Center или сокращенно ACC). Проверьте, что ключ отображается на странице «Sentinel Keys».
10. Проверьте, что приложение работает. Если нет:
• Используйте «MsConfig» для остановки все служб, которые не относятся к Microsoft, перезагрузите компьютер и проверьте снова
• В случае отказа системы, пожалуйста, пришлите «дамп памяти ядра», здесь описано как это сделать: http://msdn.microsoft.com/en-us/library/cc266505.aspx
• В случае отказа Менеджера лицензий (License Manager), пожалуйста, пришлите его лог (event log)
• Пришлите скриншот возникающей ошибки
• Удалите «aksdrvsetup.log» в папке c:windows, запустите «haspdinst –i –v», и пришлите созданный файл aksdrvsetup.log
• Запустите «MsInfo32», создайте .NFO log и пришлите его
ПРОБЛЕМЫ ВО ВРЕМЯ УСТАНОВКИ ДРАЙВЕРА
— Удалите все компоненты HASP через «Установка/удаление программ»
— Остановите все службы, которые содержат в названии «Hasp» или «HLServer»
— Удалите все файлы aks*.*, «hardlock.sys» и «haspnt.sys» из папки c:windowssystem32drivers» (если они не используются другими приложениями)
— Изменение драйверов в «Диспетчере устройств»:
o Зайдите в «Панель упаравления»«Система»
o Перейдите на вкладку «Оборудование» и откройте «Диспетчер устройств»
o Выберите в меню «Показать скрытые устройства»
o Раскройте пункт «Драйверы устройств не Plug and Play»
o Удалите каждый из следующих пунктов, если они присутствуют: «Hardlock», «Haspnt», «HASP fridge».
— Попробуйте еще раз удалить драйверы с помощью команды «haspdinst –purge», а затем установить с помощью «haspdinst –i»
Да, «Отключить ключ HASP» — это именно отсоединить его физически от ПК.
Консольная версия позволяет производить установку / удаление драйвера с различными полезными параметрами, GUI версия так не умеет, к тому же, версия 6.63 — уже устарела, сейчас актуальна версия 6.64.
Нет, тип ключа по присланной информации установить нельзя, и в данном случае это ничего не меняет. Ключи HASP HL и HASP 4 отличаются внешне.
Ссылки и есть на сайт SafeNet.
Вот альтернативная ссылка на консольную версию драйвера 6.64: https://yadi.sk/d/QG9PX7SrZxReS
В инструкции даны ссылки на разные версии драйвера.
Опция «-alldrv» доступна именно для старой версии драйвера (4.116 и ниже).
Windows 10 upgrade ‐ “Unable to access Sentinel Run‐time Environment (H0033)” when trying to start Digitizer. This means that the Sentinel LDK License Manager service has stopped, so there is an easy fix for this: Right‐click on the Windows Start button icon located in the bottom left of your computer screen. Choose “Control Panel”.
If you updated Windows to Windows 10, you may get “Unable to access Sentinel Run-time Environment (H0033)” error when starting up e3 software. If this is the case, all you need to do is to reinstall new HASP driver, V7. 32 or later version.
Full
Answer
How to fix “unable to access Sentinel run‐time environment (h0033) ” when trying to start digitizer?
Windows 10 upgrade ‐ “Unable to access Sentinel Run‐time Environment (H0033)” when trying to start Digitizer. This means that the Sentinel LDK License Manager service has stopped, so there is an easy fix for this: Right‐click on the Windows Start button icon located in the bottom left of your computer screen. Choose “Control Panel”.
Why can’t I access HASP SRM run-time environment (h0033)?
When trying to start your application, you get an error dialog showing the message «Unable to access HASP SRM Run-time Environment (H0033)». The error above means that the Sentinel LDK system service is either not started or cannot be reached. A running Sentinel LDK system service is required to run Intella.
What is h0033 error and how to fix it?
«Unable to access Sentinel Run-time environment (H0033)» error occurs when launching e4 software. Solution: It is most likely caused by antivirus software, in particular, Avast or AVG antivirus software.
How to fix Sentinel runtime environment installer failed unable to install?
how to fix Sentinel Runtime Environment installer failed unable to install an inf file 12-13-2016 08:56 AM 12-13-2016 08:56 AM This is usually caused by interference from an anti-virus product. As Administrator, disable your anti-virus product and retry the installation.
What does Unable to access HASP srm Run-time Environment H0033?
When trying to start your application, you get an error dialog showing either «Unable to access HASP SRM Run-time Environment (H0033)» or «No matching feature found (h0050)». The error above means that the Sentinel LDK system service is either not started or cannot be reached.
Sentinel LDK Run-time Environment is a standalone component that enables communication between a Sentinel protection key and Sentinel EMS or a protected application. Each Run-time Environment also contains Sentinel Admin Control Center, a web-based interface for managing licenses.
How do I install Haspdinst?
To install or upgrade the Sentinel LDK Run-time Environment: >Type haspdinst -i in the command line. The installation or upgrade process is performed automatically. A message is displayed informing you that the Sentinel LDK Run-time Environment was successfully installed.
How do I install HASP drivers on Windows 10?
Then Copy the downloaded “haspdinst.EXE” file to “C:HASP” folder ( you need to create a folder of “C:HASP”) Right-click on the Windows “Start” button. In the right-click menu, click on “Command Prompt (Admin)” menu. Click on OK button in the warning message to allow it to run.More items…•
Background
My wife asked me to install her Viking embroidery “5D” software on her Surface Pro PC so she could use the touch tablet and pen to do graphics drawing and editing in the Design Creator.
Solution
I eventually found a post to download the HASP SRM Runtime drivers at https://sentinelcustomer.gemalto.com/sentineldownloads/ (or use the link below). Installing this did solve the H0033 error. Also, once installed, the dongle light was lit and the http://localhost:1947 worked.
Popular Posts:
Содержание
Решение проблем с технологией защиты
-
Если драйвер, поставляемый с установочным диском устарел, то последнюю версию драйвера всегда можно получить на сайте компании SafeNet http://safenet-sentinel.ru/helpdesk/.
HASP LM Server running
Сообшение при установке драйвера ключа защиты Sentinel Hasp:

Уже запущен менеджер лицензий HASP. Это не одно и тоже, что Sentinel HASP.
Решение:
-
Дождитесь, когда пользователи выйдут из баз 1С и прекратят использовать прочие ключи HASP.
-
Остановите службу «HASP Loader».
-
Установите драйвер защиты из дистрибутива МИКО.
Ошибка 48
Установлен «не поддерживаемый» драйвер защиты.
Проблема описана в статье HASP_NO_VLIB
Решение:
-
Удалите используемый драйвер защиты Sentinel HASP.
-
Установите драйвер защиты из дистрибутива МИКО.
Ошибка 42
При подключении панели телефонии может возникать следующая ошибка «Версия менеджера лицензии Sential HASP устарела КОД: 042«
Ошибка означает, что у Вас используется версия панели телефонии, которая не может работать с установленной на данный момент версией драйвера Hasp. Необходимо обновить версию драйвера HASP. Решение представлено в инструкции.
Ошибка H0033
Системное сообщение «Unable to access Sentinel Run-time Environment (H0033)».
Решение:
-
Установите драйвер защиты из дистрибутива МИКО.
-
Откройте обработку 1С повторно.
Ошибка 48 5 718 1275
Эта ошибка может возникать при попытке установки драйвера защиты.
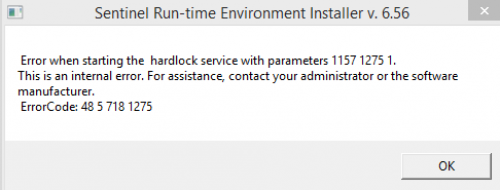
Скорее всего устанавливаемый драйвер защиты устарел. Скачайте актуальный дистрибутив панели телефонии. В каталоге «Protect» находится актуальная версия драйвера для текущего релиза панели телефонии.
ПК не видит сетевой ключ
Если на удаленной машине захватывается тиральный ключ, это значит что ПК не видит лицензий с удаленной машины.
На клиентской машине нужно установить драйвер защиты.
Перейти в браузере в http://localhost:1947
В настройках указать «Aggressive Search for Remote Licenses».
В поле «Specify Search Parameters» указать ip адреса сервера с лицензией.
Адреса вводятся каджый на новой строке.
В http://localhost:1947/_int_/devices.html
должны отобразиться ключи с удаленной машины.
Hasp Key Inactive
Сообщение наблюдается в web интерфейсе localhost:1947, в разделе «Sentinel Keys»:
Сообщение означает, что ключ был отключен. Такое может происходит в случае апгрейда ключа до большего числа лицензий. В таком случае необходимо активировать дополнительный «.v2c» файл.
В личном кабинете будет два ключа защиты:
-
Основной ключ
-
Ключ апгрейда на более емкий.
Для случая переустановки ОС следует активировать ключи последовательно.
Комментарии
Problem:
В процессе установки драйвера Sentinel HASP возникает ошибка Unable to start/stop hardlock service with parameters…
В процессе установки драйвера Sentinel HASP возникает ошибка вида Error Code: 48 X YYY ZZZZ
Solution:
ВНИМАНИЕ! Перед тем, как выполнять рекомендации, приведенные в этой статье, остановите антивирус и брандмауэр, отключите UAC и DEP, если перечисленные компоненты и ПО установлены и запущены на Вашем компьютере, или попросите Вашего системного администратора сделать это. В процессе выполнения рекомендаций Вам понадобится перезагрузить компьютер. После каждой перезагрузки проверяйте, что антивирус не запустился снова (если запустился — снова остановите его).
ВНИМАНИЕ! Для выполнения действий Вам потребуется работа в командной строке. Чтобы открыть окно командной строки
- на OC Windows XP выберите Пуск — Все программы — Стандартные — Командная строка
- на ОС Windows 7 выберите Пуск — Все программы — Стандартные, на пункте Командная строка нажмите правую клавишу и выберите Запуск от имени администратора
- на ОС Windows 8 и 8.1 в окне Проводника Windows (в любом каталоге) выберите Файл — Открыть командную строку — Открыть командную строку как администратор
Изначально выполните пункты исключая пункт номер 7. Если это не принесло результатов то повторите выполнение переустановки включая пункт 7.
Для устранения проблемы необходимо выполнить следующие действия в строгой последовательности:
- остановите все приложения, которые используют в работе ключи Sentinel и HASP (всех модификаций), а затем отсоедините все usb-ключи Sentinel и HASP
- остановите службу Sentinel LDK License Manager* в оснастке Службы Windows или выполните в командной строке net stop hasplms
- остановите службу HASP Loader в оснастке Службы Windows (если есть)
- скачайте актуальный драйвер Sentinel HASP (HASP SRM) здесь, распакуйте архив в любом месте на компьютере и перетащите файл в окно командной строки (или выполните в командной строке cd <путь к каталогу с файлом драйвера>, например, cd C:haspdinst)
- удалите установленный драйвер Sentinel HASP (HASP SRM) выполнив в командной строке haspdinst -fr -purge
- перезагрузите компьютер
-
установите актуальный драйвер, выполнив в командной строке haspdinst -i
Если ошибка снова возникла, выполните удаление драйвера как описано выше, затем перезагрузите компьютер и перейдите к рекомендациям из пункта 8.
-
откройте Диспетчер устройств Windows (Компьютер — Свойства — Диспетчер устройств) и отобразите скрытые устройства (Вид — Показать скрытые устройства). Если в ветке Драйверы несамонастраиваемых устройств есть устройство hardlock, то удалите его:
-
удалите папки
- C:Program FilesAladdin (C:Program Files (x86)Aladdin для 64-разрядных ОС)
- C:WindowsSetupAladdin
- удалите из папки C:WindowsSystem32DriverStoreFileRepository все файлы, название которых начинается с aks
-
удалите из папки C:WindowsSystem32Drivers файлы
- hardlock.sys
- aksfridge.sys
- akshasp.sys
- aksclass.sys
- aksusb.sys
- удалите файл hasplms.exe из папки C:WindowsSystem32
- удалите из системного реестра ветку HKEY_CURRENT_USERSoftwareAladdin Knowledge Systems
-
выполните в реестре поиск и удаление всех веток, в названии имени или параметра которых есть слова hasplms или hardlock:
- перезагрузите компьютер
- установите драйвер Sentinel HASP (HASP SRM), выполнив в окне командной строки haspdinst -i -fi -kp -fss
-
перезагрузите компьютер и убедитесь, что драйвер успешно установился и запустился:
- в процессах есть hasplms.exe
- в браузере открывается утилита Admin Control Center
* в прежних версиях драйвера служба может называться HASP License Manager или Sentinel HASP License Manager или Sentinel Local License Manager