This article, suggests a way of resolving the below error message, when you are trying to access SQL Server using “Microsoft OLE DB Provider for SQL Server” and TLS 1.0: [DBNETLIB] [ConnectionOpen (SECDoClientHandshake()).] SSL Security Error
Prior to start writing this article, I was thinking of using a title like “How to still use TLS 1.0”, or something similar, but besides the fact that would have given a wrong message, it would not help so much because many people, usually search for such articles using the error message (SSL Security error)…
So, I anticipate that this article, with this title, would help as many people as possible 🙂
Drop me a line if you find the article useful and why not, subscribe to my newsletter to stay up to date with future articles!
A Few Words About TLS 1.0
TLS 1.0 is considered a deprecated protocol and it is not recommended anymore to be used to secure connections. That’s why many organizations (if not all) transitioned or are in the process of transitioning to newer versions of TLS such as TLS1.1 or above.
However, you may still encounter outdated applications that still need to use this protocol, even for a while for just performing a single operation. One such example, is to try and connect to a SQL Server instance via Microsoft OLE DB Driver for SQL Server using TLS 1.0.
If you are in such situation, I have good news, from a technical aspect, it is still possible to do this.
Read on to learn more.
SQL Server Support for TLS 1.0 and Above
SQL Server still supports all TLS protocols, currently from 1.0 to 1.2. However, depending on the version of SQL Server you have, especially in cases of older SQL Server versions, you might need a patch.
Read this article on SQLNetHub to learn more about SQL Server support for TLS versions.
Now let’s jump to the juicy part of this article and see how finally we can resolve the above error and manage to connect to SQL Server using Microsoft OLE DB Driver for SQL Server and TLS 1.0.
Note that if you are just trying to connect with TLS 1.0 for a while in order to perform a specific task, then make sure to revert the below changes in order to restore the security level of your systems back to their previous level.
Latest Microsoft OLE DB Driver for SQL Server
The first step towards resolving the SSL Security error, is to make sure that the version of the target SQL Server instance you want to connect to, is supported by the driver.
For example, Microsoft OLE DB Driver 18.1 for SQL Server supports connecting to SQL Server 2012 or later.
For older versions of SQL Server, you will need to find an earlier version of Microsoft OLE DB Provider for SQL Server as well.
You can find the latest version of the OLE DB driver here.
Useful details:
The Microsoft OLE DB Provider for SQL Server, allows ADO to access Microsoft SQL Server. However, This is an older driver and it is not recommended to be used driver for new development, since it is deprecated.
The new OLE DB provider is called the Microsoft OLE DB Driver for SQL Server (MSOLEDBSQL) which will be updated with the most recent server features going forward (learn more)
Registry Changes
The next step is, to edit the Windows Registry (* always be careful when messing up with Windows Registry – only certified engineers should do that).
To enable TLS 1.0 in Windows
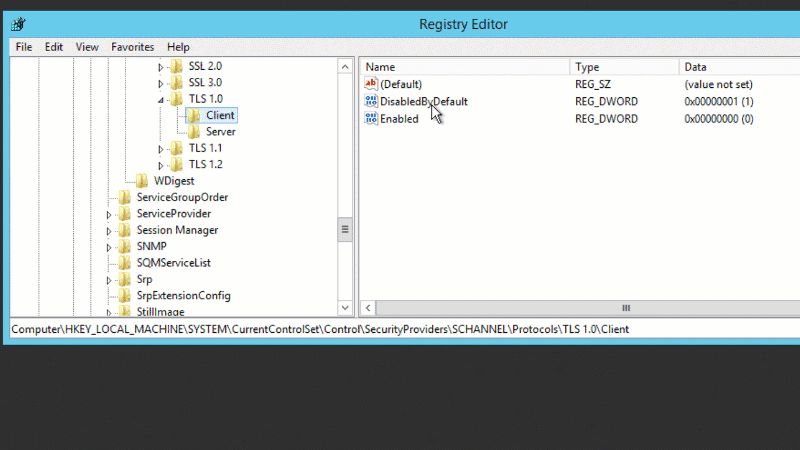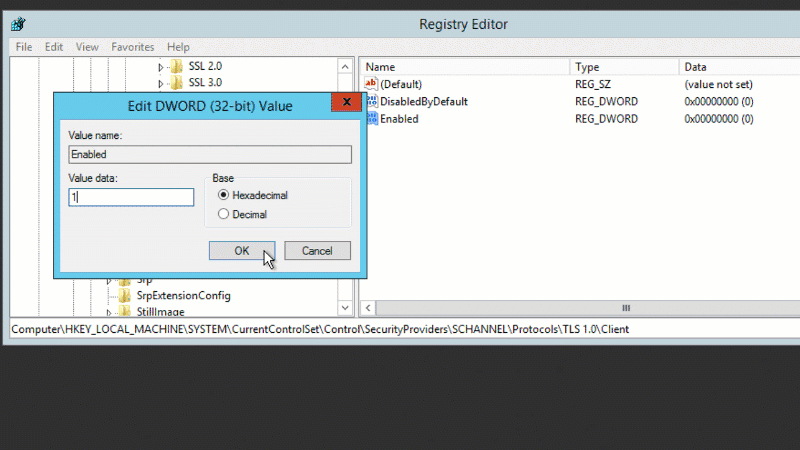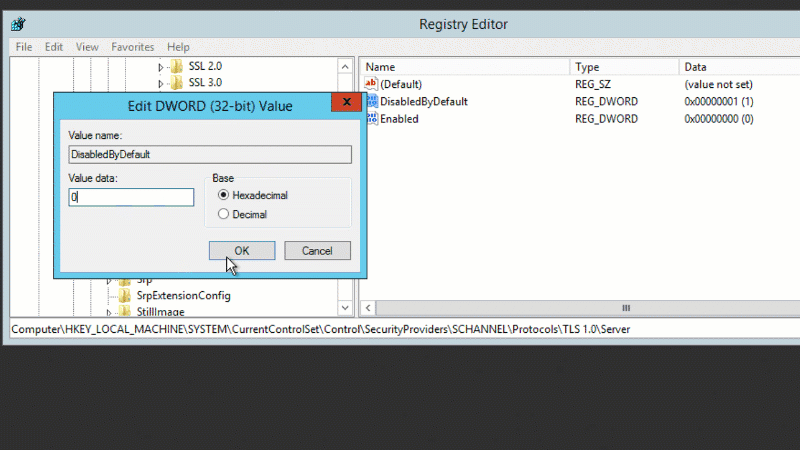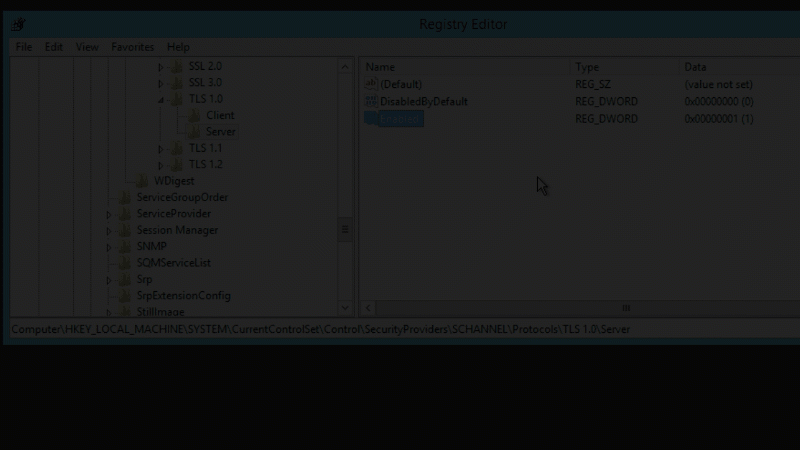
In Windows Registry, add the below dword keys:
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server]
- “Enabled”=dword:00000001
- “DisabledByDefault”=dword:00000000
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Client]
- “Enabled”=dword:00000001
- “DisabledByDefault”=dword:00000000
To disable TLS 1.0 in Windows
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
[HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client]
- “Enabled”=dword:00000000
- “DisabledByDefault”=dword:00000001
Learn more about the above registry changes in this MS Docs article.
Local Security Policy
The next step is to check the Local Security Policy on the database server.
So, in Local Security Policy on the Database Server, make sure that the setting “System Cryptography: Use FIPS compliant algorithms for encryption, hashing, and signing” is disabled.
If you want to learn more about this security option, you can check this MS Docs article.
Strengthen your SQL Server Administration Skills – Enroll to our Online Course!
Check our online course on Udemy titled “Essential SQL Server Administration Tips”
(special limited-time discount included in link).Via the course, you will learn essential hands-on SQL Server Administration tips on SQL Server maintenance, security, performance, integration, error handling and more. Many live demonstrations and downloadable resources included!
(Lifetime Access/ Live Demos / Downloadable Resources and more!) Enroll from $12.99
Server Protocols, Ciphers, Hashes and Client Protocols
The last step in this troubleshooting guide, is to use IISCrypto, which is an excellent free tool, that allows you to control which protocols, ciphers, and more are enabled (or not) on a Windows server.
That being set, you will need to run IISCrypto and make sure that the “TLS 1.0” Server and Client Protocols, as well as the”SHA” hash are enabled.
Here’s a screenshot of IISCrypto, running on my PC, having TLS 1.0 and “SHA” enabled for illustration purposes:
Note that, if finally you need to perform any changes using IISCrypto, you will need to restart the server.
Actually, for any changes you might need to perform, it is recommended to restart the server.
A Piece of Advice
As mentioned in this article’s beginning, TLS 1.0 is considered a deprecated protocol and it is not recommended anymore to be used to secure connections.
Instead, you should be using newer versions of TLS.
In case you just need to switch to TLS 1.0 for performing an ad hoc task, you need to make sure that after you completed the task, you revoked any changes you might have applied, and disable again TLS 1.0 and the “SHA” hash.
See More
Check out DBA Security Advisor, a SQL Server security tool to assess your SQL Server instances against a rich set of security checks and get security best practice recommendations.
Featured Online Courses:
- SQL Server 2022: What’s New – New and Enhanced Features
- Data Management for Beginners – Main Principles
- Introduction to Azure Database for MySQL
- Working with Python on Windows and SQL Server Databases
- Boost SQL Server Database Performance with In-Memory OLTP
- Introduction to Azure SQL Database for Beginners
- Essential SQL Server Administration Tips
- SQL Server Fundamentals – SQL Database for Beginners
- Essential SQL Server Development Tips for SQL Developers
- Introduction to Computer Programming for Beginners
- .NET Programming for Beginners – Windows Forms with C#
- SQL Server 2019: What’s New – New and Enhanced Features
- Entity Framework: Getting Started – Complete Beginners Guide
- A Guide on How to Start and Monetize a Successful Blog
- Data Management for Beginners – Main Principles
Read Also
- DBA Security Advisor v2.3 is Now Out!
- The OLE DB provider “SQLNCLI11” for linked server “…” supplied inconsistent metadata for a column… – How to Resolve
- SQL Server 2022: What’s New – New and Enhanced Features (Course Preview)
- How to Connect to SQL Server Databases from a Python Program
- What is Data Security and which are its Main Characteristics?
- Introduction to Azure Database for MySQL (Course Preview)
- Data Management for Beginners – Main Principles (Course Preview)
- Advanced SQL Server Features and Techniques for Experienced DBAs
- SQL Server Database Backup and Recovery Guide
Other SQL Server Security-Related Articles
- How to Enable SSL Certificate-Based Encryption on a SQL Server Failover Cluster
- Why You Need to Secure Your SQL Server Instances
- Policy-Based Management in SQL Server
- Advanced SQL Server Features and Techniques for Experienced DBAs
- Should Windows “Built-InAdministrators” Group be SQL Server SysAdmins?
- Frequent Password Expiration: Time to Revise it?
- The “Public” Database Role in SQL Server
- Encrypting SQL Server Databases
- 10 Facts About SQL Server Transparent Data Encryption
- Encrypting a SQL Server Database Backup
- …check all
Subscribe to our newsletter and stay up to date!
Subscribe to our YouTube channel (SQLNetHub TV)
Easily generate snippets with Snippets Generator!
Secure your databases using DBA Security Advisor!
Generate dynamic T-SQL scripts with Dynamic SQL Generator!
Check our latest software releases!
Check our eBooks!
Rate this article: 
Loading…
Reference: SQLNetHub.com (https://www.sqlnethub.com)
© SQLNetHub
Artemakis Artemiou is a Senior SQL Server Architect, Author, a 9 Times Microsoft Data Platform MVP (2009-2018). He has over 20 years of experience in the IT industry in various roles. Artemakis is the founder of SQLNetHub and {essentialDevTips.com}. Artemakis is the creator of the well-known software tools Snippets Generator and DBA Security Advisor. Also, he is the author of many eBooks on SQL Server. Artemakis currently serves as the President of the Cyprus .NET User Group (CDNUG) and the International .NET Association Country Leader for Cyprus (INETA). Moreover, Artemakis teaches on Udemy, you can check his courses here.
Views: 24,707
Tasks using ‘Microsoft OLE DB Provider for SQL Server’ are failing with the following error:
Possible Error 1:
Error: Connector connect error: ErrorSource: Microsoft OLE DB Provider for SQL Server, ErrorMsg: [DBNETLIB][ConnectionOpen (SECCreateCredentials()).]SSL Security error.
Possible Error 2:
ErrorMsg: [DBNETLIB][ConnectionOpen (SECDoClientHandshake()).]SSL Security error.
Environment:
- All QlikView versions
- All Qlik Sense versions
Resolution:
The source and destination servers do not have aligned TLS versions enabled.
For example, if the data source only has TLS 1.0 enabled, while the Qlik product is installed on a Windows 2016 machine that disallows 1.0 and uses either TLS 1.1 or TLS 1.2, then the data source needs to be upgraded to support TLS 1.1 or TLS 1.2, or the security protocols need to be aligned.
In this example, the currently deployed Microsoft OLE DEB Providers for SQL do not support TLS 1.2 yet.
Please verify what version you have installed and confirm if you need to upgrade your data source: https://support.microsoft.com/en-us/kb/3135244
Recommended Fix:
Upgrade your data source so that the TLS versions between the data source and Qlik Sense or QlikView server match.
Alternative Fix:
Align the TLS versions used. Note that the example we use here configures TLS 1.0. We do not recommend the use of TLS 1.0, it is simply used for demonstration purposes.
If the registry keys are not present, the script under the following article should add them leaving only TLS 1.2 enabled TLS and SSL Support in Qlik Sense: How to configure Qlik Sense and TLS . Then TLS 1.0 may be enabled as mentioned below.
TLS 1.0 can be enabled with the following registry changes:
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server] «Enabled»=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Server] «DisabledByDefault»=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Client] «Enabled»=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.0Client] «DisabledByDefault»=dword:00000000
If the organization policy requires TLS 1.1 to be disabled, this can be done after the installation completes:
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server] «Enabled»=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Server] «DisabledByDefault»=dword:00000001
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client] «Enabled»=dword:00000000
- [HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlSecurityProvidersSCHANNELProtocolsTLS 1.1Client] «DisabledByDefault»=dword:00000001
Related Content:
- TLS and SSL Support in Qlik Sense: How to configure Qlik Sense and TLS
YouTube Video (Better Quality)
I was approached with a case where the customer was trying to create a Data Source within the Power BI Admin Center and received the following error when trying to test the connection and having Encrypt Connection selected.
Artemakis Artemiou is a Senior SQL Server Architect, Author, a 9 Times Microsoft Data Platform MVP (2009-2018). He has over 20 years of experience in the IT industry in various roles. Artemakis is the founder of SQLNetHub and {essentialDevTips.com}. Artemakis is the creator of the well-known software tools Snippets Generator and DBA Security Advisor. Also, he is the author of many eBooks on SQL Server. Artemakis currently serves as the President of the Cyprus .NET User Group (CDNUG) and the International .NET Association Country Leader for Cyprus (INETA). Moreover, Artemakis teaches on Udemy, you can check his courses here.
Views: 24,707


![[DBNETLIB] [ConnectionOpen (SECDoClientHandshake()).] SSL Security Error - How to Resolve - Article on SQLNetHub [DBNETLIB] [ConnectionOpen (SECDoClientHandshake()).] SSL Security Error - How to Resolve - Article on SQLNetHub](https://www.sqlnethub.com/wp-content/uploads/2019/02/IISCrypto-Example-SQLNetHub-SSL-Security-Error-Article.png)